Table Of Contents
- 1 Configure an Access Control Policy to Block Access from Unauthorized Locations in Entra ID
- 2 What is Entra ID?
- 3 Why Block Access from Unauthorized Locations?
- 4 Disable Microsoft security defaults in Microsoft Entra ID
- 5 Create Approved Counties in Microsoft Entra ID
- 6 Create a New Conditional Access Policy to Block Unapproved Countries
- 7 Enable the Policy
- 8 Test the Effectiveness of the Policy
- 9 Best Practices for Configuring Location-Based Access Control in Entra ID
- 10 Conclusion
- 11 About The Author
In today’s digital age, ensuring the security of your organization’s data is paramount. One of the most effective ways to protect against unauthorized access is by setting up location-based access control policies. With Entra ID, you can easily configure these policies to block users from accessing your system from unauthorized or suspicious locations. This guide walks you through the steps of configuring and applying an access control policy in Entra ID to block access from unauthorized locations. Let’s dive in!
What is Entra ID?
Entra ID, formerly known as Azure AD, is a cloud-based identity and access management service that helps businesses manage user identities, access to applications, and security across their environment. It offers features like conditional access policies, multi-factor authentication, and security reports to help protect your organization’s sensitive data.
Blocking access based on geographic location is one of the most effective ways to mitigate risks related to unauthorized logins. Here are a few reasons why location-based access control is crucial:
- Prevent Data Breaches: Block access from high-risk or unfamiliar regions.
- Comply with Regulatory Standards: Certain industries require location-based access control for compliance.
- Enhance Security: Limit the possibility of login attempts from unauthorized IP addresses or locations.
Entra ID offers an easy-to-use interface to configure access control policies that restrict or allow access based on the user’s location.
Disable Microsoft security defaults in Microsoft Entra ID
To use a conditional access policy. You will need to turn off Microsoft security defaults. Follow the following steps to turn off Microsoft security defaults:
In Microsoft Entra ID, click on Identity >Overview >Properties >Manage security defaults. Select Disabled (not recommended) and Click the Save button.
Create Approved Counties in Microsoft Entra ID
Click on Named locations on the left pane of the Conditional Access page. Click on Countries location, give your new location a name, select Determine location by IP address (IPv4 and IPv6), Search for the country or countries you want to allow and select them. I will select the United States for this example. Click on the Create button, as shown below.

Create a New Conditional Access Policy to Block Unapproved Countries
From the Microsoft Entra ID admin center, click on Protection >Conditional access.
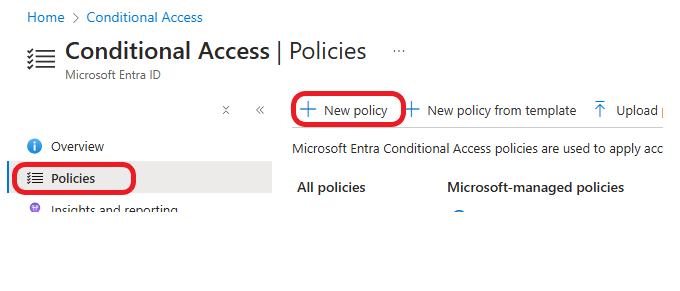
Click on Policies >New Policy at the top of the Conditional Access page, as shown below.
You’ll be prompted to give your policy a name. Choose a descriptive name, such as Block Unauthorized Locations, to help you identify it later. Under the Assignments section, select the Users and Groups to which the policy will apply. You can apply it to all users and specific groups or select individual users based on your security needs. For this example, select All users.

Click on Exclude > User and groups. Search for your username, click on it, then click on Select to exclude yourself.

As shown here

Click on Target resources, and select All resources (formerly ‘All cloud apps’) under Include.

Click on Network, Click Yes under Configure, and select Any network or location under Include, as shown below.

Still, under Network, click Exclude >Select networks and locations. select the approved country created earlier and click Save, as shown below.

Click on Conditions and select Locations. Click Yes under Configure, and select Any network or location.

Click on Exclude > Selected networks and locations. Search for the Approved Country created earlier, click on it to select it, then click on Save to exclude the approved country (United States).

Still, under the Conditions, click on Client apps > select Yes under Configure. Select the client apps to which you want the policy to apply. For this example, I will select Browser and Mobile apps and desktop clients, as shown below. Click Done.

Next, we are going to make some exceptions. This is for situations like when your CEO travels outside the United States and wants to work remotely. Select Exclude filtered devices from policy and set a rule. Property >IsComplaint, Operator >Equals, Value >True. Click Done. This rule will allow access from outside the United States if complaint.

Click on Grant >Block access >Select.

Enable the Policy
Click On, as shown below, to enable the policy. Click on the Create button.

The policy was created and enabled successfully.

Test the Effectiveness of the Policy
Before rolling out the policy organization-wide, it’s always a good idea to test it with a small group of users to ensure everything is working as expected. For this example, you will need to change your location. I changed my country to Canada using a VPN. Then, I tried to log in to one of the test user accounts.

The policy works as expected. Below is the message I received.

Best Practices for Configuring Location-Based Access Control in Entra ID
- Monitor and Review Policies: Continuously review and update your access policies to ensure they remain effective and aligned with organizational needs.
- Leverage Multi-Factor Authentication (MFA): Even with location-based restrictions, enable MFA for another layer of security.
- Apply Least Privilege: Restrict access based on the least privilege principle, allowing access only to users and locations necessary for their role.
Conclusion
Blocking access from unauthorized locations is a proactive measure to safeguard your organization’s sensitive data and ensure only trusted users have access to critical resources. With Entra ID’s Conditional Access policies, you can easily configure location-based access controls and apply them to specific users, groups, or applications. By following this guide, you can implement a strong security layer that minimizes the risk of unauthorized access from suspicious locations.
