Table Of Contents
- 1 Secure Your Organization’s Mobile App on Personal Smartphones (BYOD)
- 2 Why Securing BYOD with Microsoft Intune is Essential
- 3 Manage Data and Protect Sensitive Information
- 4 Enroll Devices into Microsoft Intune
- 5 Disable Microsoft security defaults in Microsoft Entra ID
- 6 Configure App Protection Policies
- 7 Configure Conditional Access Policy to Enforce the App Protection Policies
- 8 How to Implement Conditional Access
- 9 Educate Employees on Mobile Security Best Practices
- 10 Conclusion
- 11 About The Author
Secure Your Organization’s Mobile App on Personal Smartphones (BYOD)
In today’s increasingly mobile world, employees are more likely to use their personal smartphones and devices for work, using an approach known as Bring Your Own Device (BYOD). While this can boost productivity and flexibility, it also presents significant security challenges for organizations. Ensuring that your organization’s mobile apps are secure on personal smartphones is paramount. Fortunately, Microsoft Intune, a comprehensive Mobile Device Management (MDM) and Mobile Application Management (MAM) solution, offers powerful tools to protect sensitive data and maintain compliance. In this blog post, I will guide you through the steps to secure your organization’s mobile apps on personal smartphones using Microsoft Intune.
Why Securing BYOD with Microsoft Intune is Essential
BYOD offers several benefits, such as reducing hardware costs and improving employee satisfaction. However, it also increases the risk of data breaches, device loss, and unauthorized access. Without a clear strategy and security framework, organizations expose themselves to potential data leaks, cyberattacks, and non-compliance with industry regulations. Microsoft Intune provides a robust set of tools to manage and secure personal devices that access corporate resources. It enables IT admins to enforce security policies, monitor device compliance, and ensure that only authorized users and apps can access sensitive corporate data.
Manage Data and Protect Sensitive Information
To protect sensitive corporate data, organizations need to ensure that any data accessed or stored on personal devices is protected. Microsoft Intune provides several data protection capabilities to secure your organization’s mobile apps.
Data Protection Strategies in Intune:
Mobile Application Management (MAM): Apply MAM policies to prevent data leakage by controlling actions like copy-paste, saving documents, or forwarding emails from corporate apps. For example, you can stop users from copying text from a work app and pasting it into a personal app.
App Wrapping: Microsoft Intune allows you to “wrap” mobile apps with a management layer that enforces security policies. This can ensure that data within the app remains encrypted and is only accessible under specified conditions.
Remote Wipe Capabilities: In the event of a lost or stolen device, Intune allows IT admins to remotely wipe the organization’s data from the device without affecting the user’s personal data. This can be especially important for maintaining the integrity of sensitive information on BYOD devices.
Enroll Devices into Microsoft Intune
The first step in securing your organization’s mobile apps on personal smartphones is enrolling the devices into Intune. Microsoft Intune supports both iOS and Android devices, allowing users to bring their own smartphones while giving IT teams the control they need. After enrollment, ensure that the devices are compliant with your organization’s mobile security policies. Intune can check if the device is running the latest operating system, has encryption enabled, and meets other requirements.
- Ensure that Microsoft Intune is properly set up within your organization. You’ll need an Entra ID, an Intune subscription, and appropriate admin privileges.
- Employees should install the Company Portal app on their personal devices. This app will allow them to enroll their devices with Intune and access corporate resources securely.
- Employees can enroll their devices by logging into the Company Portal with their work credentials. Intune will automatically verify the device’s compliance with your organization’s security policies.
Disable Microsoft security defaults in Microsoft Entra ID
To use a conditional access policy. You will need to turn off Microsoft security defaults. Follow the following steps to turn off Microsoft security defaults:
In Microsoft Entra ID, click on Identity >Overview >Properties >Manage security defaults. Select Disabled (not recommended) and Click the Save button.
Configure App Protection Policies
Microsoft Intune offers powerful app protection policies that can be applied to your organization’s mobile apps, whether the device is personally owned or company-issued. These policies help secure apps by ensuring that sensitive data is protected, even when used on a personal device.
From the Intune Admin Center, click on Apps >App protection policies >Create policy
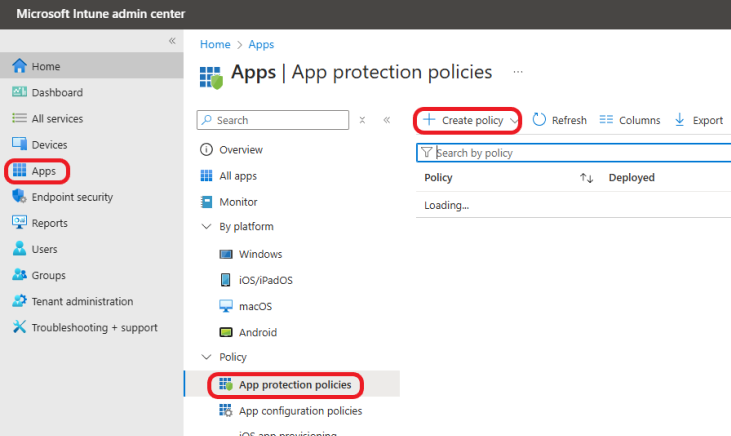
Choose the platform (iOS or Android). For this example, I will choose Android.

Name your policy, Enter a meaningful description, and click on the Next button.

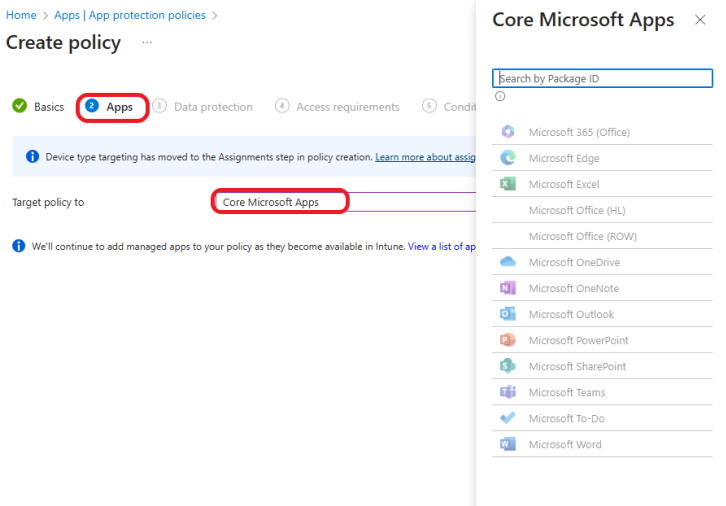
Click on the drop-down menu and select which apps to target the policy to, depending on which apps your organization uses. For this example, I will select the Core Microsoft app in the drop-down. Click on the blue hyperlink “View a list of apps that will be targeted” to view the list of the targeted apps, as shown below. Click the Next button.
On the Data Protection page, Set the data protection policy based on your organization’s needs. I will set the policies as follows: Backup org data to Android backup services >Block
Send org data to other apps >Policy Managed apps
Save copies of org data >Block
Allow user to save copies to selected services >OneDrive for Business and Sharepoint

Transfer telecommunication data to Any dialer app
Transfer messaging data to Any policy-managed messaging app
Receive data from other apps >Policy Managed apps
Open data into Org documents >Block
Allow users to open data from selected services >OneDrive for Business and Sharepoint
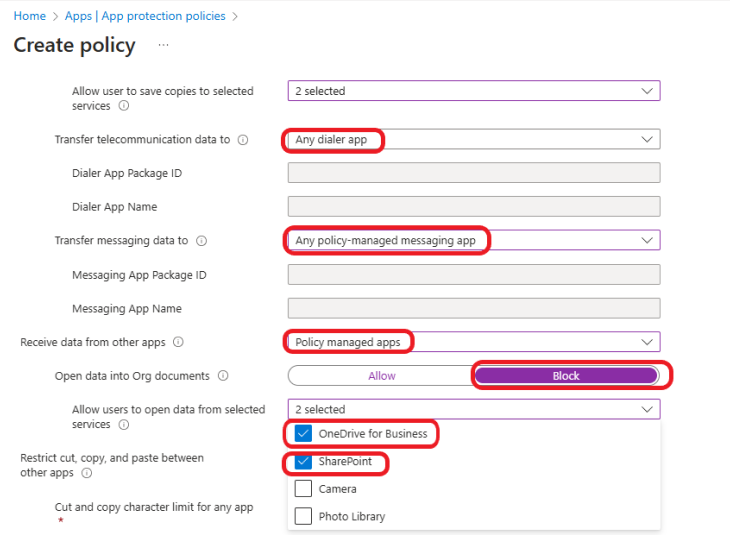
Restrict cut, copy, and paste between other apps >Policy managed apps with paste in
Cut and copy character limit for any app >0
Screen capture and Google Assistant >Block
Encrypt org data >Require
Encrypt org data on enrolled devices >Require
Sync policy managed app data with native apps or add-ins >Block
Printing org data >Block
Restrict web content transfer with other apps> Microsoft Edge
Start Microsoft Tunnel connection on app-launch >Yes
Click on the Next button.

On the Data Access requirements page, Set the policy based on your organization’s needs. I will set the policies as follows:
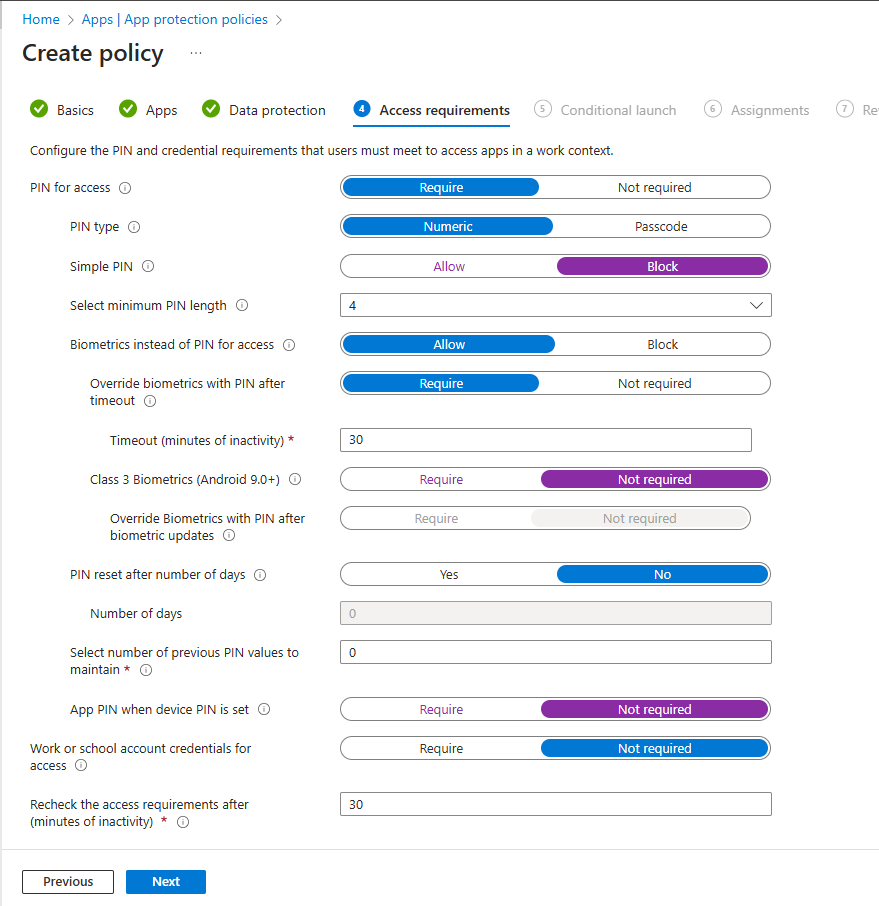
PIN type >Numeric
Simple PIN >Block
Select minimum PIN length >4
Biometrics instead of PIN for access >Allow
Override biometrics with PIN after timeout >Require
Timeout (minutes of inactivity) >30
Class 3 Biometrics (Android 9.0+) >Not required
App PIN when device PIN is set >Not required
Recheck the access requirements after (minutes of inactivity) >30
Click on the Next button.
I will leave the Conditional launch page as default.

Let’s assign the policy to a group. On the assignment page, under included groups, click on Add groups. Search for the group you want to include. For this example, I assigned the policy to All users‘ group. Select the group and click on the Next button.

Click the Next button.

Review Your policy and click Create.

Configure Conditional Access Policy to Enforce the App Protection Policies
Conditional Access is a key feature of Microsoft Intune that allows organizations to control who can access what resources, from which devices, and under what conditions. By setting up conditional access policies, you can restrict access to mobile apps based on the security state of the device.
How to Implement Conditional Access
Click on Endpoint security >Conditional access.

Click on Policies >New policy.
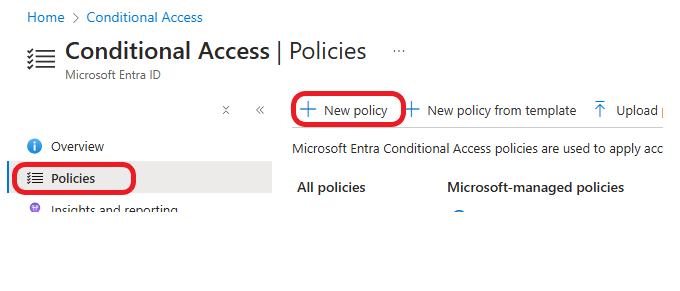
Give your policy a name, click on Users, and select All users under Include.
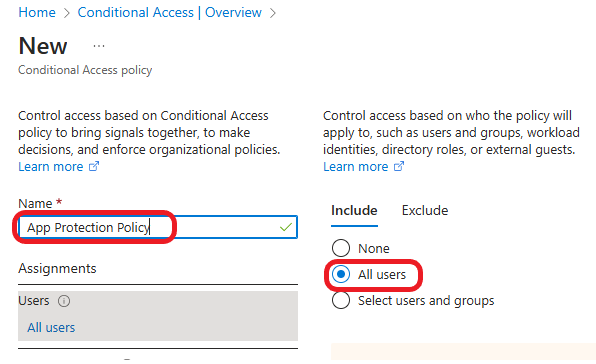
Click on Target resources >Select resources >Select > Office 365 >Select.
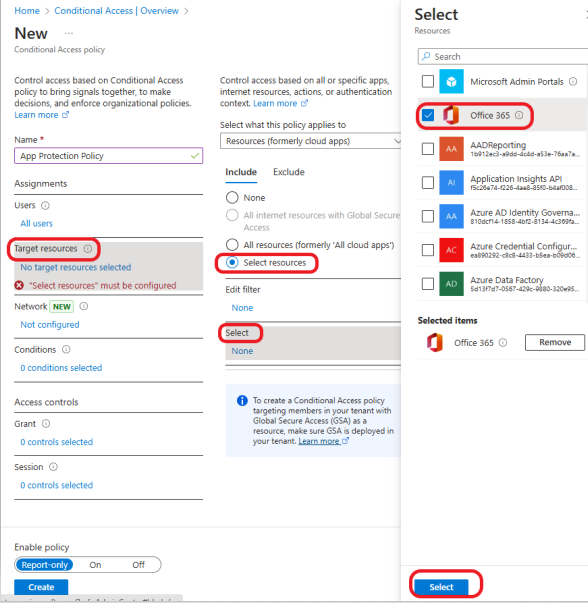
Click on Conditions >Device platforms. Configure >Yes, choose Select device platforms >Android >Done.

Click on Conditions >Client apps. Configure >Yes, choose Browser >Mobile apps and desktop clients >Done.

Click on Grant >Grant access > Require app protection policy > Select.
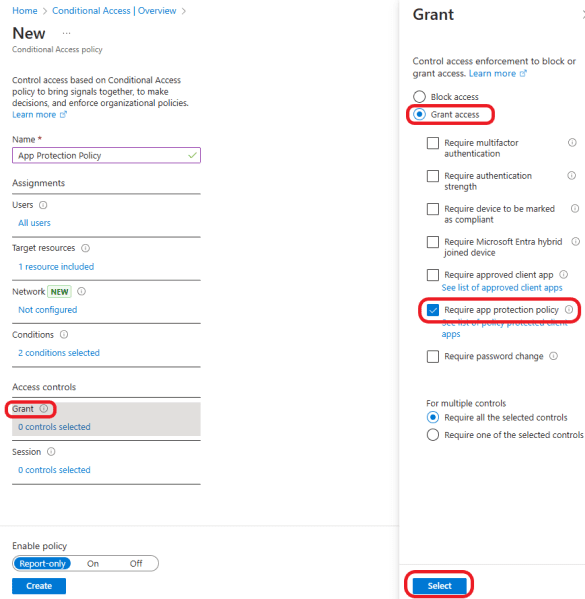
Click on to enable the policy and click on the Create button.

App Protection Policy was created successfully and enabled, as shown below.

Educate Employees on Mobile Security Best Practices
Although technology can do a lot to protect your organization’s mobile apps, human behavior is still a key factor in security. Educating employees on the best practices for securing their personal devices and the importance of mobile security can significantly lessen the risk of security breaches.
Security Awareness Tips for Employees:
Use Only Approved Apps: Ensure that employees only use corporate-approved apps for work-related tasks and avoid installing untrusted or unofficial apps. even in a bring-your-own-device (BYOD) environment.
Enable Strong Authentication: Require employees to set up strong passwords, PINs, or biometric authentication (like fingerprint or face recognition).
Update Devices Regularly: Encourage employees to keep their personal devices updated with the latest security patches and Operating System updates.
Conclusion
Securing your organization’s mobile apps on personal smartphones is crucial to protecting sensitive corporate data and ensuring compliance with security standards. Microsoft Intune offers comprehensive tools to manage and secure personal devices, enforce app protection policies, and control access to corporate resources. By following the steps outlined in this guide, you can ensure that your organization’s mobile app ecosystem remains secure, even in a bring-your-own-device (BYOD) environment.
