Table Of Contents
- 1 Analyze a Malware Incident in CrowdStrike Falcon
- 2 What is CrowdStrike Falcon?
- 3 Why Analyze Malware Incidents in CrowdStrike Falcon?
- 4 Step-by-Step Guide to Analyzing a Malware Incident in CrowdStrike Falcon
- 5 Investigate
- 6 1. Details
- 7 2. Process Table
- 8 3. Process Tree
- 9 4. Process Graph
- 10 5. Events Timeline
- 11 Containment
- 12 Best Practices for Malware Incident Analysis in CrowdStrike Falcon
- 13 Conclusion
- 14 About The Author
Analyze a Malware Incident in CrowdStrike Falcon
Malware incidents can be one of the most devastating events for organizations, leading to data breaches, system downtime, and potential financial losses. That’s why having the right tools to identify, investigate, and respond to malware attacks is crucial. CrowdStrike Falcon, a leading cybersecurity platform, is designed to help businesses detect, prevent, and respond to advanced cyber threats, including malware attacks. In this guide, I will walk you through how to analyze a malware incident using CrowdStrike Falcon, ensuring you can quickly identify the threat and take effective action.
What is CrowdStrike Falcon?
CrowdStrike Falcon is a cloud-native endpoint protection platform that offers real-time protection and advanced threat intelligence. It provides multiple layers of security, including malware detection, behavioral analysis, and incident response capabilities. With Falcon, you can monitor endpoints, detect suspicious activities, and respond to potential threats with actionable insights.
Why Analyze Malware Incidents in CrowdStrike Falcon?
Analyzing malware incidents effectively is essential for several reasons:
- Prevent Further Damage: Prompt analysis helps limit the spread of malware.
- Understand the Attack: By identifying the malware’s behavior, you can prevent similar future incidents.
- Meet Compliance Requirements: Many industries have compliance standards that require thorough incident analysis and reporting.
Step-by-Step Guide to Analyzing a Malware Incident in CrowdStrike Falcon
To begin analyzing a malware incident, log in to the CrowdStrike Falcon Console. This central hub gives you access to all security data and tools to investigate and manage incidents.
Click on the hamburger button on the top left. Click on Endpoint security, then click on Activity Dashboard, under the Monitor section.

On the dashboard, you will see Current CrowdScore, New detections, SHA-based detections, Prevented malware by host, Total OverWatch-analyzed events, OverWatch endpoint hunting leads, OverWatch endpoint detections triggered, CrowdScore over time, Most recent detections, and Detections by tactics.
Click on New detections, as shown below.

This page provides detection, categorized by severity level and detail such as Severity, Detect time, Name, Attributes, Assigned to, Resolution, and Status.
Click on the Sort by Time drop-down arrow to sort based on your needs.

Click on the Group by drop-down arrow to group the incident based on your needs.

Configure table columns.
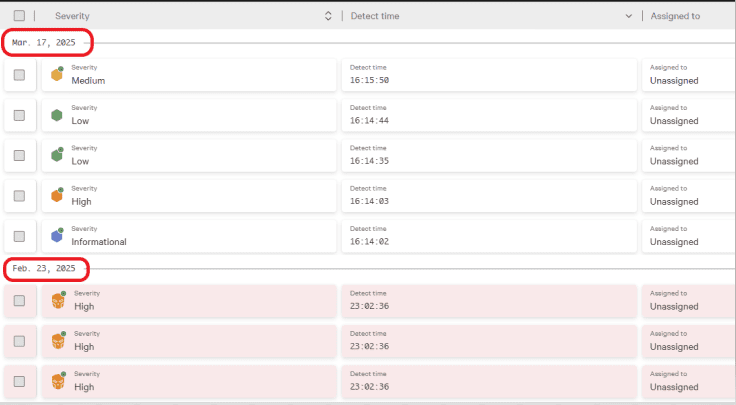
Notice there are incidents with different dates. Let’s investigate the incident that occurred on Feb 23, 2025, with High severity.
Click on the ellipsis located on the right side of the incident you are working on and select Edit Status to assign the incident and update the status. As shown below.

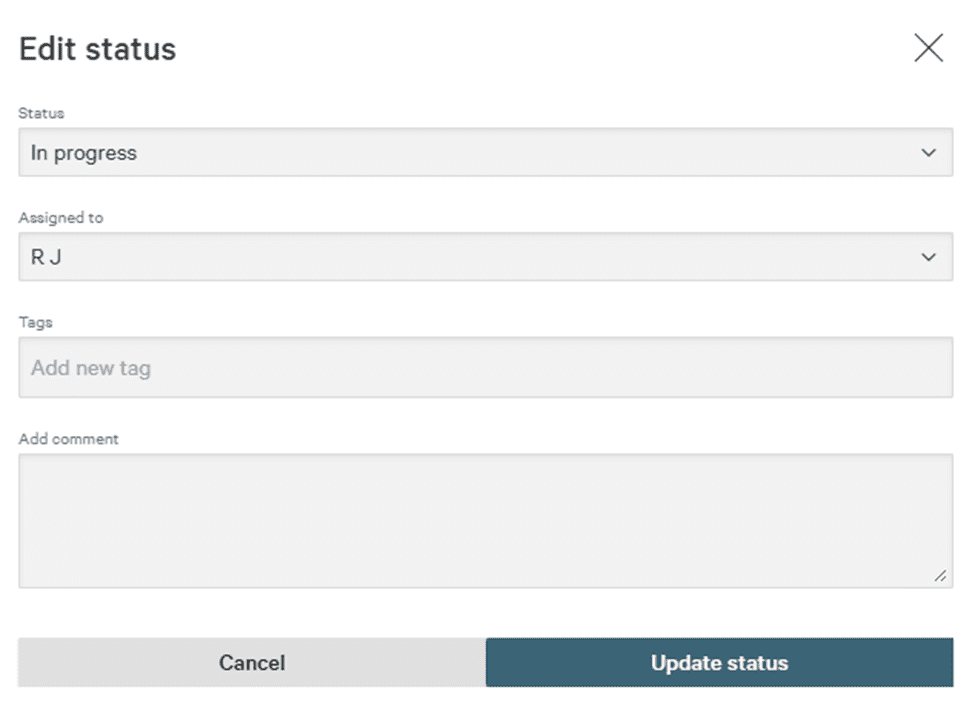
Change the status to In progress and assign it to yourself. Click on Update status, as shown below.
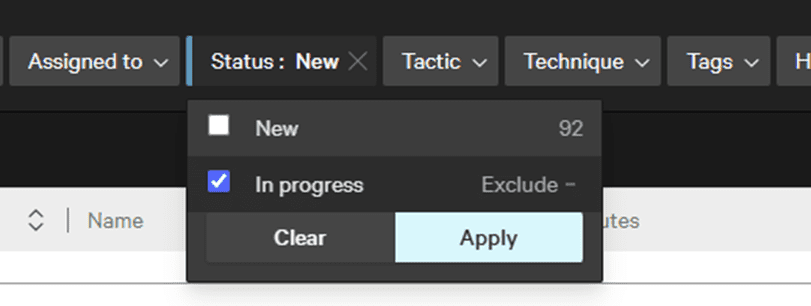
Click on the Status tab, uncheck New, and select In Progress to see the incident you just updated. Click Apply.
You should see the assigned incident listed with in-progress status, as shown below. Click on the incident.

Look through the Process table. We will learn more about it later.

Investigate
Click on Investigate on the top right and select an option based on your needs. These investigation options are essential for effective incident response, allowing security teams to analyze hosts, events, and potential threats in depth. Learn about their uses below:
- See Host Information: This option allows you to view detailed information about a specific host (a machine, server, or endpoint) that could be relevant to an investigation. This includes system details like hostname, host ID, last seen, first seen, platform, OS version, type, local IP, external IP, MAC address, sensor version, host groups, grouping tags, last logged user account, prevention policy, sensor update policy, content update policy, and host retention policy. Essentially, it helps in gathering contextual information about the host involved in an incident.
- Investigate Host: This option provides more information about the host. You can get details such as computer name, real-time response, MAC, local IP, AIP, product type, version, manufacturer, model, domain, site name, agent version, AID, and BIOS information.
- Investigate Event: Investigating events gives you the tools to explore specific security events. You can use the search function to run queries, find dashboards, lookup files, and more.
- Investigate Hash: A hash is a unique identifier for a file or a piece of data, typically used for integrity checking and identifying malicious files. Investigate hash allows you to look up the hash value of the suspicious file to see if it’s associated with any known malicious activity. Searching the hash in Falcon can tell you whether the file has been flagged as part of a known threat, whether it’s linked to a specific malware campaign, or if it exhibits any suspicious characteristics.

Click on See full detection.

There are five tabs at the top of this page: Details, Process Table, Process Tree, Process Graph, and Events Timeline. Let’s learn about them.

1. Details
The Details tab provides detailed information about the incident. These could include Adversaries, Full details, Hash, Quarantined files, Host, and User. The suspicious file has been quarantined by CrowdStrike Falcon, as shown in the screenshot below.
Triggering indicator Associated IOC (File write)
Click on the Details tab and scroll down to File details. Under the Triggering indicator Associated IOC (File write) section, we can see the Command line, File path, and File hash.
What is an Indicator of Compromise (IOC)?
An Indicator of Compromise (IOC) is a piece of forensic data or a specific event that points to potential malicious activity or a security breach. When a File Write IOC is triggered, it indicates that CrowdStrike Falcon or a similar security platform has detected suspicious file creation, modification, or movement in a location that could be indicative of malicious activity. These IOCs are important for threat hunting, forensic investigations, and incident response.
Explanation of the Associated Indicator of Compromise IOC
Command line “C:\Windows\Explorer.EXE” /NoUACCheck
- The command “C:\Windows\Explorer.EXE” /NoUACCheck is used to launch Windows Explorer (Explorer.EXE) with a specific option to bypass the User Account Control (UAC) prompt.
File path: \Device\HarddiskVolume3\Users\Administrator\Downloads\mimikatz_trunk (1)\Win32\mimikatz.exe
- The path \Device\HarddiskVolume3\Users\Administrator\Downloads\mimikatz_trunk (1)\Win32\mimikatz.exe points to the Mimikatz executable file. This path refers to a downloaded or extracted version of Mimikatz in the Downloads folder. Mimikatz is a post-exploitation tool developed by Benjamin Delpy. It is used by attackers, red teamers, and security professionals to dump credentials from memory, extract hashes, and perform various actions related to Windows authentication.
- \Device\HarddiskVolume3\: Indicates the file is on the third physical volume/partition of the disk, which could correspond to a system partition like C:.
- Users\Administrator\Downloads\: Shows the file is in the Administrator’s Downloads folder, a common location for downloaded files.
- mimikatz_trunk (1)\Win32\: Suggests the file is from the Mimikatz project. The folder name indicates it may be a downloaded or extracted version of Mimikatz. The Win32 folder refers to the 32-bit version of Mimikatz.
- mimikatz.exe: This is the Mimikatz executable, a tool used to dump credentials, extract hashes, and interact with Windows authentication systems.
File Hash: (SHA256 on file write) 94795fd89366e01bd6ce6471ff27c3782e2e16377a848426cf0b2e6baee9449b
- To investigate and validate whether this file is malicious or not, the SHA-256 hash of the written file can be used. If the hash matches a known malicious hash, you can confirm that the file is malicious and take appropriate action. Copy the file hash.

Go to Virustotal.com, paste the hash into the search bar, and press enter to check the integrity of the file.

2. Process Table
The Process Table shows information about processes, including their executable filenames, parent processes, and other relevant details. The table provides a detailed view of all processes, which is crucial for detecting suspicious activity, such as abnormal or unauthorized processes running on the system.
Click on the Process Table tab to learn more about the incident.

3. Process Tree
The Process Tree is a hierarchical visualization of how processes are related to each other. It shows the parent-child relationship between processes. Each process is spawned by another, forming a tree structure. This visualization helps security analysts trace the origin of suspicious processes and understand how an attack or malware might be spreading or executing.
Click on the Process Tree tab. Here, you can see all the entities involved in the incident. For this example, five entities are involved, as shown below. Click on each entity to learn more.

4. Process Graph
The Process Graph is a visual representation of processes and their interactions over time. It is similar to the process tree. The process graph is useful for detecting complex attack behaviors, such as multi-stage attacks, by visualizing the sequence and relationships of processes.

5. Events Timeline
The Events Timeline is a chronological view of system events, which helps analysts understand the sequence of actions that occurred on the endpoint. This feature helps in investigating an incident by providing a clear, time-based view of actions that took place on the system. It’s essential for understanding the progression of an attack and determining the attack’s start and end points.

Containment
Now that we have analyzed the incident and found the activity to be malicious, the next step is to isolate (contain) the compromised endpoint from the network. Isolating a compromised endpoint means disconnecting it from the rest of the network to stop the spread of an attack or further damage. The primary goal is to prevent the malware from spreading to other machines or endpoints on the network and prevent attackers from using the compromised machine to access other systems or steal sensitive data.
Click on Actions on the right side of the page and select Network Contain, as shown below.

Click on Contain host to isolate the victim host.

Best Practices for Malware Incident Analysis in CrowdStrike Falcon
- Regularly update detection rules to stay ahead of emerging malware threats.
- Enable real-time monitoring to detect malware as early as possible.
- Create detailed incident response playbooks to streamline your response process.
- Leverage threat intelligence to understand the broader context of the attack.
- Review system logs regularly to spot anomalies before they become full-fledged incidents.
Conclusion
By leveraging Falcon’s powerful tools, including real-time alerts, endpoint data, and behavioral analytics, security teams can swiftly identify malicious activity and assess the extent of the compromise. The step-by-step process, from incident detection, alert investigation, and threat analysis to containment and eradication, ensures the incident is contained while minimizing the risk of further damage. Ultimately, CrowdStrike Falcon empowers security professionals to act quickly and efficiently, providing valuable insights for immediate threat mitigation and long-term security improvements.
