Table Of Contents
- 1 Key Tips for Improving Your Microsoft 365 Security
- 2 1. Turn Off User Consent for Apps
- 3 How to Turn Off User Consent for Applications
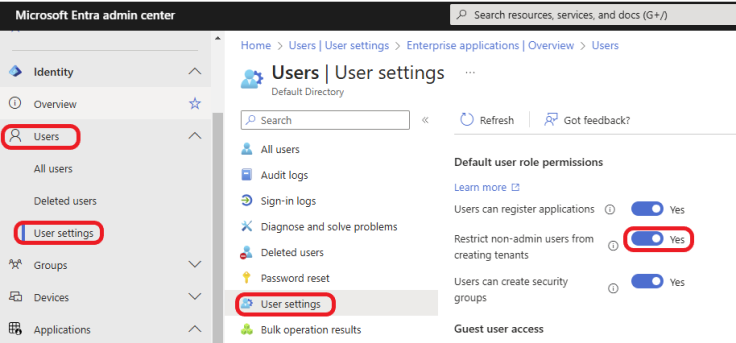
- 4 2. Restrict Non-Admin Users from Creating Microsoft Tenants
- 5 How to Restrict Tenant Creation
- 6 3. Restrict Access to the Microsoft Entra Admin Center
- 7 How to Restrict Access to the Microsoft Entra Admin Center
- 8 Why It’s Important to Restrict Access to the Microsoft Entra Admin Center?
- 9 4. Configure SharePoint Content to Only Be Shared with People in Your Organization
- 10 5. Set View Permission by Default for SharePoint
- 11 Why Is It Important to Set Permission to View for SharePoint and OneDrive?
- 12 Conclusion
- 13 About The Author
Key Tips for Improving Your Microsoft 365 Security
Microsoft 365 is a powerful suite of tools for productivity, collaboration, and communication within organizations. However, with its expansive features and widespread use, it’s critical to ensure that sensitive data and resources are properly secured. Cybersecurity risks, such as unauthorized access, data leaks, and malware, are a growing concern for many businesses, which is why taking proactive steps to secure your Microsoft 365 environment is essential. In this blog post, I will cover several key ways to enhance Microsoft 365 security, including turning off user consent, restricting non-admin users from creating tenants, controlling access to the Microsoft Entra admin center, and ensuring that SharePoint and OneDrive content can only be shared with people in your organization.
1. Turn Off User Consent for Apps
In Microsoft 365, users can grant consent to third-party apps to access their data, including emails, calendar events, and documents. While this can be convenient for users, it can also pose a security risk if unauthorized or malicious apps are given access to sensitive company data. Therefore, one of the most important security practices is to turn off user consent to prevent unapproved apps from gaining access to corporate resources.
How to Turn Off User Consent for Applications
To turn off user consent for applications to access your organization’s data, log into the Microsoft Entra admin center with administrator credentials. Click on Applications > Enterprise applications.
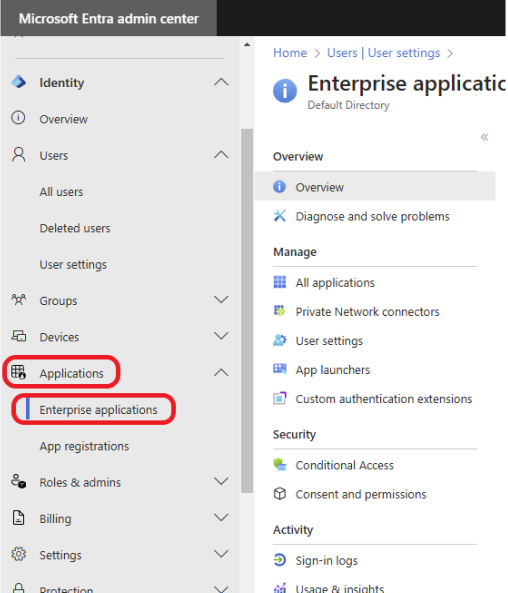
Under the Security session, Click on Consent and permissions.
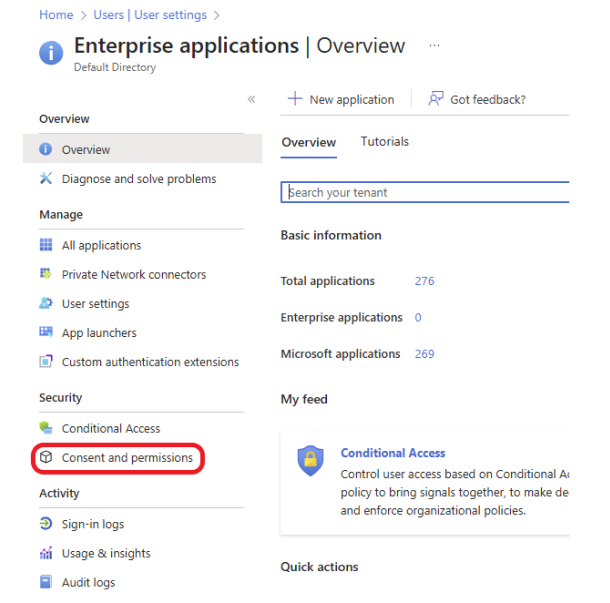
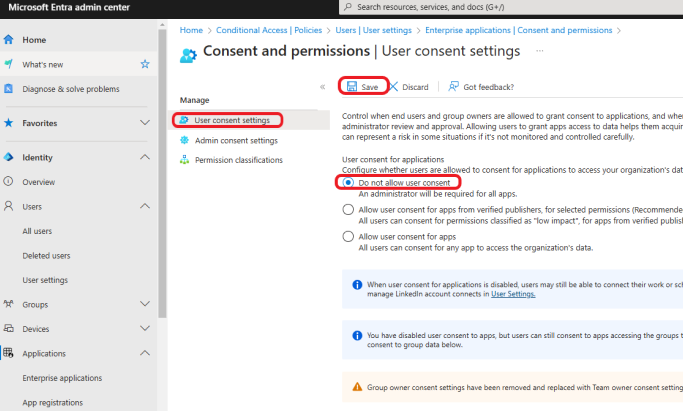
Click on User consent settings, under User consent for applications, select Do not allow user consent. Click Save to save the changes. This setting will block users from granting third-party apps access to their Microsoft 365 data, forcing all app permissions to go through administrators for approval.
Why Is It Important to Turn Off User Consent for Applications?
Turning off user consent In Microsoft 365 to third-party applications helps prevent malicious apps or unintended permissions from being granted, thereby safeguarding organizational data. This is particularly crucial for organizations in highly regulated industries where data privacy is a top concern.
2. Restrict Non-Admin Users from Creating Microsoft Tenants
Another security risk that organizations often overlook is the creation of new tenants by non-admin users. In Microsoft 365, users with the correct permissions can potentially create new tenants, which could be used maliciously or to bypass security controls. By restricting non-admin users from creating new tenants, you add an added layer of security to your Microsoft 365 environment.
How to Restrict Tenant Creation
Log into the Microsoft Entra admin center with administrator credentials. Click on Users > User settings >User settings. Turn Restrict non-admin users from creating tenants to Yes. Click on Save to save the settings.
Why Is It Important to Restrict Non-Admins from Creating Tenants?
This security measure ensures that only trusted administrators have the ability to create new tenants, preventing unauthorized tenants from being created within your organization’s Microsoft 365 environment. By enforcing this restriction, you help protect your organization from potential breaches or misuse.
3. Restrict Access to the Microsoft Entra Admin Center
The Microsoft Entra admin center (formerly Azure Active Directory) is where administrators can configure access to corporate resources, manage users, and set security policies. If unauthorized users gain access to this portal, they could potentially make changes that impact the security of your Microsoft 365 environment.
How to Restrict Access to the Microsoft Entra Admin Center
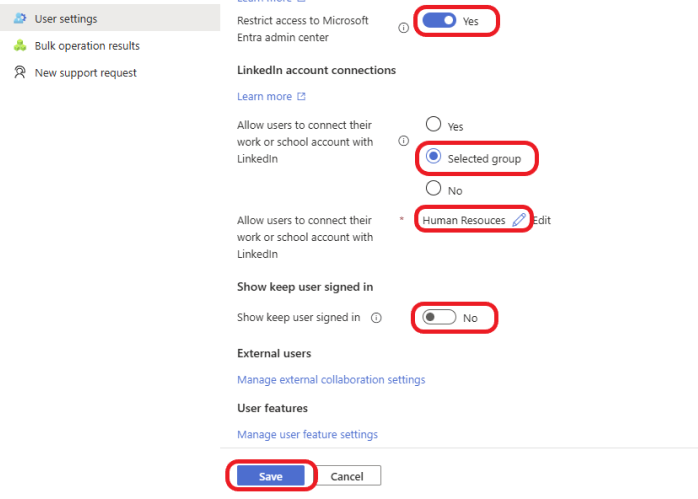
Log into the Microsoft Entra admin center with administrator credentials. Click on Users > User settings >User settings. Turn Restrict access to Microsoft Entra admin center to Yes. This will restrict the creation of Microsoft Entra ID tenants to the global administrator or tenant creator roles. Click on Save to save the settings.
Depending on your organization’s risk tolerance, you can choose to allow users to connect their work or school account with Linkedin. For this example, I will select a group of users that may need to use LinkedIn for their job duties, such as Human resources.
Disabling persistent browser sessions is a good practice. So, for this example, I will turn Show keep user signed in to No.
Why It’s Important to Restrict Access to the Microsoft Entra Admin Center?
No allows non-admin users to create Microsoft Entra ID tenants. Anyone who creates a tenant will become the global administrator for that tenant. Restricting access to the Microsoft Entra admin center reduces the risk of unauthorized modification to key security settings or accessing sensitive information. Limiting this access to only trusted administrators ensures that your organization’s security controls are not compromised.
Sharing content externally can be useful in some cases, but it also exposes your organization to significant security risks. For example, employees may accidentally share confidential documents with external users, or malicious actors could use compromised accounts to leak data. To reduce this risk, it’s important to configure your Microsoft 365 environment so that SharePoint content can only be shared with people within your organization.
Login to Microsoft 365 admin center with admin credentials and click on Sharepoint.
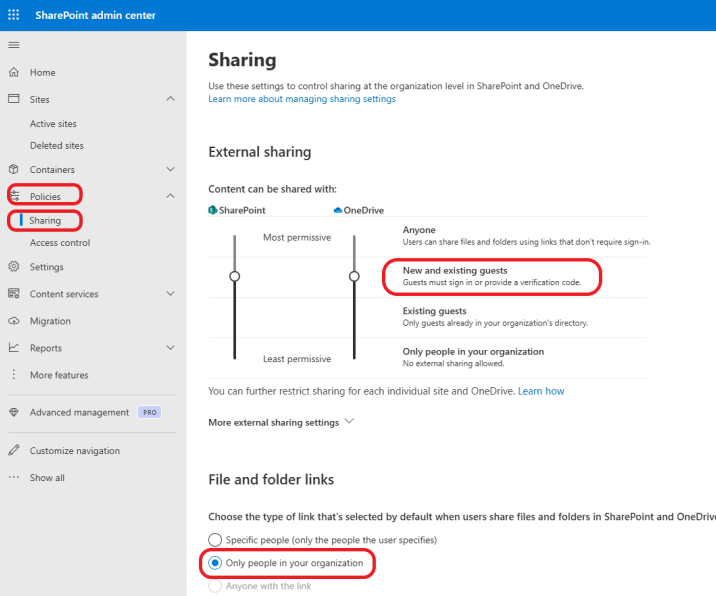
Click on Policies >Sharing. Change the permissions for Sharepoint and OneDrive to meet your organization’s needs. For this example, I will set the Content can be shared with to New and existing guests. Guests must be signed in or provide a verification code. Under File and folder links, select Only people in your organization.
Why Is It Important for Content to Only Be Shared with People in Your Organization?
Restricting SharePoint sharing to only internal users helps prevent accidental or unauthorized data leaks, particularly with sensitive information. It ensures that your files remain within the secure boundaries of your organization, reducing the risk of exposing confidential data to third parties.
A security best practice is to ensure that only those who absolutely need access to a file or document can view it. By default, SharePoint should be configured to provide view-only permissions for users unless they explicitly need more access. This reduces the potential damage that can occur if a file is accidentally shared or misused.
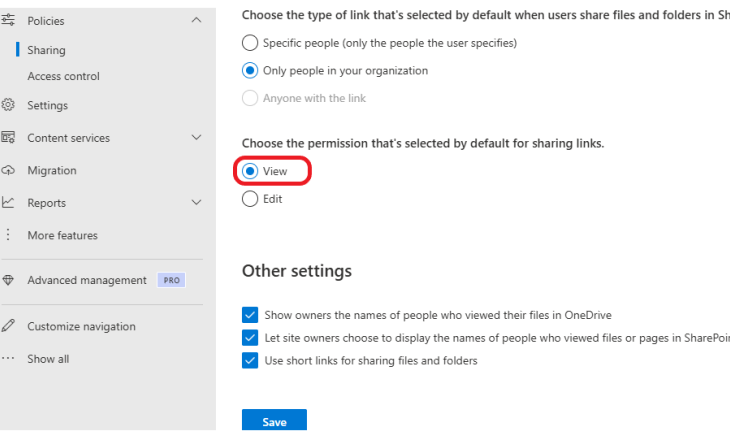
Under Choose the permission that’s selected by default for sharing links, select View. Click the Save button to save the changes.
Setting view permissions by default helps limit the exposure of sensitive content. By granting users only the ability to view files and not modify them unless necessary, you reduce the likelihood of accidental data leaks, ransomware attacks, or malicious modifications.
Conclusion
Enhancing the security of your Microsoft 365 environment is crucial to protect sensitive information, comply with industry regulations, and prevent unauthorized access to your systems. By implementing the outlined key steps, you can significantly improve the security posture of your organization. Make sure to regularly review and update your security settings to keep up with emerging threats and ensure that your Microsoft 365 environment remains as secure as possible.