Nessus, developed by Tenable, is a security vulnerability scanning tool that checks for weaknesses in devices, networks, applications, operating systems, and cloud services. While Nessus is a Proprietary software, there is also a free community version. The community edition of Nessus is called Nessus Essential by Tenable. Allows users to scan up to 16 IP addresses for free. I plan to use this tool to scan my lab environment as it perfectly meets my requirements. Now that you understand what Tenable Nessus entails, let’s proceed with the installation process.
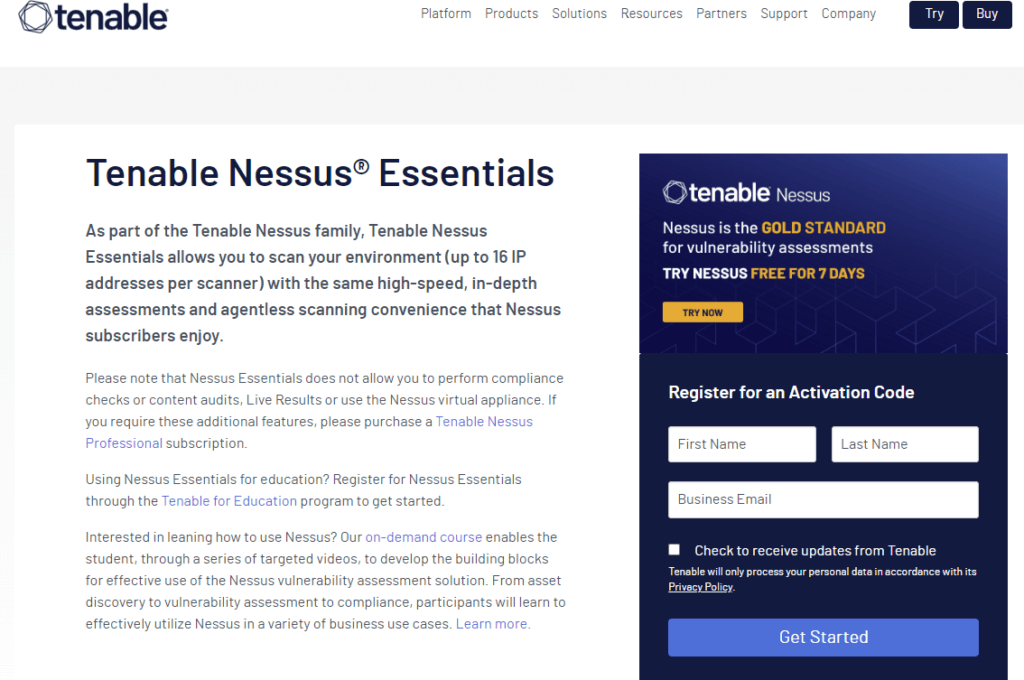
Click here to download the Nessuss Installer from the Tenable website. Fill out the form to register for an activation code. Click Get Started.
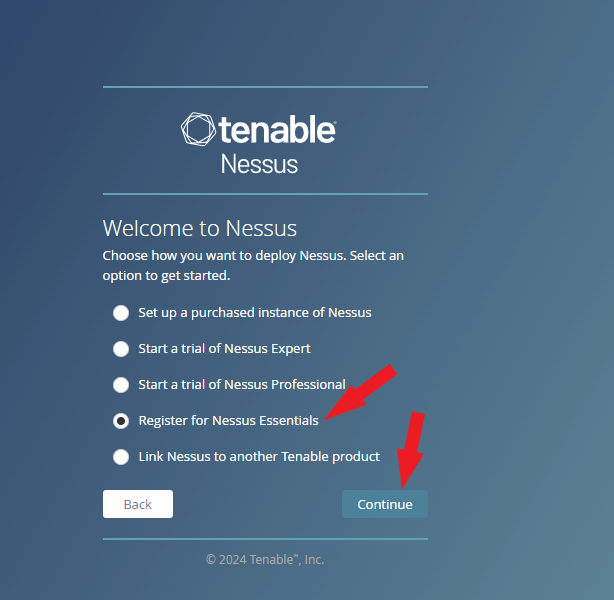
Check the box next to Register for Nessus Essentials and click Continue.
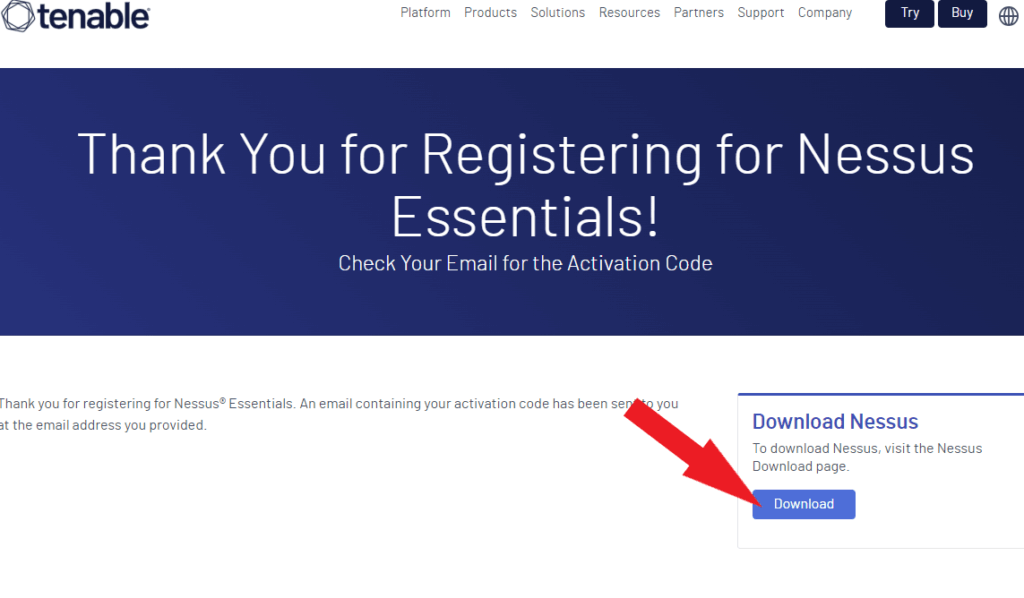
Click the Download button to visit the Nessus download page.
Choose the download version and platform (Operating System) and click the Download button to download Nessus Essential Installer.
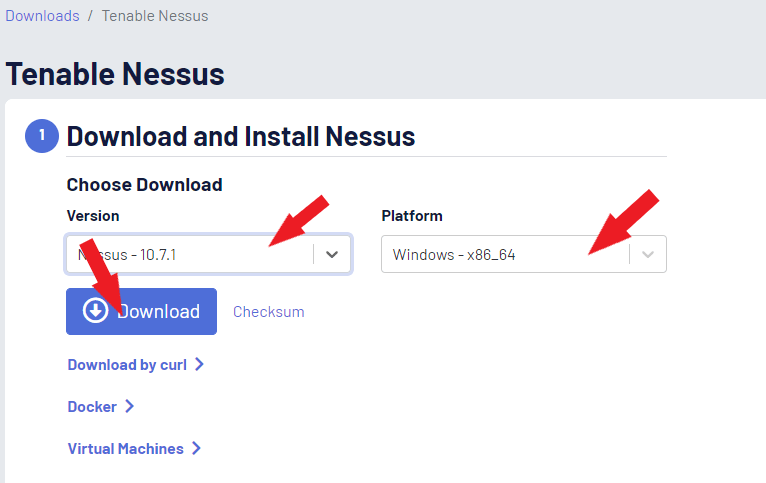
Click the I Agree button to agree to the License Agreement. And the installer will start downloading.

Open File Explorer on your computer and locate the downloaded Nessus Essential Installer.
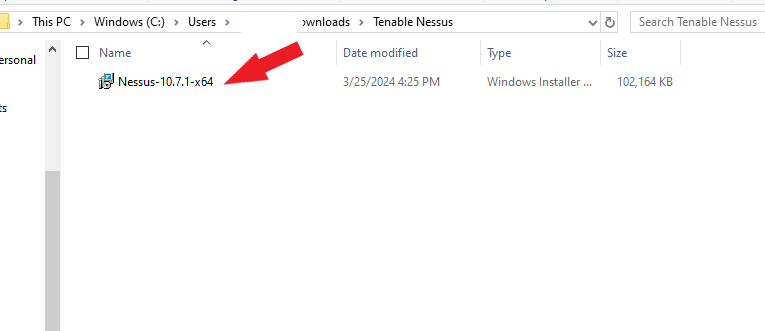
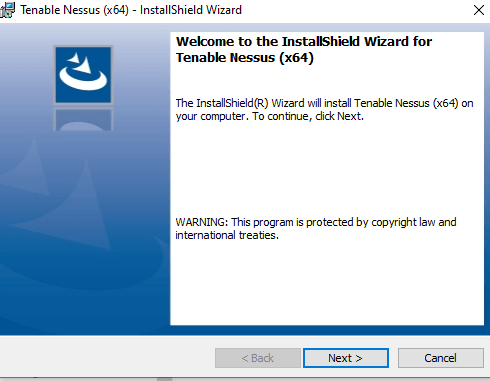
Double-click the installer. The InstallShield wizard appears. Click Next and follow the steps.
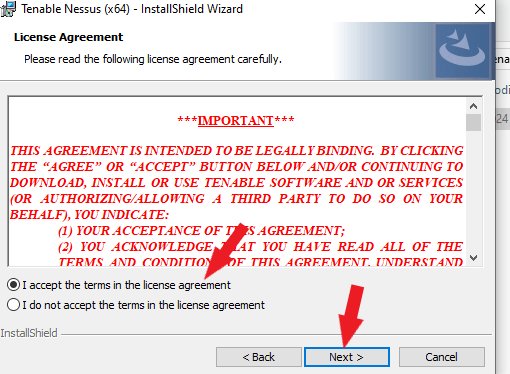
Check the box next to I accept the terms in the license agreement and click Next.
Choose what location to install Nessus. Example C:\Program Files\Tenable\Nessus. Click Next.
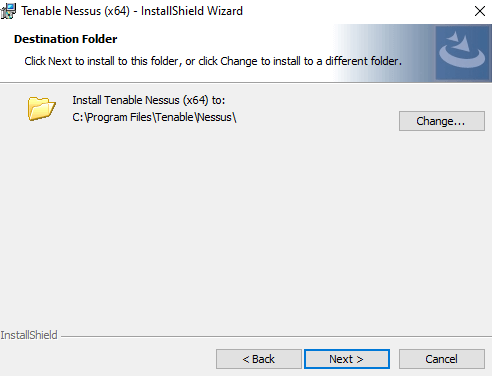
Click Install to install Nessus.
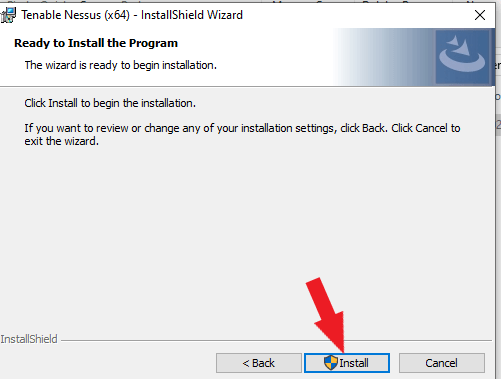
Nessus essential is now installed successfully. Click on the Finish button. Nessus opens up in your default browser. Nessus uses port 8834; Link here. Click the Connect via SSL button.

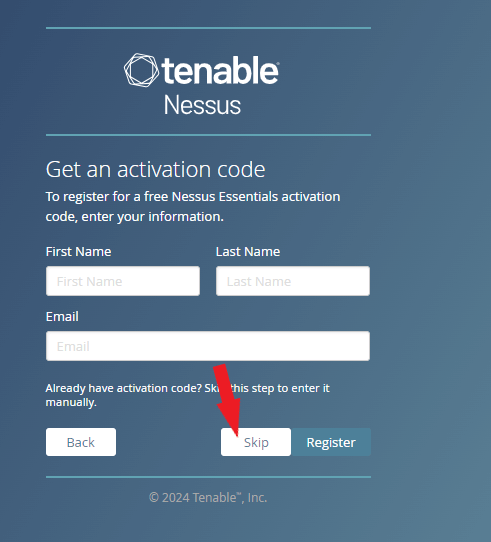
Skip this step, as we received an activation code from Nessus in the initial process.
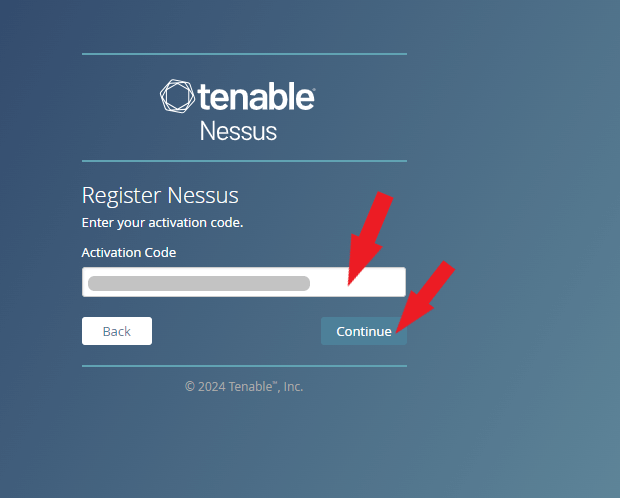
Locate the email and enter the activation code received earlier in the installation process. Click the Continue button
Click the Continue button to proceed with the installation.

Wait while the plugins download.
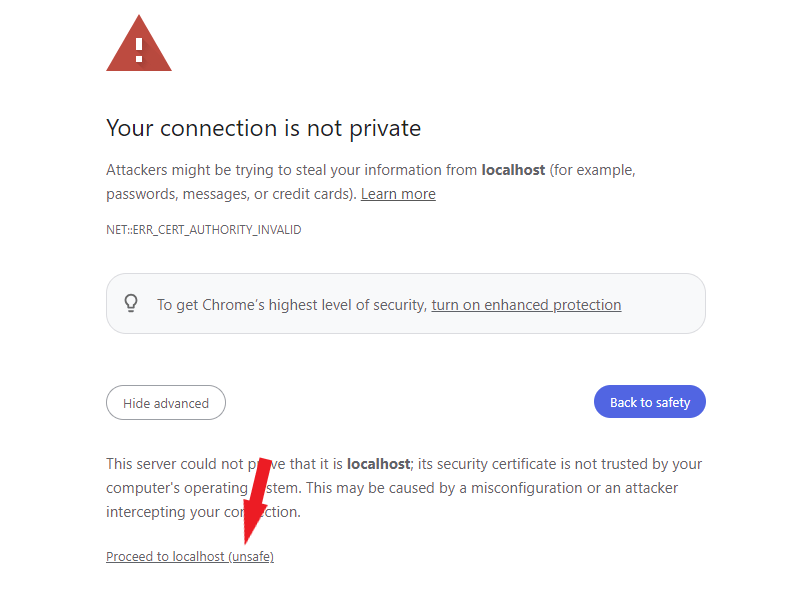
Now it’s time to log in to Nessus. Click the Advance button, then click the Proceed to localhost (unsafe). Enter the username and Password created in the initial process, then click the Sign In button as shown in the screenshot below.
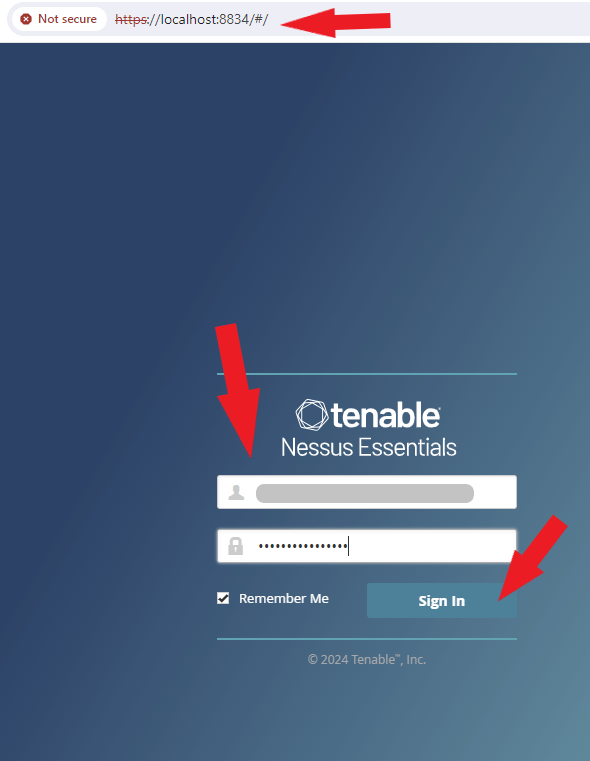
Success, we are in!