Table Of Contents
SMB Signing Policy
SMB Signing Policy refers to the security settings related to the SMB (Server Message Block) protocol, which is used for file sharing, printer access, and other network services in Windows environments. Server Message Block signing is a security feature that helps protect SMB communication against certain types of attacks, such as man-in-the-middle attacks, by ensuring that SMB communications are authentic and have not been tampered with.
What is SMB Signing?
SMB Signing involves adding a digital signature to SMB packets. This signature verifies the authenticity of the packets and ensures that the data has not been altered during transmission. When SMB signing is enabled, each SMB packet includes a cryptographic signature that is verified by the receiving party.
Advantages of SMB Signing
Security: It helps prevent attackers from intercepting and tampering with SMB traffic, which can include sensitive information and authentication credentials.
Integrity: Ensures that the data transmitted over the network is not modified or corrupted in transit.
Disadvantages of SMB Signing
- Performance Impact: Enabling SMB signing can lead to poor networking performance due to the additional processing required for signing and verifying packets.
- Compatibility: Some older systems or applications may not support SMB signing, potentially leading to connectivity issues if it’s enforced.
SMB Signing Policy Settings
There are typically two key policy settings related to SMB signing:
Enable SMB Signing for Client and Server
Client Side: This setting determines whether the client will request SMB signing when communicating with the server.
Server Side: This setting determines whether the server requires SMB signing from clients.
You can configure SMB signing to be required, enabled but not required, or disabled.
Require SMB Signing for Client and Server
This setting forces SMB signing to be enabled and required for all SMB traffic. If this policy is applied, SMB communications will not be established without signing.
Best Practices
- Enable SMB Signing: This is for better security, especially in environments where sensitive data is transmitted.
- Require SMB Signing: In environments where data integrity and authenticity are critical.
- Monitor and Test: Regularly monitor the impact of SMB signing on network performance and compatibility and test configurations in a staging environment before widespread deployment.
By implementing and managing SMB signing policies effectively, you can enhance the security of SMB communications in your network and protect against various types of cyber threats.
Configuring SMB Signing
We are going to configure SMB signing for both the server and the client (Require and enable). To enable SMB signing for the client, follow these steps:
Navigate to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services as shown below
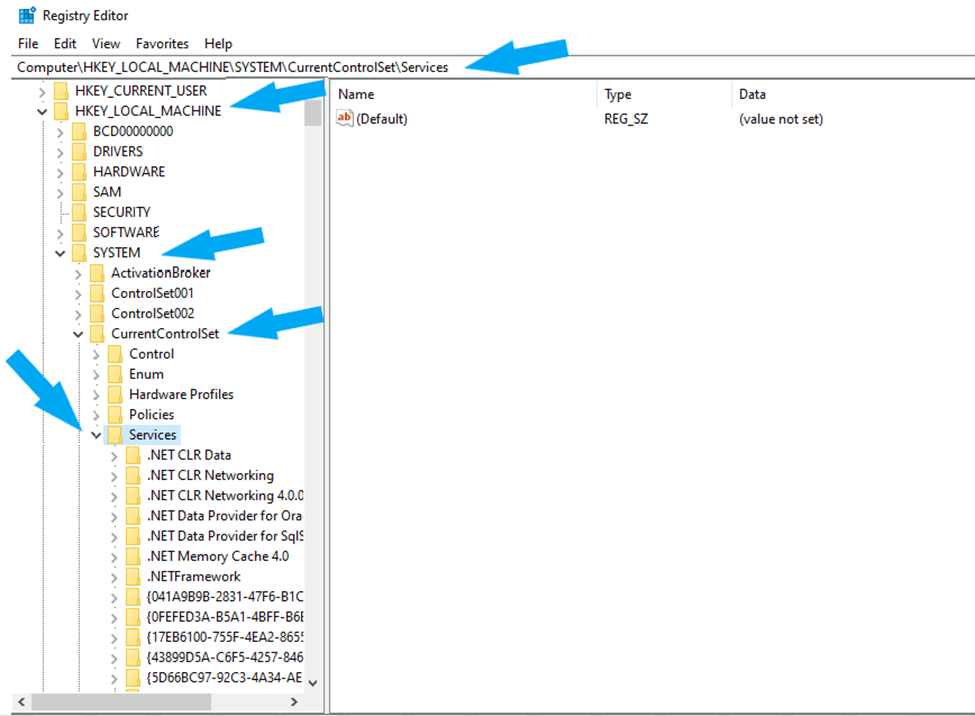
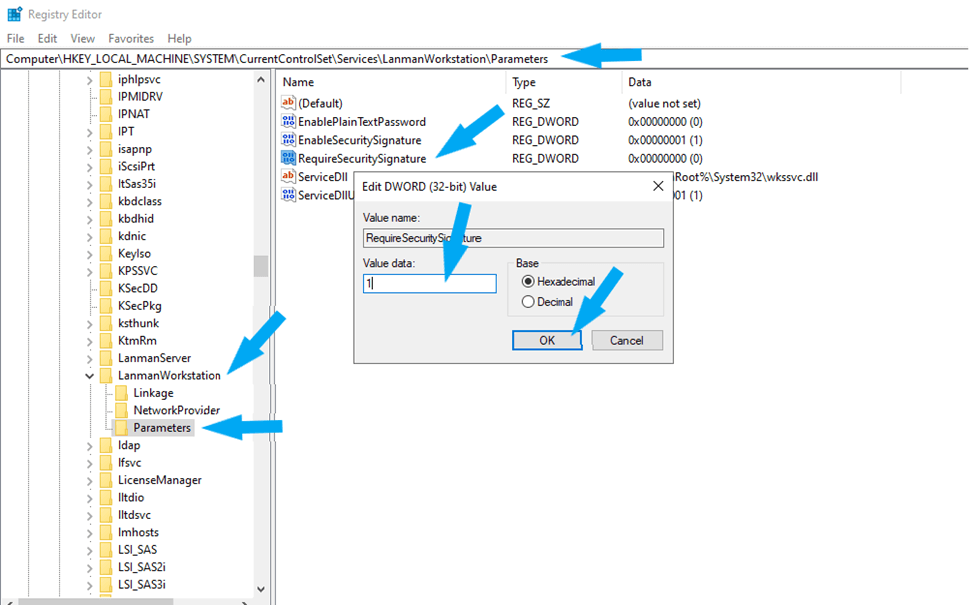
To configure the client to require SMB signing (RequireSecuritySignature). Locate \LanManWorkstation\Parameters and click on parameters.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\ ParametersOn the right side, click on the registry value RequireSecuritySignature to edit REG_DWORD, as shown below. Replace (0) with (1) to enable it. (0) means disable (1) means enable.
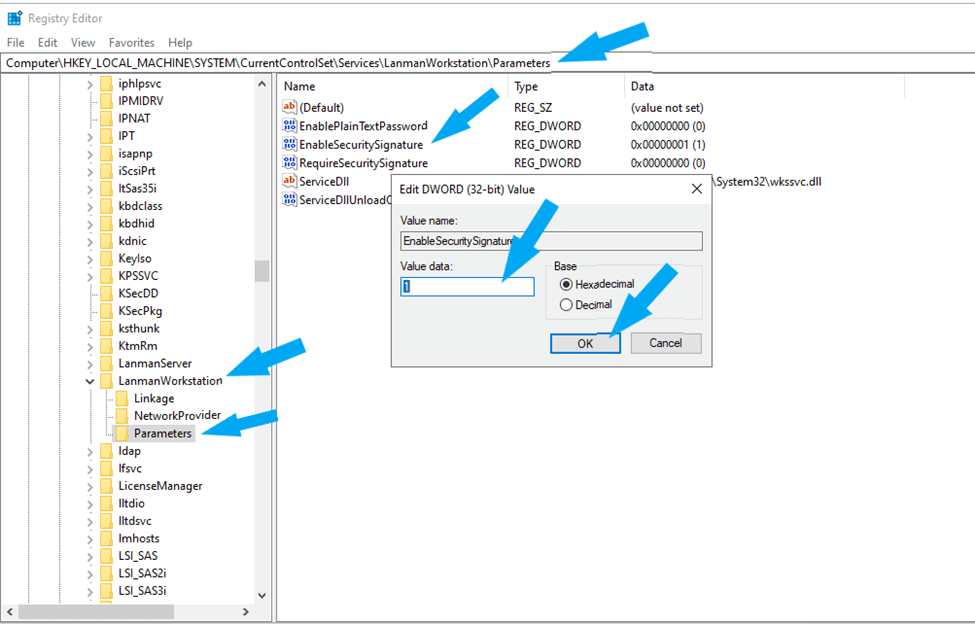
To configure the client to enable SMB signing (EnableSecuritySignature). Locate \LanManWorkstation\Parameters and click on parameters.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\ ParametersOn the right side, click on the registry value EnableSecuritySignature to edit REG_DWORD, as shown below. Replace (0) with (1) to enable it. (0) means disable (1) means enable.
To configure the server to enable SMB signing (EnableSecuritySignature). Locate \LanManWorkstation\Parameters and click on parameters.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\ LanManServer \ ParametersOn the right side, click on the registry value RequireSecuritySignature to edit REG_DWORD, as shown below. Replace (0) with (1) to enable it. (0) means disable (1) means enable.
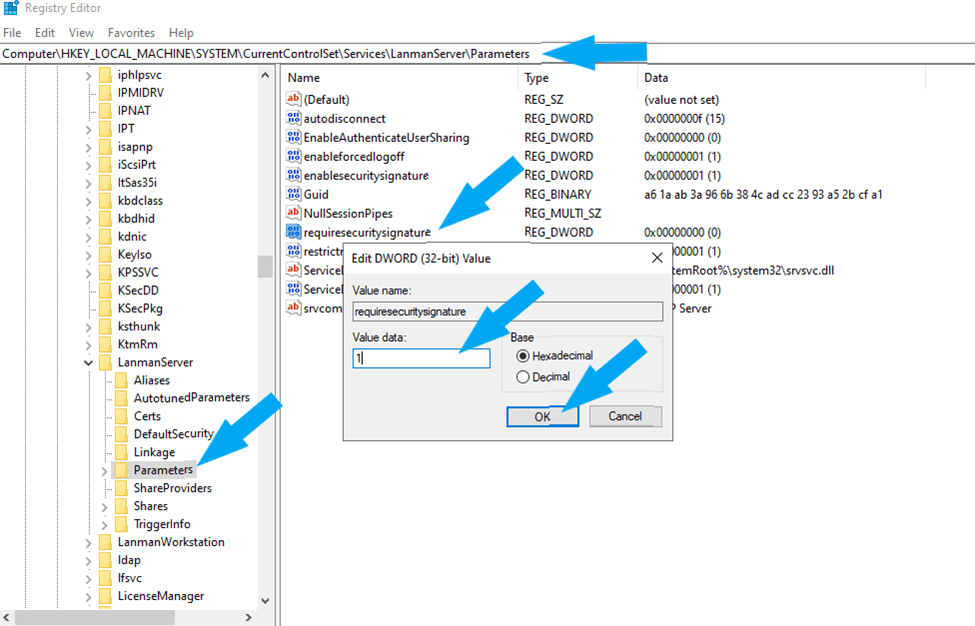
To configure the server to enable SMB signing (EnableSecuritySignature). Locate \LanManWorkstation\Parameters and click on parameters.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\ LanManServer \ ParametersOn the right side, click on the registry value EnableSecuritySignature to edit REG_DWORD, as shown below. Replace (0) with (1) to enable it. (0) means disable (1) means enable.
To disable SMB signing, simply follow the same steps listed above and replace (1) with (0) to disable it.
Conclusion
Implementing SMB signing is a crucial step in enhancing the security of network communications within Windows environments. By enabling SMB signing, organizations can protect against man-in-the-middle attacks and ensure the integrity of data transmitted over the network. While SMB signing introduces a slight performance overhead and may affect compatibility with older systems, the security benefits far outweigh these drawbacks. Enforcing SMB signing policies helps safeguard sensitive information and maintain a secure network environment. Organizations should regularly review and adjust their SMB signing settings to balance security needs with performance considerations, ensuring robust protection against potential cyber threats.
