Table Of Contents
Understanding Vulnerability and CVE
In the rapidly evolving world of cybersecurity, understanding vulnerabilities and how they are assessed is crucial. With threats becoming more sophisticated, it’s essential to have a structured method for evaluating and prioritizing these vulnerabilities. One of the key frameworks used for this purpose is the Common Vulnerability Scoring System (CVSS), maintained by the CVSS Special Interest Group (CVSS SIG). This blog post delves into what vulnerabilities and Common Vulnerabilities and Exposures (CVE) are and how CVSS helps in assessing their severity.
What is a Vulnerability?
Vulnerability in cybersecurity means a weakness or flaw in a system that bad actors can exploit to gain unauthorized access, cause damage, or disrupt services. Vulnerabilities can exist in software, hardware, or network configurations. They often arise from coding errors, misconfigurations, or design flaws. For instance, a software vulnerability might allow an attacker to execute arbitrary code, while a hardware vulnerability could enable a bad actor to bypass security controls.
Understanding CVE
Common Vulnerabilities and Exposures (CVE) is a system that supplies a reference method for publicly known information-security vulnerabilities and exposures. Each CVE entry is a unique identifier for a specific vulnerability or exposure, making it easier to share data across different tools and databases.
For example, CVE-2023-12345 refers to a specific vulnerability in a widely used software product. The CVE entry includes a brief description of the affected products and sometimes a link to more detailed information or patches.
The Role of CVSS in Vulnerability Assessment
The Common Vulnerability Scoring System (CVSS) is a framework used to assess the severity of vulnerabilities. It provides a standardized method for rating the impact of a vulnerability and helps organizations prioritize their remediation efforts.
What is CVSS v4.0?
CVSS, originally developed in 2005 and updated over time, is a framework for rating the severity of security vulnerabilities. The latest version, CVSS v4.0, represents a substantial revision from its predecessors. It builds upon the previous versions, incorporating feedback from the cybersecurity community and adapting to the modern threat landscape.
Key Changes in CVSS v4.0
1. Improved Precision with New Metrics
CVSS v4.0 introduces new metrics and refinements to existing ones, enhancing the precision of the scoring system. Notable changes include:
- Attack Scope (AS): A new metric that helps determine whether the impact of a vulnerability is contained within the vulnerable component or affects other components. This allows for a more nuanced understanding of the potential spread and impact of an exploit.
- Privileges Required (PR) Adjustment: The revised metric now offers more granularity in assessing the level of privileges needed to exploit a vulnerability.
2. Expanded Temporal Metrics
The Temporal metrics in CVSS v4.0 have been expanded to better reflect the evolving nature of vulnerabilities over time. The updated metrics provide more detailed information about:
- Exploit Code Maturity (E): The maturity of exploit techniques, now with additional classifications to reflect different stages of exploit development.
- Remediation Level (RL): A new classification system to better describe the availability and effectiveness of remediation.
3. Enhanced Environmental Metrics
CVSS v4.0 improves the Environmental metrics to allow for more precise tailoring of the CVSS score based on the specific environment:
- Security Requirements (CR, IR, AR): These metrics now better reflect the importance of Confidentiality, Integrity, and Availability in the given context, allowing organizations to adjust the base score according to their unique security requirements.
4. Usability and Clarity
The new version emphasizes usability and clarity. Changes to the metric definitions and scoring algorithms aim to reduce ambiguity and make the scoring process more straightforward for users. This includes clearer definitions and more intuitive scoring guidelines.
How CVSS v4.0 Enhances Vulnerability Management
The enhancements in CVSS v4.0 provide several benefits to organizations:
- More Accurate Risk Assessment: With refined metrics and improved granularity, CVSS v4.0 enables a more accurate assessment of the potential impact and likelihood of vulnerabilities being exploited. This helps in prioritizing remediation efforts more effectively.
- Better Contextualization: The updated Environmental metrics allow organizations to adjust scores based on their specific context, providing a more tailored view of risk that aligns with their unique security posture and requirements.
- Improved Decision-Making: The increased precision and clarity in CVSS v4.0 facilitate better decision-making by providing a more detailed and accurate picture of vulnerability severity.
Getting Started with CVSS v4.0
To start using CVSS v4.0, you can refer to the official CVSS v4.0 Specification, which provides comprehensive details on the new metrics, scoring guidelines, and calculation methods. The specification includes a detailed description of each metric and examples to guide users in applying CVSS v4.0 effectively.
Understand the Metric Groups
CVSS is organized into four main metric groups as follows:
- Base Metrics: Fundamental characteristics of the vulnerability.
- Threat Metrics: The likelihood of exploitation and the effectiveness of available remediations.
- Environmental Metrics: Adjustments based on the specific environment.
- Supplemental metrics: Additional insights that complement the main metrics but do not affect the CVSS score directly.
1. Base Metrics Calculation
The Base Metrics form the core of the CVSS score and are divided into:
Exploitability Metrics
- Attack Scope (AS): Whether the vulnerability’s impact is contained within the vulnerable component or affects other components. Values: Unchanged (no impact beyond the vulnerable component), changed (impact extends beyond the vulnerable component)
- Attack Vector (AV): The method by which the vulnerability is exploited. Values:
Network (exploitable remotely), Adjacent Network (requires close network proximity), Local (requires local access), Physical (requires physical interaction)
- Attack Complexity (AC): Conditions required to exploit the vulnerability. Values:
Low (easy to exploit), High (difficult to exploit)
- Privileges Required (PR): The level of privileges needed to exploit the vulnerability. Values:
None (no privileges needed), Low (low privileges required), High (high privileges required)
- User Interaction (UI): Whether exploitation requires user interaction. Values: None (no user interaction required), Required (user interaction required)
Impact Metrics
- Confidentiality Impact (C): Impact on the confidentiality of information. Values: None (no impact), Low (some impact), High (complete loss)
- Integrity Impact (I): Impact on the integrity of the system. Values: None (no impact), Low (some impact), High (complete loss)
- Availability Impact (A): Impact on the availability of the system. Values: None (no impact), Low (partial loss), High (complete loss)
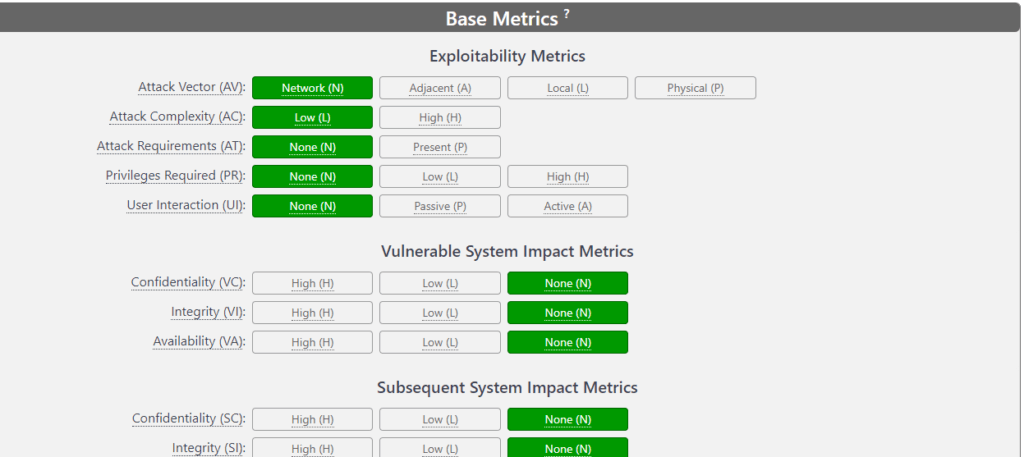
2. Threat Metrics
Threat Metrics are designed to capture factors related to the threat landscape that influence the likelihood of exploitation and the potential effectiveness of remediation. While not part of the traditional CVSS framework, these metrics provide additional context for understanding threats.
- Exploitability Impact (EI): Assesses the real-world impact of the exploit based on practical scenarios.
- Exploitability Attack Vector (AV): Provides specific details about the method of attack, such as social engineering or specific attack vectors.
- Exploitability Techniques (ET): Details the techniques used by attackers to exploit the vulnerability, including known exploit techniques and methods.
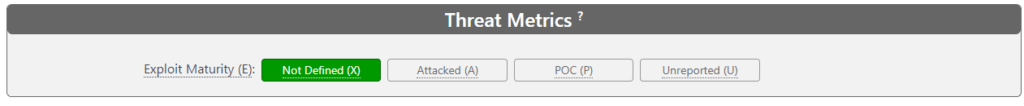
3. Environmental Metrics
Environmental Metrics adjust the CVSS score based on the specific context of the organization. These metrics allow organizations to tailor the CVSS score to their unique environment and risk profile.
- Modified Base Metrics: Adjustments to the Base Metrics based on the organization’s environment and configuration.
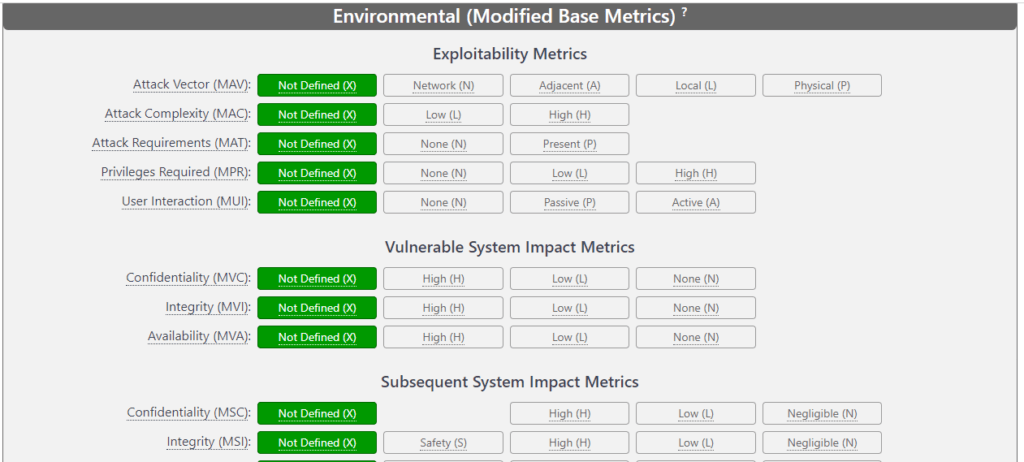
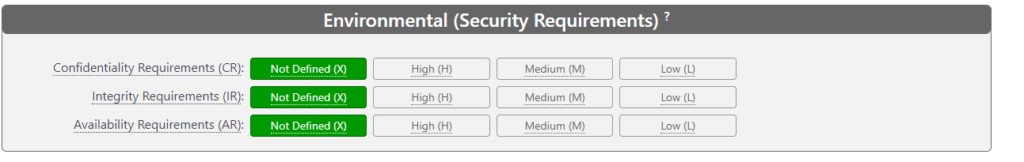
- Security Requirements (CR, IR, AR): Reflect on how crucial are Confidentiality Integrity and Availability to the organization. Value: Low (Security requirement is not critical), Medium (Security requirement is important but not critical), High (Security requirement is crucial).
4. Supplemental Metrics
Supplemental Metrics provide additional context and details that complement the Base, Threat, and Environmental metrics. While not directly contributing to the CVSS score, these metrics supply valuable insights into various aspects of the vulnerability.
- Remediation Complexity (RC): Evaluates the difficulty involved in applying patches or fixes.
- Remediation Effectiveness (RE): Assesses how effective the available remediation is in mitigating the vulnerability.
- Operational Impact (OI): Measures the broader operational impact of the vulnerability, including disruptions to business operations and customer experience.
- Data Sensitivity (DS): Assesses the sensitivity of the data potentially exposed by the vulnerability.
Steps to Calculate CVSS Score
- Start with Base Metrics: Determine the inherent severity of the vulnerability using the Base Metrics, which ranges from 0 to 10. The formula takes into account the Exploitability and Impact metrics.
- Incorporate Threat Metrics: Apply Threat Metrics to understand the likelihood and impact of exploitation in practical scenarios.
- Adjust with Environmental Metrics: Tailor the CVSS score based on your organization’s specific environment and security requirements.
- Use Supplemental Metrics for Context: Consider additional details provided by Supplemental Metrics to gain a comprehensive understanding of the vulnerability’s implications.
Example Calculation
Suppose a vulnerability has the following Base metric values:
- Attack Vector (AV): Network
- Attack Complexity (AC): Low
- Privileges Required (PR): None
- User Interaction (UI): None
- Confidentiality (C): High
- Integrity (I): High
- Availability (A): Low
The CVSS string will look like this: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:L/SC:N/SI:N/SA:N
Let’s input the above values using the online CVSS calculator, as shown in the screenshot below.
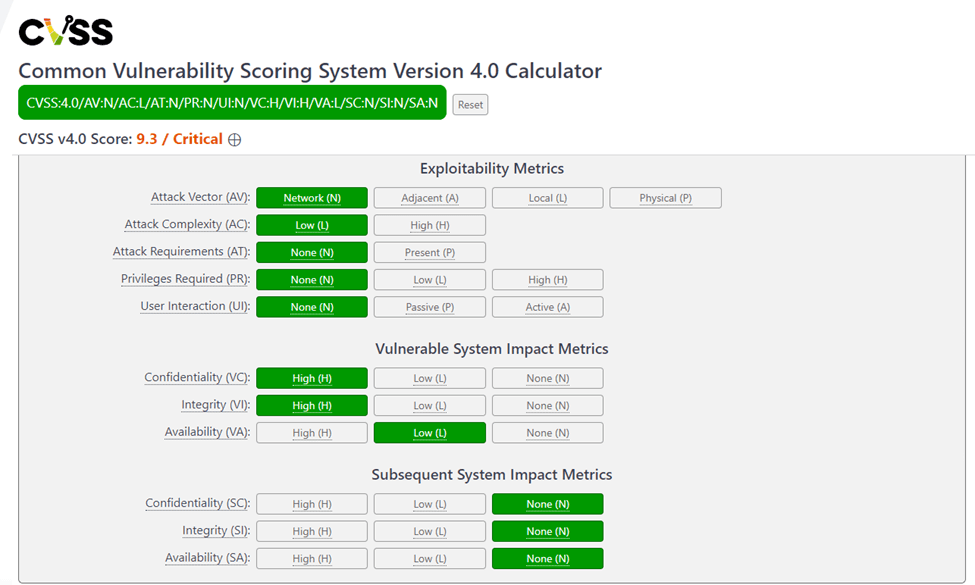
Then, you would adjust this score using Base, Threat, Environmental, and Supplemental metrics if applicable. We will leave the Threat, Environmental, and Supplemental metrics as default for this example. The CVSS score is 9.3, which is Critical.
Conclusion
Understanding vulnerabilities, CVEs, and the CVSS framework is essential for effective cybersecurity management. By leveraging CVSS, organizations can systematically assess and prioritize vulnerabilities, enabling them to respond more effectively to potential threats. As the cybersecurity landscape evolves, staying informed about these tools and frameworks will be crucial in maintaining robust security postures.
For more detailed information on CVSS and how to interpret scores, you can visit the official CVSS SIG website below.
Reference
Common Vulnerability Scoring System SIG
