Table Of Contents
- 1 Investigate a Malware Incident in Microsoft Sentinel Using NIST SP 800-61
- 2 Understanding NIST SP 800-61
- 3 Prerequisites for Using Microsoft Sentinel
- 4 Step-by-Step Malware Incident Investigation in Microsoft Sentinel
- 5 1. Detection and Analysis
- 6 Visually investigate your incidents with the Investigation Graph
- 7 2. Containment, Eradication, and Recovery
- 8 Lessons Learned
- 9 How to Handle False Positives in Malware Detection
- 10 Conclusion
- 11 About The Author
Investigate a Malware Incident in Microsoft Sentinel Using NIST SP 800-61
Malware incidents can have serious consequences for your organization’s security and data integrity. Detecting, investigating, and responding to malware effectively is critical to mitigating damage and preventing future attacks. Microsoft Sentinel, a cloud-native SIEM (Security Information and Event Management) platform, can help automate much of the detection and investigation process. By aligning with NIST SP 800-61, which provides guidelines for handling security incidents, organizations can ensure they are following best practices throughout the investigation. In this post, I will guide you through the step-by-step process of investigating a malware incident in Microsoft Sentinel, from detection to recovery. I will also discuss how to handle false positives during the investigation process.
Understanding NIST SP 800-61
NIST SP 800-61 is the National Institute of Standards and Technology’s guide for handling computer security incidents. It provides an organized approach to incident management and is divided into four main phases:
- Preparation: Ensuring that your organization has the right tools, processes, and teams in place to handle incidents.
- Detection and Analysis: Identifying and analyzing potential security incidents, such as malware infections.
- Containment, Eradication, and Recovery: Isolating the threat, eliminating it, and restoring affected systems.
- Post-Incident Activity: Analyzing the incident to improve future responses and prevent similar attacks.
These steps help structure an investigation process, ensuring a consistent, thorough approach. By following the steps, you can investigate and respond to a malware incident methodically, reducing the impact on your organization and improving your incident response capabilities over time.
Prerequisites for Using Microsoft Sentinel
Before diving into the investigation process, ensure the following prerequisites are in place:
- Microsoft Sentinel Subscription: You need an active Microsoft Sentinel subscription to access its SIEM capabilities.
- Data Connectors: Set up data connectors to bring in logs from various data sources, such as Azure Active Directory, firewall logs, endpoint security tools, and antivirus solutions.
- Detection Rules: Microsoft Sentinel comes with built-in detection rules, but you can also customize them to detect malware-related activities, such as unusual file activity, suspicious network traffic, or the presence of known malware signatures.
- KQL Skills: Understanding Kusto Query Language (KQL) is essential for querying and analyzing log data within Sentinel.
- Playbooks: Consider using Microsoft Sentinel Playbooks to automate responses like isolating infected devices or sending alerts to relevant teams.
Step-by-Step Malware Incident Investigation in Microsoft Sentinel
1. Detection and Analysis
NIST SP 800-61 Reference: Detection and Analysis phase, where you identify suspicious activity and confirm whether it is indeed a malware incident.
The first step in investigating a malware incident is detection and identification. This is where Microsoft Sentinel excels, helping you quickly identify potential malware infections through pre-configured alerts or custom detection rules. Check the Microsoft Sentinel Dashboard for Incidents and for alerts indicating malware-related activities, such as:
- Detection of malware by endpoint protection tools integrated with Sentinel
- Unexpected file execution or network activity
- Presence of known malicious IP addresses or URLs
For this example, Microsoft Defender for Endpoint is integrated with Microsoft Sentinel. So, I will be working on the incidents detected by the Defender for Endpoint.
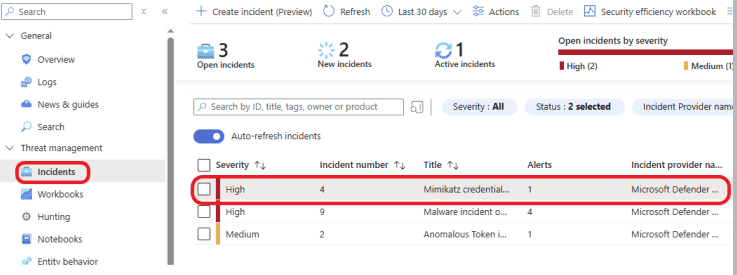
In your Sentinel Workspace, click on Incidents under Threat management on the left navigation pane. Here, we have 3 incidents. Two High-severity incidents and one Medium-severity incident, as shown in the screenshot below.
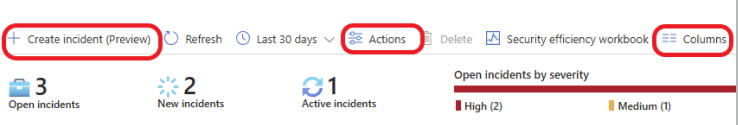
Create Incident (Preview): This option allows you to create a new incident and begin the investigation process, which can be very useful during threat hunting.
Column Tab: The column tab organizes and displays different pieces of information or filters, making it easier to manage and view incident data in a structured way. You can filter based on information that is important to you.
Date and Time range: The date and time range allows you to filter incidents based on a specific period. You can select one of the times available or click on custom range to select a start and end date and time to narrow down the information to the relevant timeframe for your investigation or analysis.
Actions: This section displays the available actions you can take, such as changing the incident Severity, assigning the Owner, and updating the incident Status.
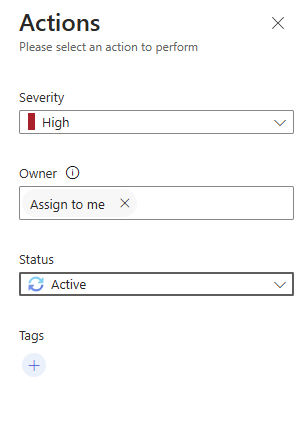
You can assign the incident to an analyst or to yourself. Click on the incident and click on the Actions tab. Here, you can change the incident Severity, assign an Owner, and update the incident Status. Select your name under Owner to assign the incident to yourself, then select Active under Status to change the status to active. Click on Apply to apply the changes.
Click on View full detail on the lower right side to learn more about the incident.
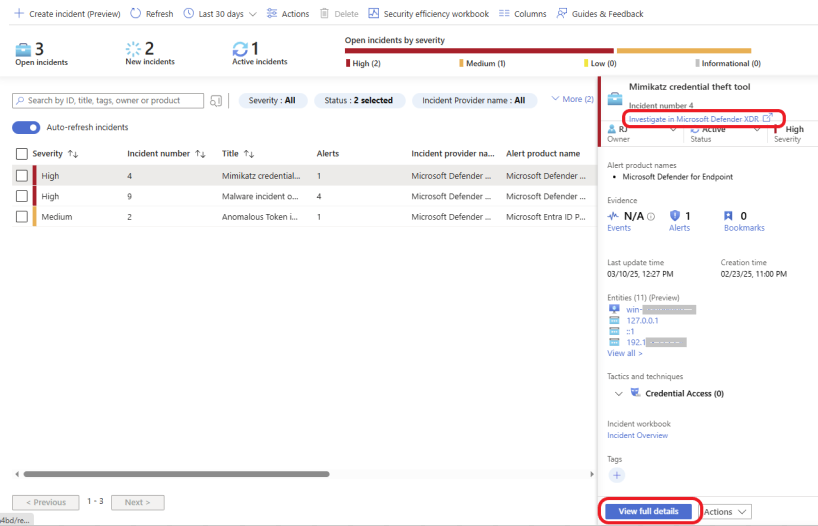
The Timeline tab gives basic information about the incident. Click on the Similar Incidents tab to see incidents from the past that are similar to the one you are working on.
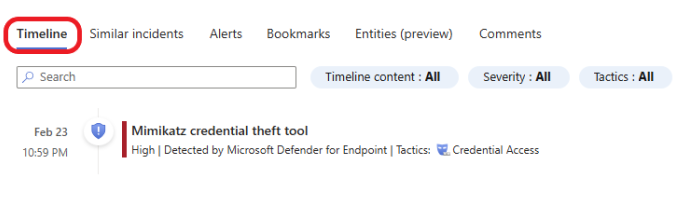
Click on the Entities (preview) tab to gather information about the entities involved.
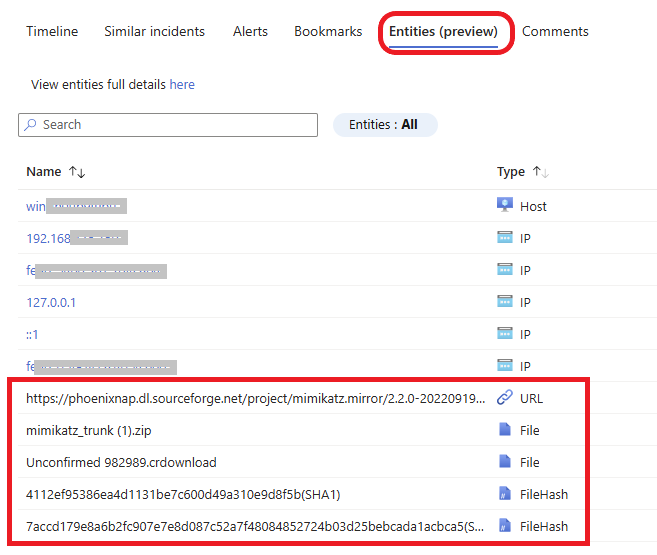
Some information about the incident is provided on the right side. Click on the link provided to read about the identified malware.
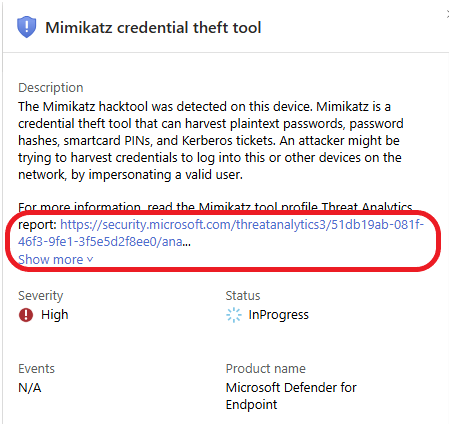
Scroll down and read the Remediation steps.
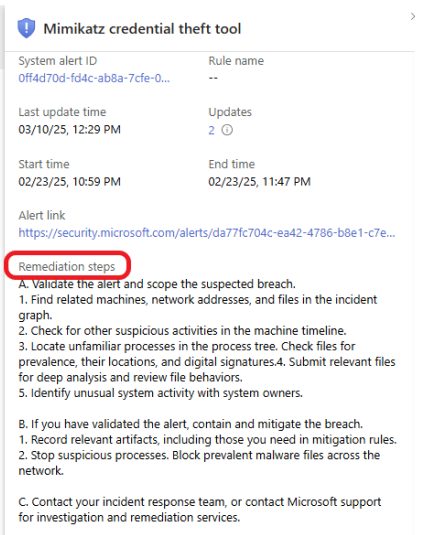
Click on Investigate on the bottom left to learn more about the incident.
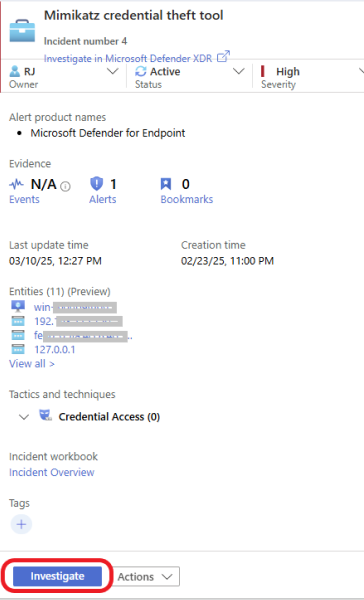
Visually investigate your incidents with the Investigation Graph
Investigation Graph helps you see how entities and activities are connected in a clear, visual format. You can track relationships between different elements to better understand the incident.
The Entities widget displays all the entities identified in the incident, such as affected users, devices, IP addresses, potentially malicious files, or more.
Here, you will get information about the incident. Including the endpoint and the affected end user, how the malware got in, the type of malware, and more. Click on each entity for more information.
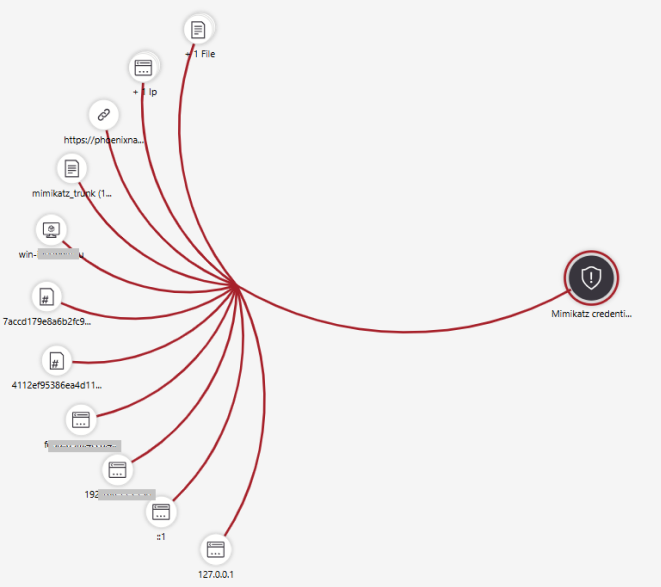
Click on Entities. Here, you can see the infected device name, IP address, file name, file hashes, and the URL. The name of the file detected as malicious is mimikatz-master (5).zip.
Mimikatz is a popular open-source tool used for post-exploitation tasks in cybersecurity. It allows attackers (or penetration testers) to extract sensitive information from Windows systems, such as:
- Passwords (in plain text)
- Hashes (password hashes)
- Kerberos tickets
While it’s often used for malicious purposes, it’s also a useful tool for security professionals to test and strengthen system defenses against such attacks.
Click on the Entities tab to copy the file hash.

Investigate the file hash associated with the incident. Copy the file hash and remove the (SHA1) at the end. Then go to virustotal.com, click on SEARCH, paste the hash in, and press enter. See the screenshot below. Read through the DETECTION section and click on DETAILS, RELATIONSHIP, BEHAVIOUR, and COMMUNITY.
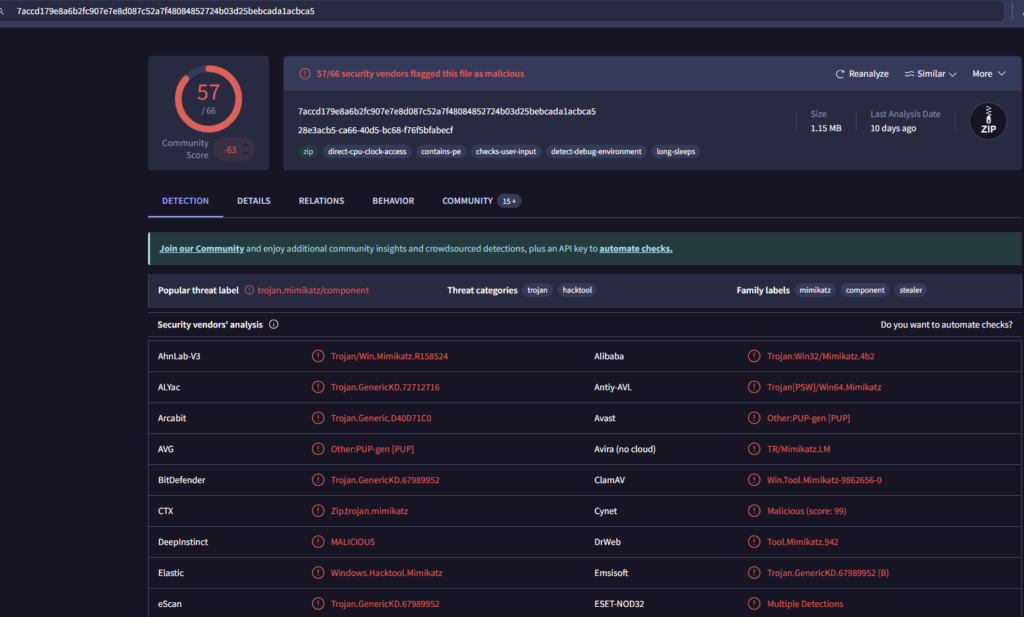
Next, In the comment session, leave a detailed comment about the result of your analysis.
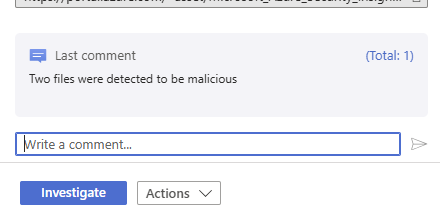
Click on the incident under the Timeline tab. On the right side, scroll down and click on the Alert link as shown below. This will take you to the Microsoft Defender portal.
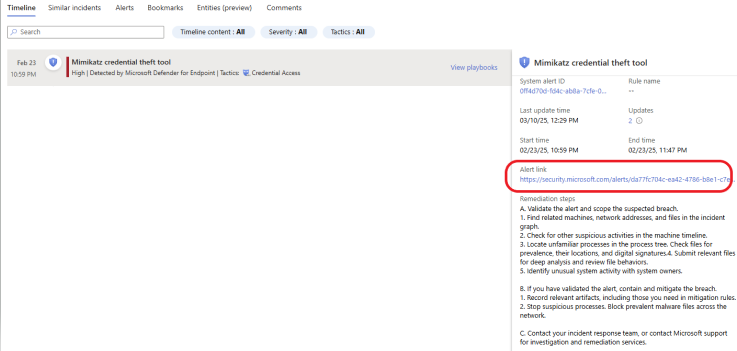
Clicking on the Alert link takes you to Microsoft Defender on the Alert story page, where you can get even more information about the incident and take some action.
The process tree in Microsoft Defender helps security teams trace the origin of a potential threat. It provides insight into the entire lifecycle of processes to aid in incident investigation and response. This tool is handy for investigating malware or other suspicious activity, allowing analysts to follow the attacker’s steps and understand how they gained access or moved through the system.
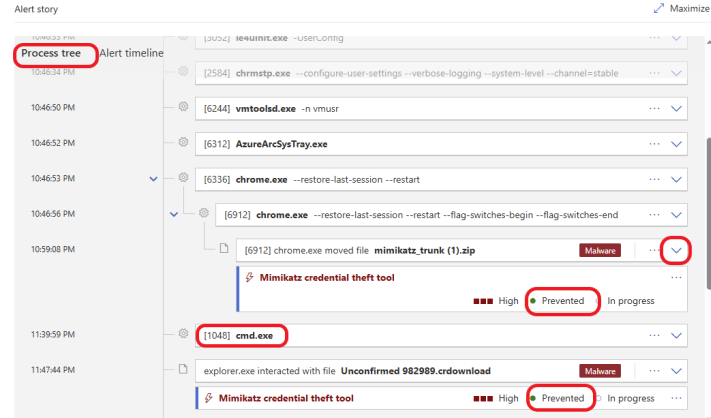
You can click on the down arrow to expand each process. Look for any suspicious or unknown processes that might indicate malicious activity.
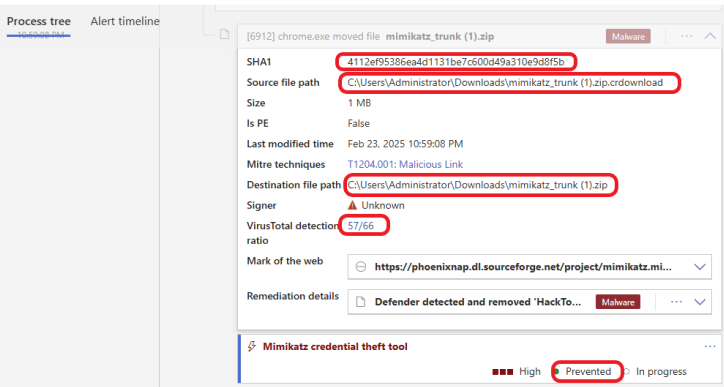
Click on the hyperlink under MITRE ATT&CK Techniques. This link takes you to the MITRE ATT&CK website to learn more about the attacker’s technique. You can manage the alert by clicking on Manage alert. Tune the alert by clicking on Tune alert.
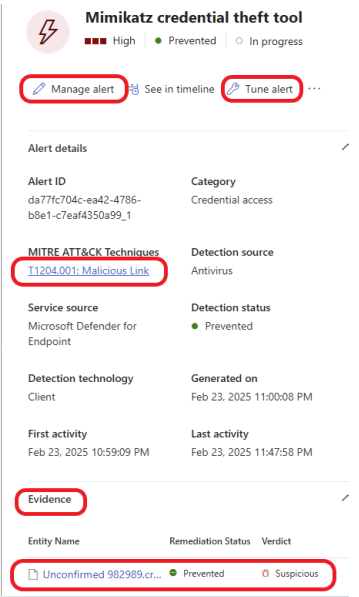
We are done with the analysis phase. The next phase is Containment, Eradication, and Recovery.
2. Containment, Eradication, and Recovery
Containment
NIST SP 800-61 Reference: Containment phase, where you limit the spread of the malware and prevent further impact on your organization. Once you have confirmed that malware is present, the next step is containment. The goal here is to prevent the malware from spreading to other systems or compromising sensitive data.
To stop the malware from spreading to other systems on the network, we are going to isolate (contain) the infected machine. To do this, click on the View incident page hyperlink at the top of the Alert story page, as shown below.
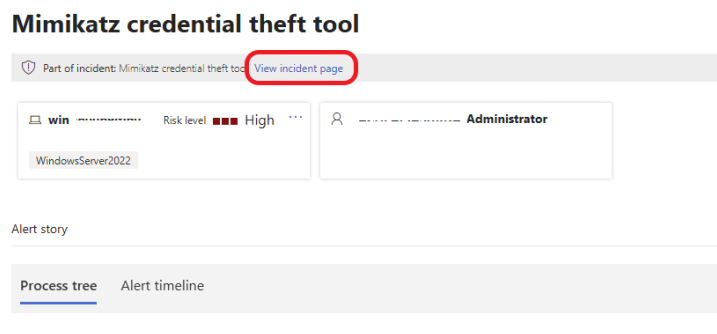
Click on Manage Incident by the top right.
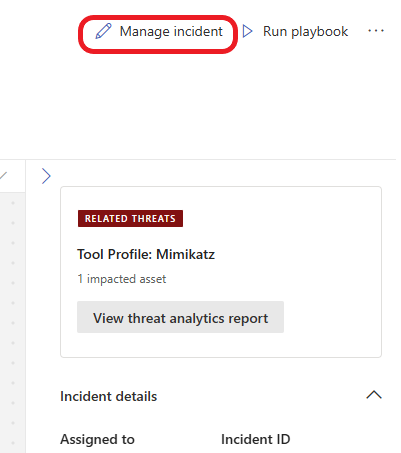
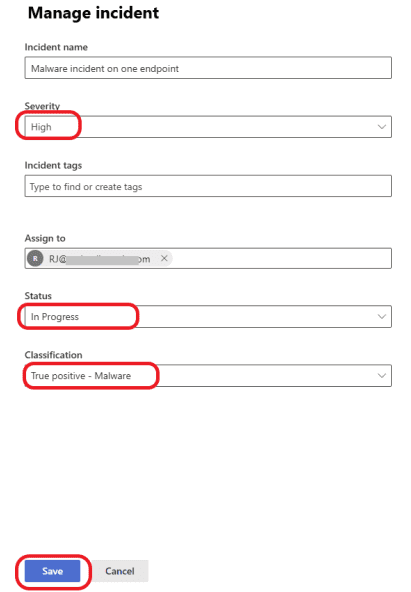
Update the Incident based on your findings and click on the Save button.
Click on the Assets tab at the top of the page. You should see the victim machine listed as shown below. Double-click it.
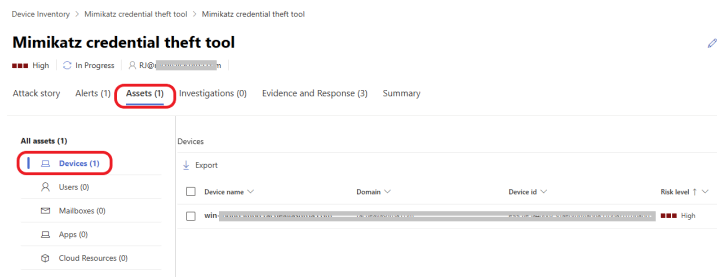
A window opens up, click on Open device page, as shown below, to go to the device page.
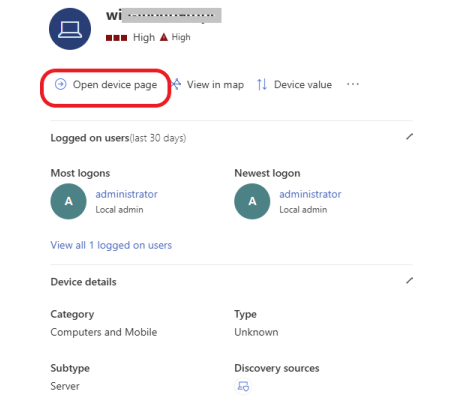
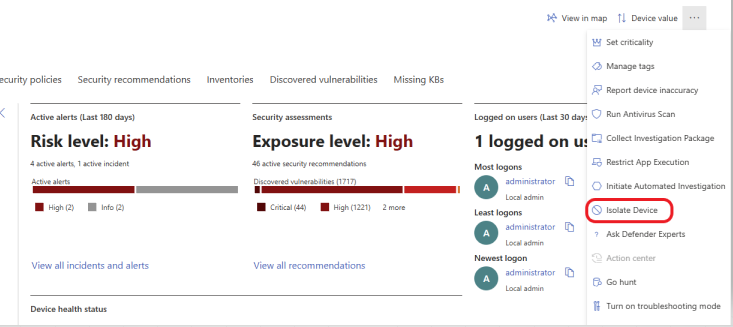
On the device page, click on the ellipsis in the top right corner. Here, you can take many actions depending on the situation and the criticality of the victim machine in the business operation. For this example, I am going to isolate the device to stop the malware from spreading to other devices. Isolating a device during an incident response stops the malware from spreading to other devices or communicating with the command and control center (attacker) while preventing evidence for forensic investigation. Click on Isolate Device.
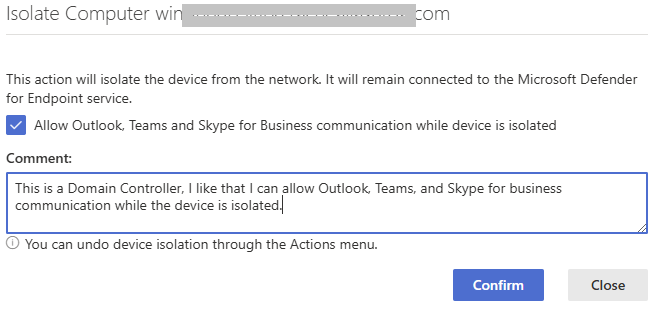
You have the option to allow Outlook, Teams, and Skype for business communication while the device is isolated. Check the box for these applications to communicate. For this example, I will check the box to allow communication and click on the Confirm button. This action will isolate the device from the network, but the device will still be connected to Microsoft Defender for Endpoint.
After isolating the device, I logged into the device and got the notification below.
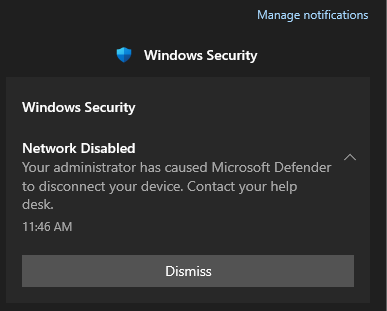
Eradication
NIST SP 800-61 Reference: Eradication phase, where you remove the malware and any residual malicious components. Eradication is the process of completely removing the malware from your systems and ensuring that no traces are left behind.
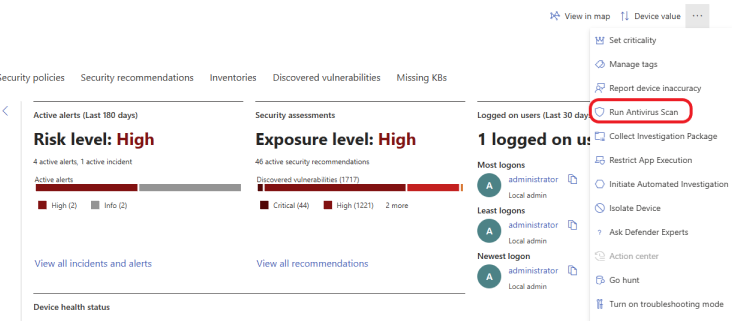
On the device page, click on the ellipsis in the top right corner and click on Run Antivirus Scan, as shown below.
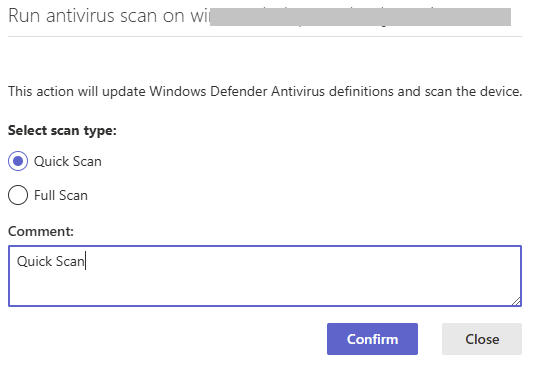
Select a Quick or Full Scan. I will select Quick Scan for this example. Click on the Confirm button.
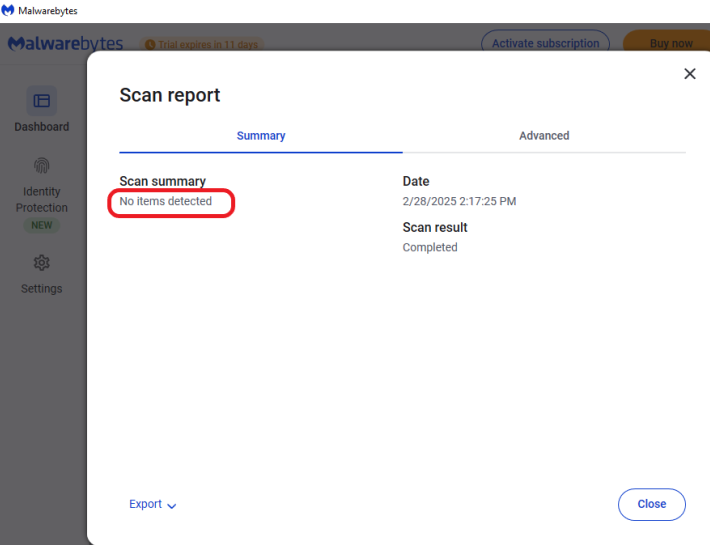
The scan was completed successfully, and no threat was found. I also performed another scan using Malwarebytes, but no threats were found, as shown below.
We are done with the containment and eradication phase.
It is important to monitor the system’s performance and watch for signs of malware, such as:
- Unexplained system slowdowns or crashes
- Unusual network activity or high bandwidth usage
- Unexpected pop-up ads or strange browser behavior
- Unfamiliar processes running in the background
- Increased CPU or memory usage without explanation
- Files or programs being modified or encrypted without your knowledge
- Unauthorized access attempts or login failures in system logs
- Disabled security software or firewall settings
Recovery
NIST SP 800-61 Reference: Recovery phase, where you restore normal operations and ensure that the malware has been fully eradicated. The recovery phase focuses on bringing systems back online and ensuring that they are functioning securely.
In a production environment, you may need to reimage the machine and restore a clean backup. Make sure your Operating System is up to date with the latest patches.
I monitored the device, but it was very slow and kept frozen. So I decided to restore the snapshot I took before the malware, since this is a virtual machine. I updated the Operating System to the latest version.
Lessons Learned
NIST SP 800-61 Reference: Post-Incident Activity phase, where you analyze the incident and take steps to improve security and incident response in the future.
Once the malware incident is resolved, it’s important to conduct a post-incident review to learn from the event and improve your incident response processes.
Key Actions in This Phase
- Conduct a Post-Incident Review: Analyze the incident to understand how the malware infiltrated your systems, how it was detected, and how it was contained and eradicated.
- Update Detection Rules: Based on the lessons learned, refine your detection rules to improve the accuracy of future alerts and ensure quicker identification of similar threats.
- Train Employees: Educate employees on malware prevention best practices, such as not clicking on suspicious links and ensuring.
How to Handle False Positives in Malware Detection
False positives can occur when legitimate activities, such as software updates or system configuration changes, trigger alerts that resemble malware behavior. Handling false positives effectively is crucial to avoid wasting resources on unnecessary investigations.
Key Actions to Handle False Positives:
- Examine Context: Always review the context of the alert. Look at factors such as the time of day, the user involved, and whether the activity aligns with normal operations.
- Correlate with Other Data: Correlate the alert with data from other sources (e.g., network logs, endpoint protection logs) to determine if the alert is truly malicious or if it’s a result of legitimate activity.
- Refine Detection Rules: Continuously improve your detection rules to reduce the likelihood of false positives. For example, increase thresholds for triggering alerts or add more context (e.g., user role or geographical location) to improve accuracy.
- Automate Triage: Implement automated playbooks in Sentinel to handle low-level alerts and quickly dismiss false positives without requiring manual intervention.
Conclusion
Investigating a malware incident with Microsoft Sentinel while following NIST SP 800-61 guidelines provides a structured and efficient approach to incident response. By detecting malware early, containing its spread, eradicating it, and learning from the incident, organizations can reduce the impact of malware attacks and improve their security posture.
By continuously refining your detection and response strategies, you can stay ahead of evolving malware threats.