What is Nessus?
Nessus is a widely used vulnerability scanner that helps identify security weaknesses in systems, networks, and applications. It performs automated scans to detect vulnerabilities such as missing patches, misconfigurations, and potential security issues.
Understanding False Positives, False Negatives, True Positives, and True Negatives
Understanding these concepts is crucial for evaluating and improving security tools:
False Positives: A result indicating a vulnerability that does not actually exist. The scan reports a problem that, upon further investigation, proves to be non-existent or benign. Incorrectly flagged issues that don’t exist can lead to wasted resources and unnecessary remediation efforts. Reducing false positives helps streamline security operations and focus on genuine threats.
False Negatives: A situation where Nessus fails to detect an existing vulnerability. The scan does not identify a real issue that should have been flagged. Missed detections of real vulnerabilities can leave systems exposed. Minimizing false negatives is critical for maintaining effective security and ensuring that all potential threats are addressed.
True Positives: A valid detection where Nessus correctly identifies an actual vulnerability. Accurate identification of real vulnerabilities is essential for effective risk management and timely remediation. This helps ensure that actual threats are addressed promptly.
True Negatives: A correct assessment where Nessus accurately indicates the absence of a vulnerability, meaning no issue exists where none should be. Correctly identifying the absence of vulnerabilities helps validate that systems are secure where no issues should be, supporting efficient resource allocation and confidence in the security posture.
Balancing these outcomes improves the reliability and efficiency of security tools, leading to a more accurate assessment of risks and better overall protection. Now that you understand these concepts, let’s handle a false positive in Nessus.
Handling False Positives in Nessus
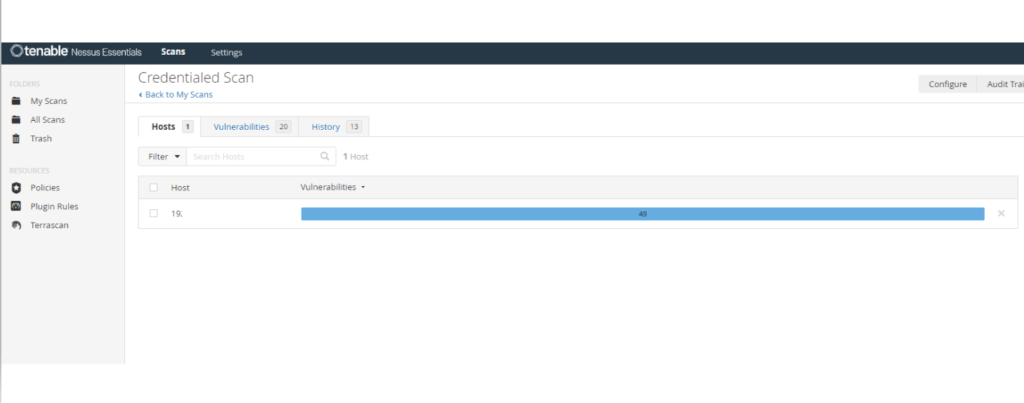
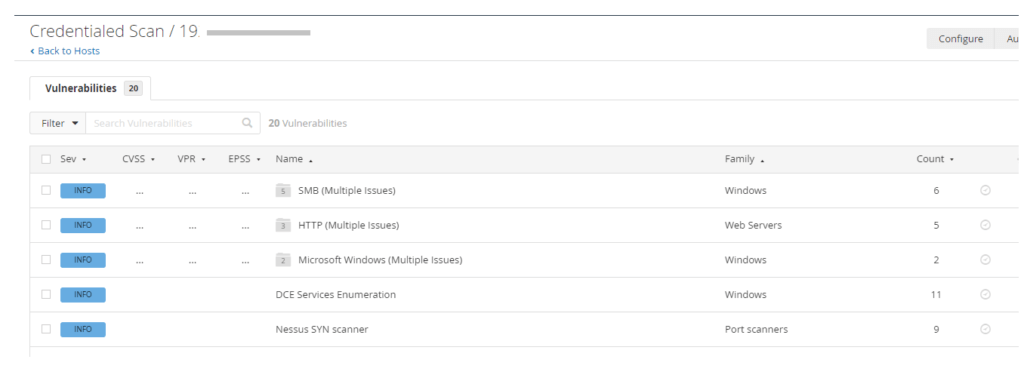
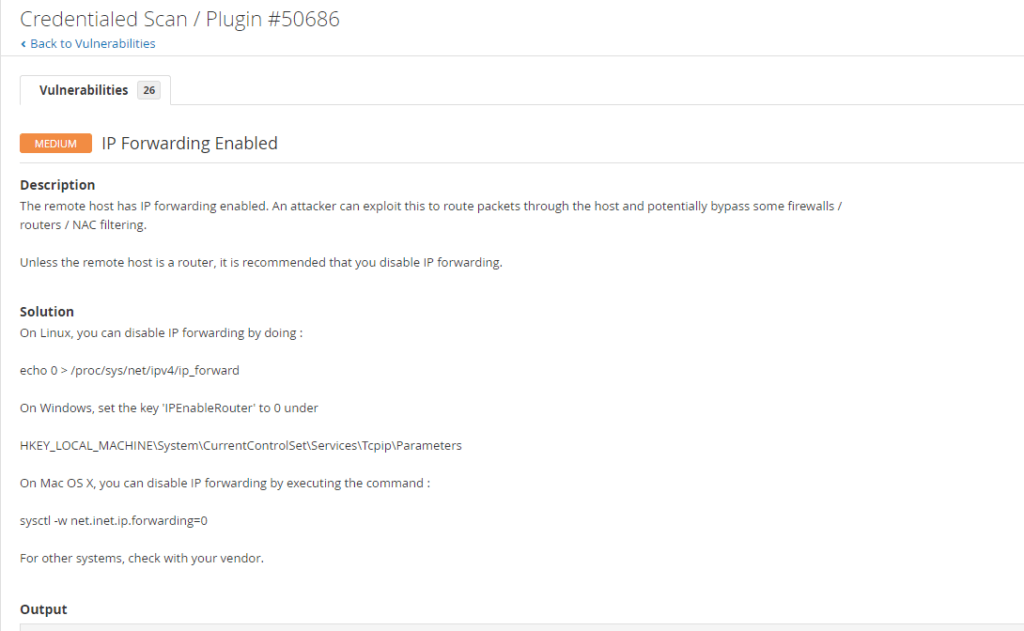
We have a false positive to address from our previous Nessus lab. Click here to learn How to Analyze Nessus Vulnerability Scan Result. as shown in the screenshot below. First, you need to take note of the plugin ID and the target IP address. For this example, the Plugin ID is 50686, and let’s say the IP is 192.168.30.01. So get the Plugin ID 50686 and your target IP address or addresses ready.
Before handling a false positive, all results must be reviewed and validated through manual verification of findings by cross-checking Nessus findings with other tools or by manually inspecting them to confirm whether they are true vulnerabilities. You can also consult vendor documentation, threat intelligence feeds, or security advisories to verify the validity of the identified issues.
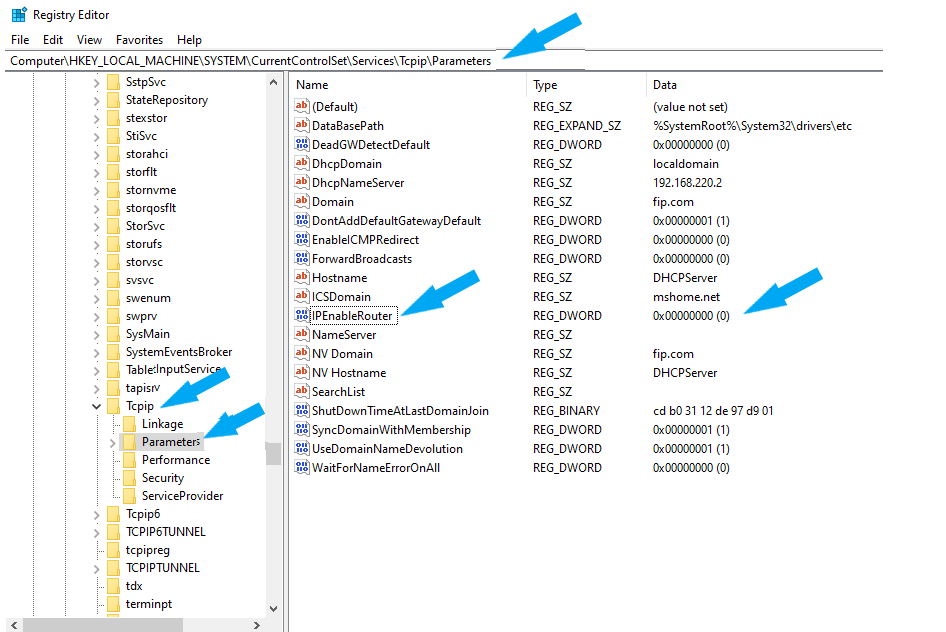
For this example, I logged into the target system, navigated to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters, and located IPEnableRouter. The IPEnableRouter was disabled (0), as shown in the screenshot below. I only confirmed the vulnerability and didn’t make any changes.
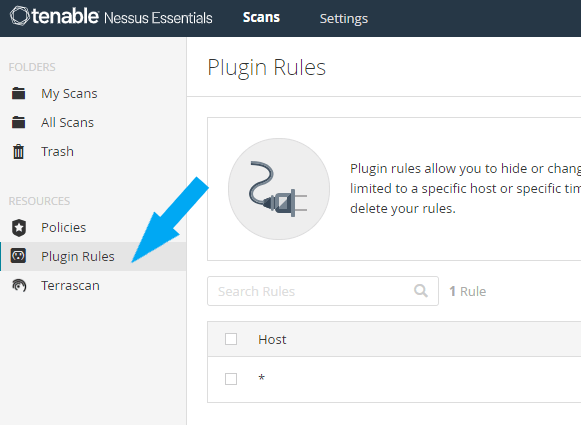
Now, we will create a plugin rule that hides the false positives from our future scans. In your Nessus account, click on Plugin Rules on the left pane.
Click the blue New Rule button on the top right below your username, as shown below.
In the Host field, type in your target IP address or addresses. In the Plugin ID field, type in your Plugin ID.
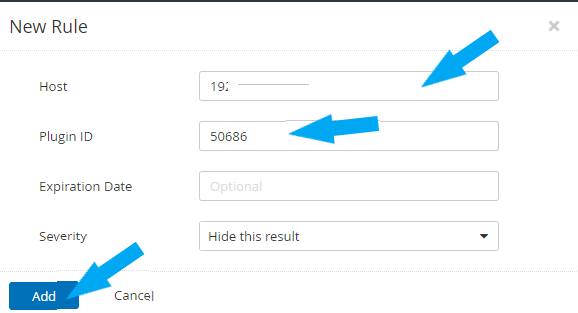
You have the option to set an Expiration Date if you want; I am leaving it as default for this example.
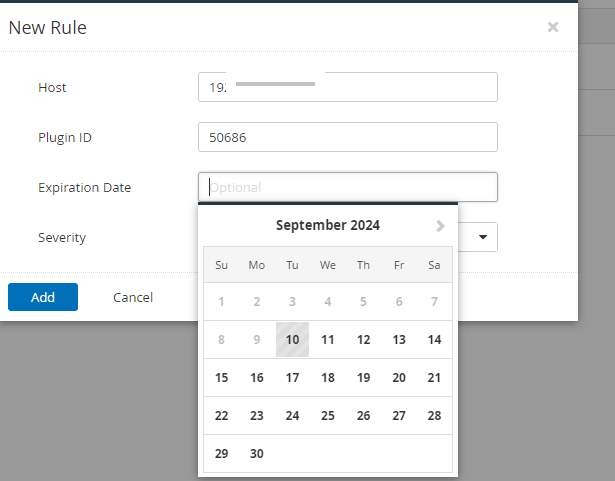
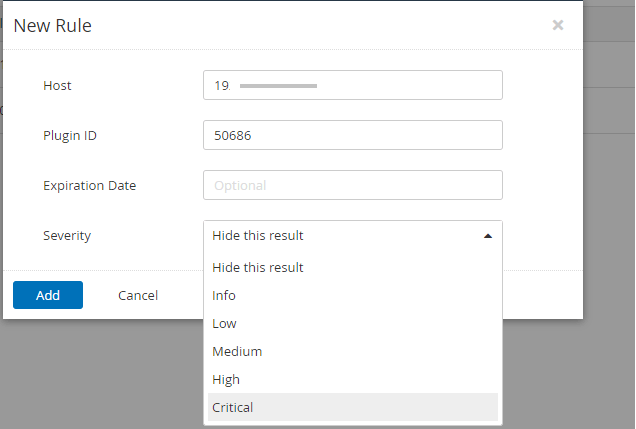
Click on the Severity drop-down, and select the severity I am leaving as default for this example, as shown below. Click the Add button
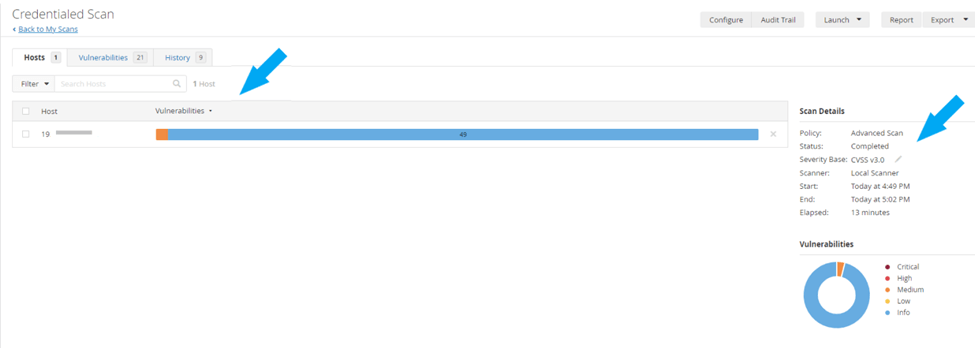
The next thing to do is to perform another scan to verify the update. Relaunch the previous scan or create a new scan using the same scanning method, such as a credentialed scan or a non-credentialed scan on the same target host.
Credentialed Scans use valid credentials (like usernames and passwords) to access and scan the system. Accesses internal components for a thorough vulnerability assessment scan systems behind firewalls or in secure networks, which non-credentialed scans might miss, and provides the most accurate result.
Non-credentialed scans conduct scans without accessing systems directly, simulating an external attack. Does not need valid credentials, reducing setup complexity and security risks. Provides less accurate results, which might lead to less actionable findings.
The new credentialed scan has been completed on the same host, and the false positive no longer appears in the scan result. See the screenshot below