Table Of Contents
How to Send CrowdStrike Logs to Splunk: A Step-by-Step Guide
Integrating CrowdStrike Falcon logs with Splunk is an effective way to enhance your organization’s security monitoring and incident response capabilities. By sending CrowdStrike logs to Splunk, you can leverage Splunk’s powerful data analytics and visualization features to have valuable insights into your security posture. In this post, I will walk you through the process of sending CrowdStrike logs to Splunk for effective security event monitoring.
Why Send CrowdStrike Logs to Splunk?
Before diving into the process, it’s important to understand the benefits of integrating CrowdStrike Falcon with Splunk:
- Centralized Log Management: Splunk can aggregate logs from multiple sources, allowing you to view, analyze, and search all your security data from one platform.
- Improved Threat Detection: Splunk’s machine learning and data analysis capabilities can help you identify suspicious activity within CrowdStrike logs, improving your ability to detect and respond to security threats.
- Enhanced Reporting: With Splunk, you can create custom dashboards, alerts, and reports based on the data received from CrowdStrike, allowing you to make data-driven security decisions.
- Streamlined Incident Response: By combining CrowdStrike’s endpoint data with Splunk’s advanced analytics, your security team can streamline investigation workflows and resolve incidents more efficiently.
Prerequisites
Before starting the integration process, ensure you meet the following prerequisites:
- CrowdStrike Falcon Account: Make sure your organization has an active CrowdStrike account.
- Splunk Enterprise or Splunk Cloud: Ensure you have access to a running instance of Splunk to store and analyze the logs.
- Required Permissions: Ensure you have appropriate permissions in both CrowdStrike and Splunk to access API keys and configure integrations.
Set Up CrowdStrike API Access
To send CrowdStrike logs to Splunk, you need access to the CrowdStrike API to extract the logs. Log into the CrowdStrike Falcon Console. Navigate to Support and Resources > Resources and Tools > API Clients and Keys, as shown below.

Click Create API Client to generate a new API client.
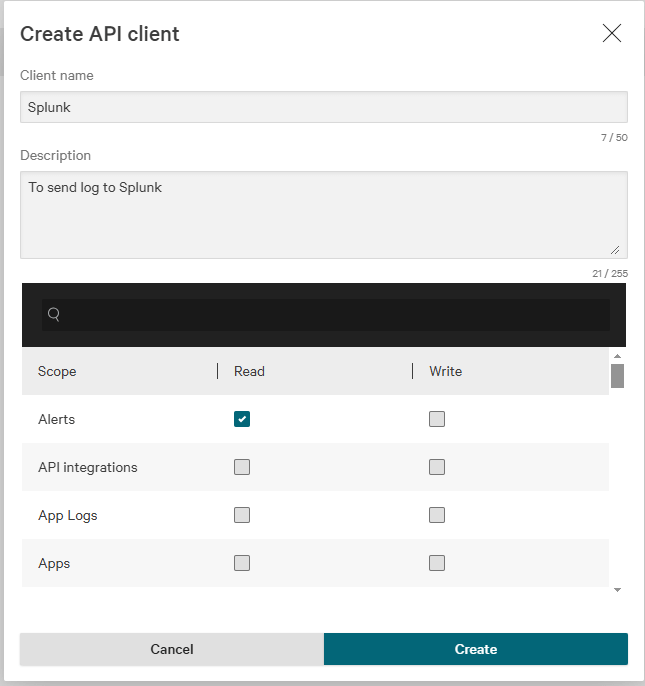
Give your new API a name and a meaningful description. Assign API Scopes by selecting scopes based on your needs. For this example, select Alert, Hosts, and Event streams. You can also select just the Event Stream if you want and the Read capability. Click the Create button.
A new API was created with Client ID and Secret. Take note of the Client ID and Client Secret, as these will be used to authenticate API requests. This is the only time you will get the secret, so please copy it to a safe place and click Done.

Next, we are going to create a new index (Optional)
Log in to the Splunk instance using your administrator credentials. Go to Settings > Indexes.

Click on the New Index button to create a new index.

Give your new index a name, leave everything else as default, and click the Save button to save it.

Using the Splunk Add-on for CrowdStrike
Splunk offers a pre-built add-on for CrowdStrike, making it easier to integrate and send logs from CrowdStrike to Splunk. Click here to download the add-on. Log in with your Splunk.com credentials and click on the Download button to download.

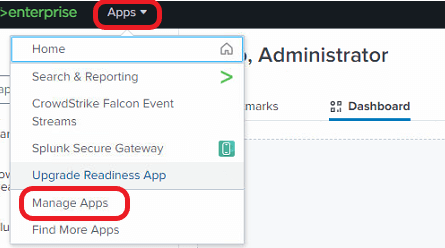
Log in to the Splunk instance using your administrator credentials. Go to Apps > Manage Apps.
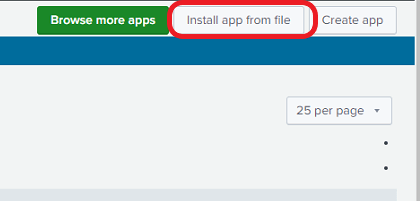
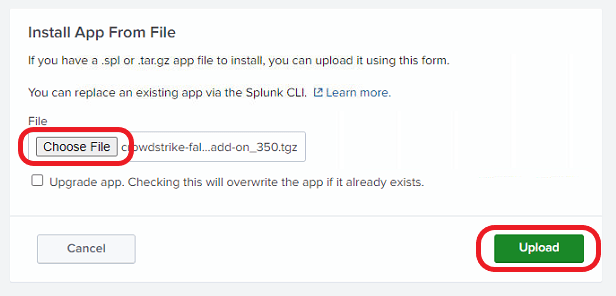
Click on Install app from file.
Click on Choose File and select the downloaded add-on file. Click on the Upload button to upload it.
Click on Apps > CrowdStrike Falcon Event Streams.

Click on Configuration > Proxy. Check the box next to Enable to enable the add-on. Select http, enter port number 8080, enter your username and password, and click the Save button.

Click on the Account tab and click Add to add a new account.

Give the account a name and enter the CrowdStrike API credentials (Client ID, Client Secret) to allow the add-on to pull data. Click the Add button.

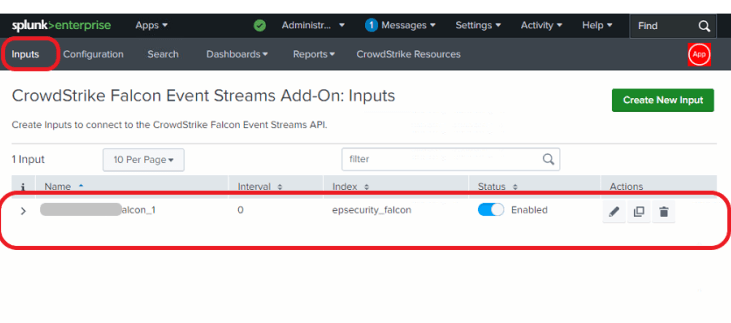
Click on the Inputs tab > Create New Input.

Give the input a name, and select the index created or a default index. Select the API credential and click on the Add button.

The input was added successfully, as shown below.
Click on Reports tab > CrowdStrike Event Stream Data Indexed vs Event Time to view the logs.

Now that your logs are flowing into Splunk, you can start creating dashboards, reports, and alerts based on the data.
- Dashboards: Use the Splunk dashboard features to visualize key metrics from the CrowdStrike logs, such as the number of threats detected, endpoint status, and more. Click here to learn how to create a dashboard in Splunk.
- Alerts: Set up alerts in Splunk to notify your security team of any suspicious activity or anomalous events based on CrowdStrike data.
Conclusion
Integrating CrowdStrike Falcon logs with Splunk provides you with powerful tools for proactive security monitoring and incident response. Splunk add-on for CrowdStrike allows you to centralize your log data and leverage Splunk’s advanced capabilities to detect, analyze, and respond to security threats more effectively. By following the steps outlined in this guide, you’ll be well on your way to enhancing your organization’s security infrastructure and improving visibility into endpoint activity.
