Table Of Contents
How to Onboard a Device into Microsoft Defender for Endpoint
When securing your organization’s network, it is essential to ensure that all devices are protected by advanced endpoint security solutions like Microsoft Defender for Endpoint. This comprehensive security tool helps protect against diverse cyber threats, including malware, ransomware, phishing, and more. In this guide, I will walk you through the process of onboarding a new device into Microsoft Defender for Endpoint, ensuring seamless integration and robust protection.
Prerequisites
Before you begin the onboarding process, there are a few requirements you need to fulfill:
Network Connectivity: The device must have internet access to communicate with the Defender for Endpoint service.
Microsoft Defender for Endpoint Subscription: Ensure your organization has an active subscription to Microsoft Defender for Endpoint.
Admin Permissions: You need to have administrative rights in the Microsoft 365 Defender portal.
Supported OS Versions: Microsoft Defender for Endpoint supports a wide range of operating systems, including Windows 10, Windows 11, macOS, Linux, and mobile devices. Make sure your devices meet the system requirements.
Sign in to Microsoft Defender
Sign in to the Microsoft Defender portal with your global administrator or security administrator account.
Once logged in, In the left-hand side navigation pane, click on System > Settings > Endpoints.

Download the Onboarding Package
Click on Device management > Onboarding. Based on your organization’s needs, choose an operating system to onboard to Microsoft Defender. Choose the Connectivity type and Deployment method. For this example, I will choose Windows 10 and 11, Streamlined, and Local Script (for up to 10 devices). Click on the Download onboarding package button to download it.

Click on Device management > Onboarding. Based on your organization’s needs, choose an operating system to onboard to Microsoft Defender. Choose the Connectivity type and Deployment method. For this example, I will choose Windows 10 and 11, Streamlined, and Local Script (for up to 10 devices). Click on the Download onboarding package button to download it.
Extract the file, then right-click and click on Run as Administrator.

Press Y for yes to confirm and continue. Press any key to proceed.

Next, confirm if the installation was successful. To do this, open a Command Prompt window on the newly onboarded device. At the prompt, copy the command below and run it. The Command Prompt window will close automatically when done. This verifies that the device is properly onboarded and reported to the service.
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'Now login to Microsoft Defender to verify that the device was added successfully. On the left-hand side blade, click on Assets > Devices.

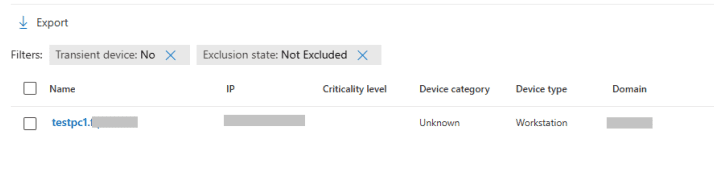
You should see your device listed, as shown in the screenshot below.
Conclusion
Onboarding a new device into Microsoft Defender for Endpoint is an essential step in ensuring your organization’s cybersecurity posture is strong and up-to-date. By following this guide, you can quickly onboard new devices into the system, apply necessary configurations, and continuously monitor them for threats.
