Table Of Contents
- 1 Disable Persistent Browser Sessions in Microsoft Entra ID
- 2 What is a Persistent Browser Session?
- 3 Why Disable Persistent Browser Sessions?
- 4 Step-by-Step Guide to Disable Persistent Browser Sessions in Microsoft Entra ID
- 5 Verifying the Changes
- 6 Best Practices for Securing Sessions in Microsoft Entra ID
- 7 Conclusion
- 8 About The Author
Disable Persistent Browser Sessions in Microsoft Entra ID
In today’s digital landscape, user security is a top priority for organizations. Microsoft Entra ID, formerly known as Azure Active Directory (AAD), provides a robust suite of tools to manage identity and access. One of the critical features that can enhance security is the ability to control how sessions are handled. Disabling persistent browser sessions in Microsoft Entra ID can prevent unauthorized users from maintaining logged-in states across sessions, adding an extra layer of security to your environment.
In this post, I will walk you through the process of disabling persistent browser sessions in Microsoft Entra ID, ensuring that users must re-authenticate every time they access their accounts, thereby reducing the risk of unauthorized access.
What is a Persistent Browser Session?
A persistent browser session occurs when a user logs in to an application, and their session is saved across browser restarts. This means the user doesn’t have to log in again, even after closing and reopening the browser. While this is convenient for users, it can pose a significant security risk. If someone gains unauthorized access to the user’s device, they could potentially access sensitive applications without needing to authenticate again.
For organizations using Microsoft Entra ID, managing persistent sessions is vital for securing user accounts, especially in environments where devices may be shared or used by multiple individuals.
Why Disable Persistent Browser Sessions?
There are several reasons why you may want to disable persistent browser sessions:
- Enhanced Security: Prevents unauthorized access to applications, especially on shared or public computers.
- Compliance: Meets regulatory requirements for industries that need strict session management, such as healthcare or finance.
- Mitigating Risk: Reduces the chance of session hijacking or other attacks that rely on maintaining persistent sessions.
Disabling persistent sessions ensures users authenticate with each session, which helps safeguard against security threats.
Step-by-Step Guide to Disable Persistent Browser Sessions in Microsoft Entra ID
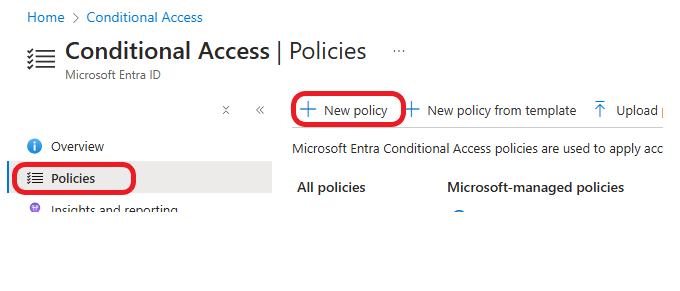
Log In to Microsoft Entra Admin Center using your admin credentials. Click on Protection > Conditional Access, as shown in the screenshot below.

Click on Policies > +New policy.
Give your policy a descriptive name so you can easily identify it later. Under Assignments, click on Users and select All Users under Include.

Click on Target resources and select All resources (formerly ‘All cloud apps’) under Include.

Click on Conditions > Client apps. Select Yes under Configure. For Modern authentication clients, check the box next to Browser to select it. Click Done.
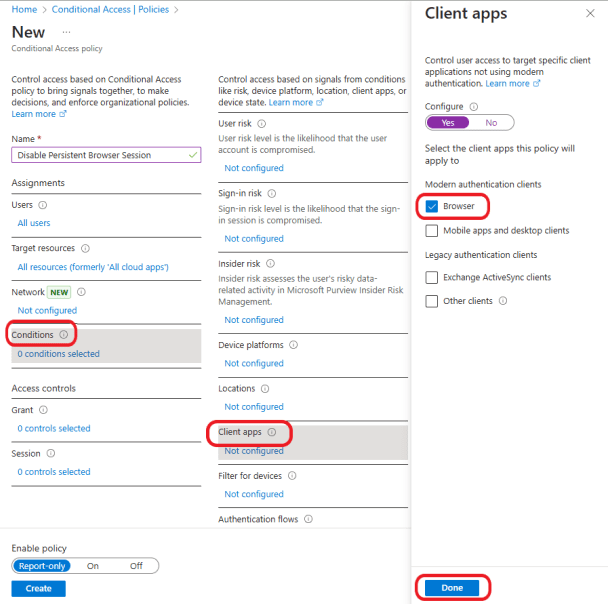
Under Access controls, click on Session.

Check the box next to the Sign-in frequency. Set the periodic reauthentication to 1, and select Hours. Check the box next to Persistent browser session to select it. Select Never persistent. Click on Select, as shown below.

Review all settings to ensure they align with your organization’s security requirements. Select On to enable it, and click on the Create button, as shown in the screenshot below.

The policy was created successfully, as shown in the screenshot below.

Verifying the Changes
After the policy is applied, it’s essential to verify that persistent sessions have been disabled.
Log in to an application integrated with Microsoft Entra ID. I will log in to Outlook for this example. Close the browser and reopen it, or leave it inactive for a while. Try to access the application again without logging in. If the settings are correct, the user should be prompted to authenticate again. See the screenshot below. You can also perform tests with different user roles to ensure the policy applies correctly across all users.

Best Practices for Securing Sessions in Microsoft Entra ID
- Enforce Multi-Factor Authentication (MFA): Complement session control with MFA to add another layer of security.
- Monitor Conditional Access Reports: Regularly check logs to ensure that the session policies are working as expected.
- Use Application Proxy: For added security, use Microsoft Entra Application Proxy to secure access to on-premises applications.
Conclusion
Disabling persistent browser sessions in Microsoft Entra ID is an effective way to improve security by ensuring users must authenticate each time they access critical resources. This action lowers the risk of unauthorized access in case of device theft or sharing, aligning with best security practices. By following the steps outlined above, you can configure your organization’s Microsoft Entra ID environment to provide more control over user sessions. With enhanced security, you can have greater confidence that your data and applications are protected.
