Table Of Contents
- 1 Configure Conditional Access to Block Legacy Authentication in Microsoft Entra ID
- 2 What is Legacy Authentication?
- 3 Why Block Legacy Authentication?
- 4 Steps to Configure Conditional Access to Block Legacy Authentication in Microsoft Entra ID
- 5 Test the Policy
- 6 Best Practices When Blocking Legacy Authentication
- 7 Conclusion
- 8 About The Author
Configure Conditional Access to Block Legacy Authentication in Microsoft Entra ID
In today’s rapidly evolving cybersecurity landscape, protecting your organization’s resources is more critical than ever. Microsoft Entra ID (formerly Azure AD) offers robust tools for managing access to corporate resources and safeguarding data. One such feature is Conditional Access, which can help enforce security policies across various platforms and applications. A common security measure is blocking legacy authentication, which is vulnerable to several types of cyberattacks, including brute-force attacks. In this blog post, I will walk you through how to configure Conditional Access to block legacy authentication in Microsoft Entra ID. This simple yet powerful step can significantly enhance the security posture of your organization.
What is Legacy Authentication?
Before diving into the configuration process, let’s understand what legacy authentication is and why it’s a potential risk.
Legacy authentication refers to older authentication protocols that do not support modern security features, like Multi-Factor Authentication (MFA). These protocols include:
- POP3
- IMAP
- SMTP
- Basic Authentication for Exchange, Outlook, and other apps
While these methods may still work, they lack built-in security mechanisms like MFA and conditional access policies. As a result, they are often exploited by attackers to gain unauthorized access to accounts.
Why Block Legacy Authentication?
Blocking legacy authentication is essential for securing your organization’s sensitive data. Some of the reasons include:
- Increased Security Risk: Legacy protocols do not support modern authentication methods like MFA, making accounts more susceptible to password spraying, brute-force, and phishing attacks.
- Compliance: Many industry compliance standards and regulations require organizations to adopt modern authentication methods to secure access to their resources.
- Reduced Attack Surface: By blocking legacy authentication, you reduce the number of potential entry points for attackers, ultimately strengthening your overall security.
Steps to Configure Conditional Access to Block Legacy Authentication in Microsoft Entra ID
Follow these steps to configure Conditional Access and block legacy authentication in Microsoft Entra ID:
Login to Microsoft Entra ID with your admin credentials. Click Protection > Conditional Access on the left-hand pane, as shown below.
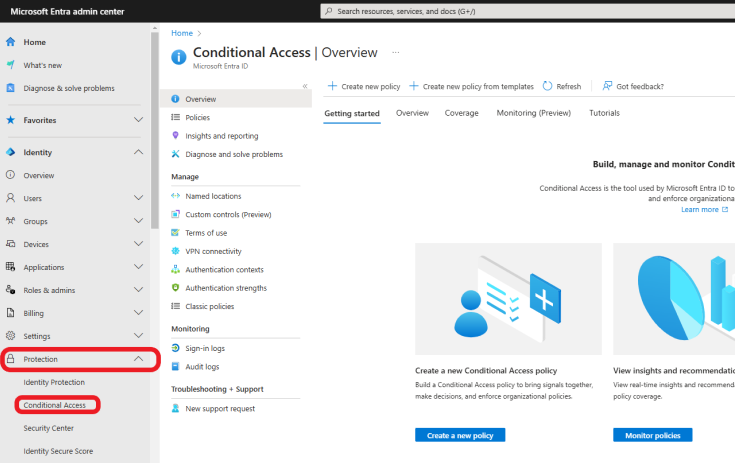
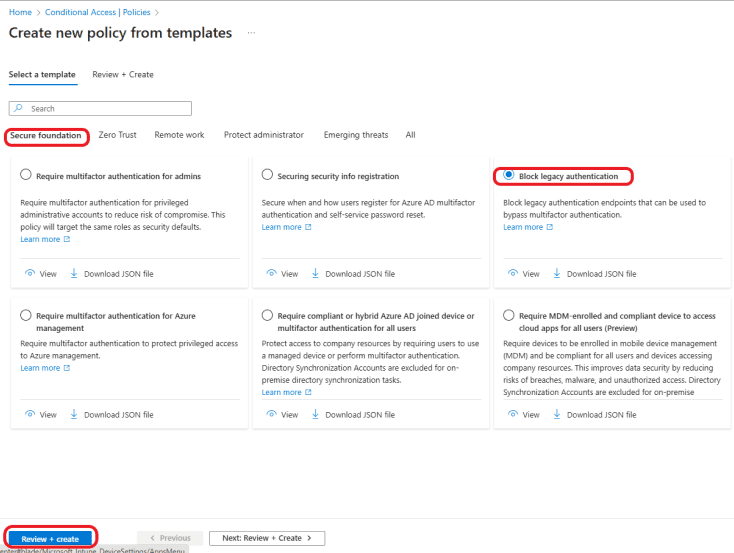
Click on Policies +New policy from the template to create a policy leveraging the Microsoft built-in template.

Under Secure foundation, choose Block legacy authentication. Click on Review + Create.
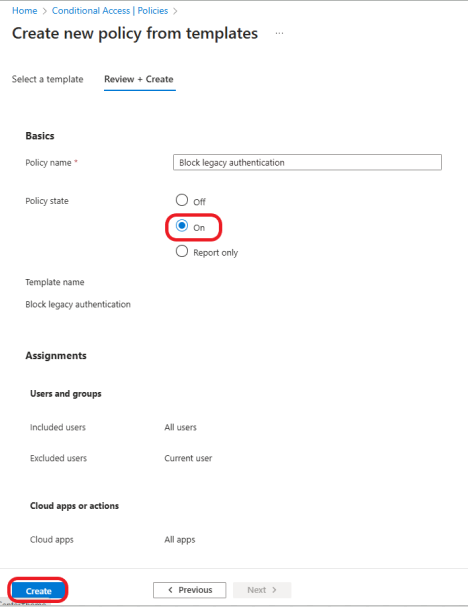
For the Policy state, select On to enable the policy. Review the policy and click on the Create button. This is a very straightforward policy. This policy applies to all users and excludes your admin account (The account you are currently logged in with). Targeting
All resources (formerly ‘All cloud apps. And Blocking access for Exchange ActiveSync clients and other clients, including older office clients and other mail protocols(POP, IMAP, SMTP, etc
Test the Policy
- It’s important to test the policy to ensure it works as expected. You can use a test account to try logging in with legacy authentication methods to verify that access is blocked.
- You may also want to enable Report-only mode for a period of time to monitor the impact of the policy before fully enforcing it.
Best Practices When Blocking Legacy Authentication
Blocking legacy authentication can have a significant impact on your organization’s access patterns. Follow these best practices to ensure an easy and smooth transition:
- Pilot Group: Always test the policy on a small group of users before rolling it out organization-wide. This helps identify any potential issues and reduce disruptions.
- Monitor Authentication Logs: Use the sign-in logs in Microsoft Entra ID to track authentication attempts. Look for any errors or failed login attempts that could indicate users are still trying to authenticate with legacy protocols.
- Communicate with Users: Inform the users about the upcoming changes, especially if they rely on legacy apps that may be impacted by the new policy. Consider providing support or training on modern authentication methods.
Conclusion
Configuring Conditional Access to block legacy authentication in Microsoft Entra ID is a critical step toward enhancing your organization’s security. By taking this proactive measure, you can mitigate the risks associated with outdated and vulnerable authentication protocols. As a part of a broader security strategy, blocking legacy authentication ensures your users are adopting more secure, modern authentication methods, helping protect your organization’s data from potential threats. Stay ahead of cyber threats by embracing modern security practices.
