Table Of Contents
- 1 How to Configure a Conditional Access Policy to Block Unapproved Devices in Microsoft Entra ID
- 2 Why Block Unapproved Devices in Microsoft Entra ID?
- 3 Prerequisites
- 4 Disable Microsoft Security Defaults
- 5 Create a Conditional Access Policy in Microsoft Entra ID to Block Unapproved Devices
- 6 Test the Policy
- 7 Monitor and Refine
- 8 About The Author
How to Configure a Conditional Access Policy to Block Unapproved Devices in Microsoft Entra ID
In an era where data security is paramount, managing access to your organization’s resources is one of the most crucial tasks an IT administrator can perform. Microsoft Entra ID (formerly Azure Active Directory) offers powerful tools to ensure that only trusted users and devices can access your critical applications and sensitive data. One such tool is Conditional Access, which allows administrators to create rules that determine how and when users can access resources based on specific conditions.
In this blog post, I will walk you through how to configure a Conditional Access Policy in Microsoft Entra ID to block unapproved devices, thereby enhancing your organization’s security posture.
Why Block Unapproved Devices in Microsoft Entra ID?
Unapproved devices can pose a significant security risk, especially when accessing corporate resources such as email, files, or applications. Blocking unapproved devices helps to mitigate risks such as:
- Unauthorized Access: Unapproved or compromised devices may not meet your security requirements, leaving your organization vulnerable to data breaches.
- Compliance Violations: Regulatory frameworks like GDPR and HIPAA require organizations to ensure only secure, trusted devices access sensitive data.
- Malware and Threats: Unapproved devices might not have the latest security patches or malware protection, making them an easy target for cyberattacks.
By blocking unapproved devices using Conditional Access policies in Microsoft Entra ID, you can enforce strict security measures and ensure that only compliant devices can access your resources.
Prerequisites
Before you can configure a Conditional Access policy to block unapproved devices in Microsoft Entra ID, ensure the following:
- Microsoft Entra ID Premium P1 or P2 Subscription: Conditional Access is only available with a Premium P1 or P2 subscription.
- Admin Rights: You must have administrative privileges to configure Conditional Access policies.
- Device Compliance Policies: Make sure your organization has already configured device compliance policies that define the security requirements for devices accessing your resources.
Disable Microsoft Security Defaults
To use a conditional access policy. You will need to turn off Microsoft security defaults. Follow the following steps to turn off Microsoft security defaults.
In Microsoft Entra ID, click on Identity >Overview >Properties >Select Manage security defaults >Set Security defaults to Disabled (not recommended). Click the Save button.
Create a Conditional Access Policy in Microsoft Entra ID to Block Unapproved Devices
Sign In to the Microsoft Entra ID Admin Center with your administrative credentials. From the left-hand menu, click on Protection and click on Conditional Access, as shown below.
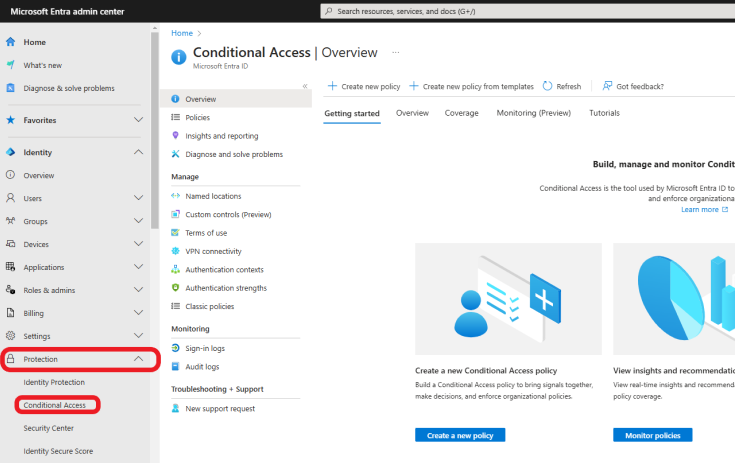
Click on Policies, then + New Policy to start creating your new policy.

Give your policy a clear, descriptive name, such as “Block Unapproved Device type.”
Under Assignments, select users to specify the users to whom the policy will apply. You can apply the policy to all users or target specific groups such as admins, contractors, or employees.
- Tip: Start by applying the policy to a small group or a test user to avoid disrupting the entire organization.
For this example, I will apply the policy to all users. Under Include, select All users.

Click on Target resources, and under Include, select All resources (formerly ‘All cloud apps’).

Click on Conditions, then click Device Platforms. Select Yes under Configure. Under Include, choose Select device platforms. Select the device types that are not used in your organization.

Click on Grant >Block access to block access to the device type specified in the previous step. Click on Select as shown below.
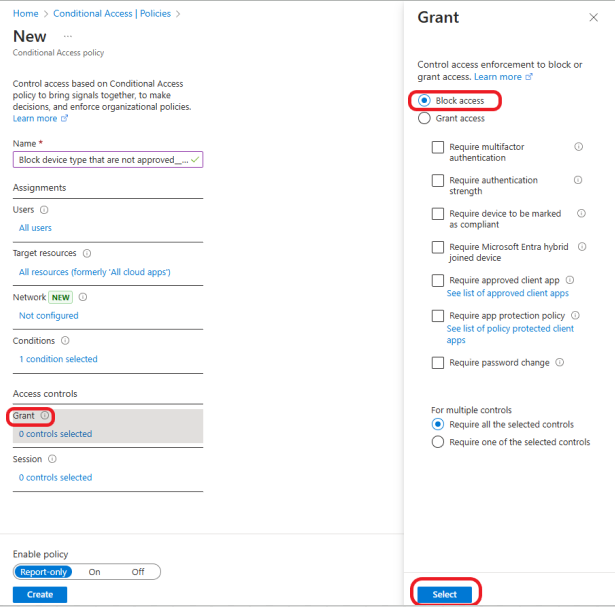
Review the policy, select On to enable the policy, and click on the Create button.

The policy was created and enabled successfully, as shown below.
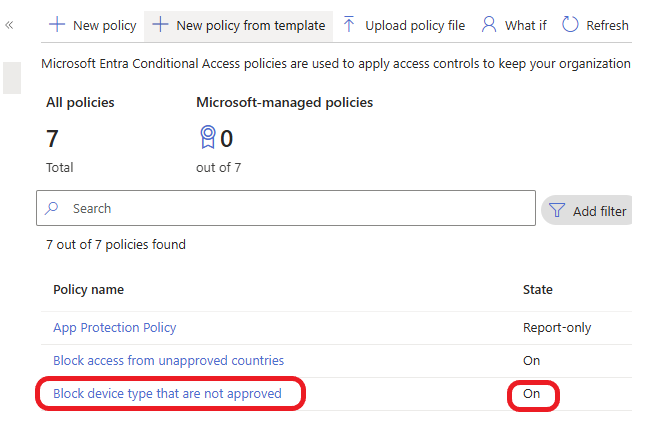
Test the Policy
Before enforcing this policy across your organization, you should test it with a pilot group. This will allow you to verify that the policy is blocking unapproved devices without causing any unintended disruptions.
- Apply the policy to a test group and attempt to access the selected cloud apps from the blocked device type to ensure the policy works as expected.
- Ensure that the devices being blocked are indeed non-compliant or unapproved based on your security.
Monitor and Refine
Once the policy is live, regularly monitor its effectiveness through the Sign-in logs and Audit logs in the Microsoft Entra ID Admin Center. Review reports to ensure that the policy is blocking unauthorized devices and not interfering with legitimate users.
Best Practices for Managing Conditional Access Policies
Here are some best practices to consider when configuring Conditional Access policies in Microsoft Entra ID:
- Leverage Multi-Factor Authentication (MFA): Combine Conditional Access policies with MFA to add an extra layer of security.
- Use Device Compliance Policies: Ensure that devices meet your compliance requirements, such as encryption, antivirus software, and OS updates, before granting access.
- Regularly Review Policies: As your organization evolves, periodically review and update your policies to ensure they still align with your security and compliance goals.
- Test Policies Before Full Deployment: Always test new policies with a small group of users before applying them organization-wide.
- Educate Users: Ensure users are aware of the device access policies and understand the importance of using compliant devices.
Conclusion
Blocking unapproved devices through a Conditional Access policy in Microsoft Entra ID is an effective way to safeguard your organization’s resources and sensitive data. By following the steps outlined in this guide, you can implement a robust access control strategy that will ensure that only trusted devices can access your critical applications.
