Table Of Contents
- 1 Configure a Conditional Access Policy to Enforce Multi-Factor Authentication to Protect Office 365 in Microsoft Entra ID
- 2 What is Conditional Access?
- 3 Why Use MFA with Conditional Access?
- 4 Prerequisites
- 5 Disable Microsoft security defaults in Microsoft Entra ID
- 6 Steps to Configure Conditional Access to Require MFA for All Use
- 7 How to Configure Custom Conditional Access to Require Multi-Factor Authentication
- 8 Configure Multi-factor Authentication Methods in Microsoft Entra ID
- 9 Test the Effectiveness of the Multifactor Authentication Policy
- 10 Conclusion
- 11 About The Author
Configure a Conditional Access Policy to Enforce Multi-Factor Authentication to Protect Office 365 in Microsoft Entra ID
In today’s digital landscape, securing access to sensitive company data is more important than ever. While usernames and passwords are still widely used, they are not enough on their own to protect accounts from cyber threats. Multi-factor authentication (MFA) provides another layer of security that can significantly lower the risk of unauthorized access.
One powerful tool for enforcing MFA across an organization is Conditional Access. In this post, I will guide you through the steps to configure a Conditional Access Policy to require MFA for all users in your Microsoft 365 environment.
What is Conditional Access?
Conditional Access is a feature in Entra ID that allows administrators to control access to applications based on specific conditions. These conditions can include factors like user location, device state, or the type of app being accessed. Conditional Access can be used to enforce security policies, such as requiring Multi-Factor Authentication, to make sure that only authorized users have access to certain resources.
Why Use MFA with Conditional Access?
While passwords are still the primary method for user authentication, they are vulnerable to various types of attacks like phishing, brute force, and credential stuffing. By requiring Multi-Factor Authentication (MFA), you add an extra layer of security that makes it much more harder for attackers to gain access to an account.
When you configure a Conditional Access policy to require MFA, you can:
- Reduce the risk of account compromise: Even if an attacker has stolen a password, they will not be granted access without the second factor of authentication.
- Enforce consistent security measures: MFA can be enforced uniformly across your organization, regardless of the user’s location or the device they’re using.
- Comply with regulations: Many industries require multi-factor authentication as part of data protection and security compliance standards.
Prerequisites
Before you configure a Conditional Access policy for MFA, ensure you meet these requirements:
- Entra ID P1 or P2: Conditional Access is available only to organizations with an Entra ID Premium subscription.
- MFA Enrolled Users: Ensure all users who will be subject to MFA have enrolled in the service. Users will need to set up their second factor, like a mobile phone, authenticator app, or hardware token.
- Admin Privileges: You must have global administrator or security administrator privileges to configure Conditional Access policies.
Disable Microsoft security defaults in Microsoft Entra ID
To use a conditional access policy. You will need to turn off Microsoft security defaults. Follow the following steps to turn off Microsoft security defaults:
In Microsoft Entra ID, click on Identity >Overview >Properties >Manage security defaults. Select Disabled (not recommended) and Click the Save button.
Steps to Configure Conditional Access to Require MFA for All Use
You can access the Microsoft Entra ID admin center from Azure or Microsoft Office 365 admin center.
To access the Microsoft Entra ID admin center from Azure, click on Microsoft Entra ID from the left-hand pane or search for Microsoft Entra ID in the search box. To access the Microsoft Entra ID admin center from the Microsoft Office 365 admin center, click on Show all, then click on Identity.
You can configure conditional access from the Microsoft Entra ID admin center or from the Microsoft Intune admin center.
To configure conditional access from the Microsoft Intune admin center, Click on Endpoint Security>Conditional access.

To configure access control from the Microsoft Entra ID admin center, click on Protection >Conditional access.
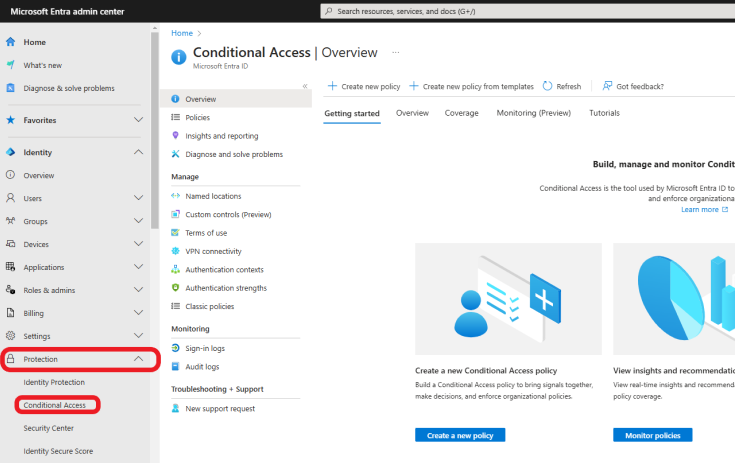
Next, we are going to create a conditional access policy to require MFA for all users using the provided template
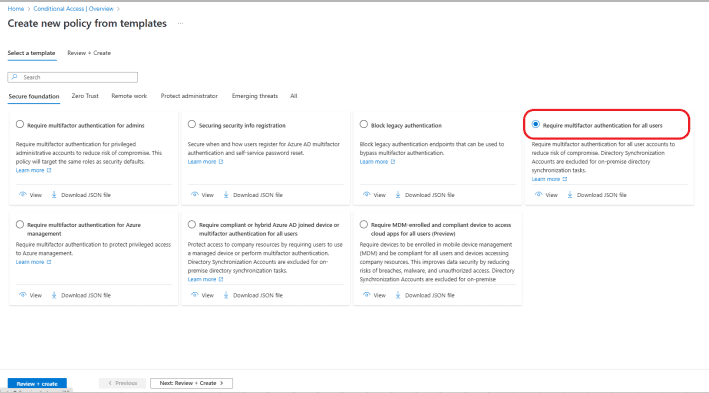
Click on Create new policy from templates.

Select Require multifactor authentication for all users and click on the Review + Create button.
Update your policy name as needed. We are not ready to turn the policy on yet, so select Report Only and click on the Create button.

How to Configure Custom Conditional Access to Require Multi-Factor Authentication
To configure access control from the Microsoft Entra ID admin center, click on Protection >Conditional access.
Click on New policy.

Give your policy a name. Click on users and select All users under Include, as shown below. You can select users and groups to assign the policy to groups. See the second method below.

Under the Assignments section, click Users and groups. Select All users to apply this policy to everyone in your organization. You will need to create the All User group if you haven’t already. Optionally, you can exclude certain users or groups (e.g., service accounts or emergency accounts), but for enforcing MFA universally, select all users.

Click on Target resources and select All resources (formerly ‘All cloud apps’) under Include, as shown below.

Click on Grant and select Grant access. Check the box next to Require multifactor authentication and click Select, as shown below. Click the Create button.

Configure Multi-factor Authentication Methods in Microsoft Entra ID
Now, let’s configure the Multi-factor Authentication methods that we want users to use to authenticate. You can enable as many MFA methods as possible based on your needs. For this example, I will configure Microsoft Authenticator and Passkey (FIDO2).
How to Configure Microsoft Authenticator as an Authentication Method in Microsoft Entra ID
Click on Protection >Authentication methods >Policies >Microsoft Authenticator, as shown below.

Click on the Enable toggle to enable the policy. You can choose Select groups if you want to target groups. For this example, Select All users under Include. You can make further changes by clicking on Configure but leaving it as default for this example. Click on the Save button.

How to Configure Passkey FIDO2 as an Authentication Method in Microsoft Entra ID
Click on Protection >Authentication methods >Policies >Passkey (FIDO2), as shown below.

Click on the Enable toggle to enable the policy. You can choose Select groups if you want to target groups. For this example, Select All users under Include.

Click on Configure, Allow self-service set up >Yes, Enforce attestation >No, Enforce key restrictions >No. Click on the Save button.

Now that we have our multifactor authentication methods configured, we are ready to enable the Require multifactor authentication for all users‘ policy created earlier.
Click on Policies > Require multifactor authentication for all users.

Click on the On and click on the Save button.

Test the Effectiveness of the Multifactor Authentication Policy
Now that the policy is enabled let’s test it. I will try to log in to Office 365 with one of the testing user accounts I created.

The policy works as expected with only two multi-factor authentication methods as configured.

Conclusion
Configuring a Conditional Access policy to enforce Multi-Factor Authentication for all users is an effective way to enhance the security of your organization’s Microsoft 365 environment. By implementing MFA, you reduce the likelihood of unauthorized access, safeguard sensitive data, and ensure that your company complies with regulatory requirements. With Azure Active Directory’s Conditional Access policies, enforcing MFA across your organization is straightforward, customizable, and scalable.
