Table Of Contents
- 1 Prerequisites
- 2 Understanding Nessus Vulnerability Assessment
- 3 Choosing Between Credentialed and Non-Credentialed Scans
- 4 Vulnerability Result Analysis
- 5 Understanding Vulnerability, Threat, And Risk
- 6 False Positives, False Negatives, True Positives, and True Negatives
- 7 Vulnerability Severity Rating
- 8 Understanding the Identified Vulnerabilities
- 9 Vulnerability Remediation
- 10 Post-Remediation Scan Result
- 11 About The Author
Prerequisites
There are prerequisites to this lab as listed below:
Step-by-Step Guide on Installing Nessus Essentials
Launch A Credentialed Scan in Nessus: Step-by-Step Guide
How to Create and Launch a Basic Network Scan in Nessus
How to Create and Launch a Host Discovery Scan in Nessus
Understanding Nessus Vulnerability Assessment
Nessus is a widely used vulnerability assessment tool designed to help organizations identify and address security vulnerabilities in their systems and networks. Developed by Tenable, Nessus scans systems for known vulnerabilities, misconfigurations, and other security issues.
In vulnerability assessment, Nessus supports two main types of scans: credentialed and non-credentialed. Each has its own advantages and limitations, depending on the level of detail required and the environment being assessed. Here’s a concise guide to understanding the differences between these two scanning approaches:
1. Credentialed Scans
Credentialed Scans use valid credentials (such as usernames and passwords) to access systems during the scan. This approach provides deeper insights into the system’s configuration and potential vulnerabilities. For example, A credentialed scan would be ideal for identifying vulnerabilities in an internal network or assessing detailed configuration settings on a web server where deeper insights are necessary for security assessment.
Advantages of Credentialed Scans
- Comprehensive Analysis: Provides a thorough assessment of vulnerabilities by accessing the system’s internal components. It can detect vulnerabilities that are not visible externally.
- Accurate Detection: Most accurately identifies configuration issues, missing patches, and other vulnerabilities that require internal access.
- Detailed Information: Allows for the retrieval of detailed system and application information, leading to more accurate and actionable findings.
- Better Coverage: Can scan systems behind firewalls and within secure internal networks, which non-credentialed scans might miss.
Disadvantages of credentialed scans
- Required Valid credentials: Admin credentials are needed to access systems, which involves additional setup and may pose security risks if credentials are compromised.
- System Performance: Accessing systems with credentials may affect performance or stability, though this is generally minimal.
- Potential False Positives: Even though a credentialed scan provides the most accurate result, the result sometimes includes false positives.
2. Non-Credentialed Scans
Non-Credentialed Scans do not use any credentials. Instead, they assess vulnerabilities based on what is accessible from an external perspective. For example, A non-credentialed scan is useful for testing the security of publicly accessible web applications or network services to determine what vulnerabilities an external attacker could exploit.
Advantages of Non-Credentialed Scans
- Simplicity: Easier to set up as it doesn’t require credentials or special access permissions.
- Replicates External Attacks: Simulates an attack from an external attacker’s perspective, providing insight into what a potential intruder might see or exploit.
- Lower Risk: The risk of impacting the system’s internal operations or configurations is less, as it does not involve logging into the systems.
Disadvantages of Non-Credentialed Scans
- Limited Scope: Provides a less detailed view, focusing mainly on external vulnerabilities and missing internal issues.
- Potential False Negatives: Some vulnerabilities, particularly those that are only visible internally or require specific configurations, may be missed.
Choosing Between Credentialed and Non-Credentialed Scans
Use Credentialed Scans When:
- You need a detailed assessment of internal vulnerabilities and configurations.
- You want to identify issues that require internal access, such as missing patches or insecure configurations.
- You are assessing systems that are not directly accessible from the outside (e.g., internal servers behind a firewall).
Use Non-Credentialed Scans When:
- You are interested in understanding what vulnerabilities are visible to external attackers.
- You prefer a simpler setup without needing to provide or manage credentials.
- You want to simulate an external attack scenario to evaluate your perimeter defenses.
Combining Both Approaches
For a comprehensive security assessment, it is often beneficial to use both credentialed and non-credentialed scans. This dual approach allows for a thorough examination of both external vulnerabilities and internal weaknesses, providing a complete view of your security posture. For example, A company might run non-credentialed scans to identify vulnerabilities accessible from the internet and credentialed scans to evaluate internal configurations and vulnerabilities that could be exploited once an attacker gains internal access. By understanding and effectively utilizing both credentialed and non-credentialed scans, organizations can better protect their systems and address vulnerabilities from multiple angles
Vulnerability Result Analysis
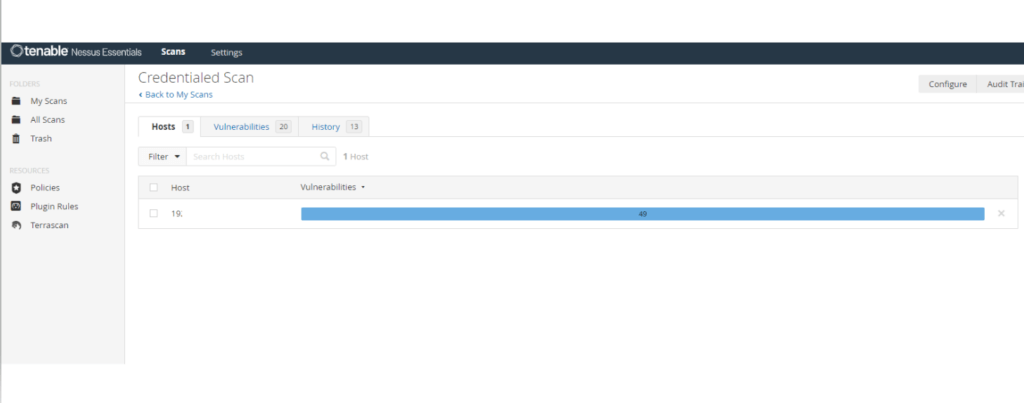
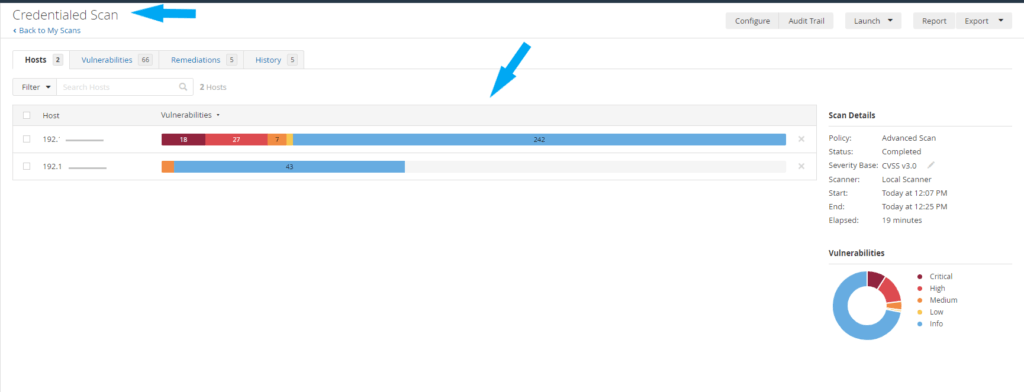
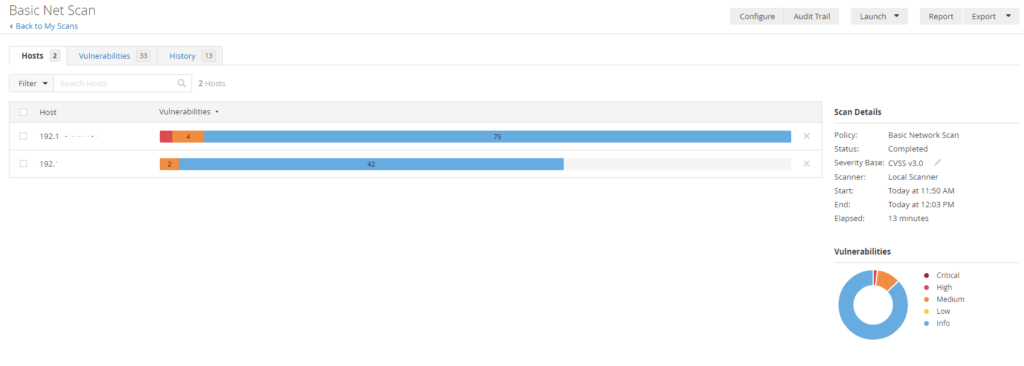
For this example, I performed both a credentialed scan and a non-credentialed scan on the same machines to compare the results, as shown in the screenshots below. Click here to learn how to launch a credentialed Scan in Nessus and here to learn how to launch a non-credentialed (Basic Network Scan) in Nessus. Your scan result dashboard should look similar to the screenshots below. Notice that the credentialed scan identified more vulnerabilities than the non-credentialed scan result.
Credentialed scan result
Non-credentialed scan result
Understanding Vulnerability, Threat, And Risk
In cybersecurity, the terms vulnerability, threat, and risk are often used interchangeably, but they have distinct meanings. Understanding these differences is crucial for effective risk management and security strategy development. Here’s a clear breakdown of each term:
1. Vulnerability: A vulnerability is a weakness or flaw in a system, application, or network that a threat actor could exploit to gain unauthorized access or cause harm. It is a specific issue within a system, such as a software bug, misconfiguration, or missing patch. For example, a software application with a buffer overflow vulnerability or an unpatched operating system that is vulnerable to known exploits. Weak passwords or default credentials. Identifying and addressing vulnerabilities is critical because they represent potential entry points for attackers. Regular vulnerability assessments help in discovering and mitigating these weaknesses before they can be exploited.
2. Threat: A threat is a potential cause of an unwanted incident that can result in harm to a system or organization. Threats exploit vulnerabilities to cause damage. A threat can be a person, group, or event that has the potential to exploit vulnerabilities. It is essentially an actor or event that has the capability and intention to cause harm. For example, cybercriminals or hackers aim to exploit vulnerabilities for financial gain, or malware like ransomware designed to exploit software flaws, natural disasters, or insider threats (e.g., employees with malicious intent). Understanding threats helps organizations anticipate potential attacks and develop strategies to protect against them. Threat intelligence and threat modeling are key to preparing for and defending against various types of threats. Click here to understand MITRE ATT&CK.
3. Risk: Risk is the potential for loss or damage when a threat exploits a vulnerability. It is the combination of the likelihood of a threat occurring and the impact it would have if it did. Risk is a measure of how vulnerabilities and threats interact to affect the organization’s assets and operations. It considers both the probability of an exploit and the potential consequences. For example, the risk of data loss from a ransomware attack exploiting an unpatched vulnerability and the risk of a data breach from an insider threat exploiting weak access controls. Managing risk involves assessing the likelihood and impact of threats exploiting vulnerabilities and implementing measures to mitigate or reduce this risk. Risk management strategies include applying patches, enhancing security controls, and developing incident response plans. Risk is often assessed using the formula: Risk = Threat x Vulnerability x Impact
False Positives, False Negatives, True Positives, and True Negatives
Understanding the concepts of false positives, false negatives, true positives, and true negatives is essential for evaluating the effectiveness of detection systems, such as vulnerability scanners, intrusion detection systems, and other diagnostic tools. Managing these outcomes helps improve the effectiveness of security tools and ensures a more accurate and efficient security posture. Here’s a breakdown of each term:
1. True Positive: A true positive occurs when a test or detection system correctly identifies a vulnerability or threat that is genuinely present. The system correctly detects a real issue. For example, a vulnerability scanner identifies a known security flaw in software that has indeed been found and confirmed to exist. True positives are crucial because they represent effective and accurate detection of actual vulnerabilities or threats, allowing for timely and appropriate responses.
2. True Negative: A true negative occurs when a test or detection system correctly identifies the absence of a vulnerability or threat that is not actually present. The system correctly determines that no issue exists when there is none. For example, A vulnerability scanner does not flag a system as vulnerable when it is, in fact, secure and free of the assessed vulnerabilities. True negatives are important because they indicate that the system is correctly avoiding false alarms and is accurately assessing the absence of issues.
3. False Positive: A false positive occurs when a test or detection system incorrectly identifies a vulnerability or threat that does not actually exist. The system mistakenly flags a non-issue as a problem. For example, a vulnerability scanner reports a system as vulnerable to a certain exploit when it is not actually affected by that vulnerability. False positives can lead to unnecessary alarms and may cause security teams to waste resources investigating non-existent issues. Reducing false positives is crucial for maintaining efficiency and focusing on real threats.
4. False Negative: A false negative occurs when a test or detection system fails to identify a vulnerability or threat that is actually present. The system overlooks or fails to detect an existing issue. For example, a vulnerability scanner does not identify a known vulnerability in a system that is indeed affected, leading to a potential security risk going unnoticed. False negatives are problematic because they mean that real threats or vulnerabilities are not being detected, which can leave systems exposed and unprotected.
Practical Examples
- True Positive: A firewall correctly identifies and blocks a malicious IP address attempting to breach a network.
- True Negative: An antivirus software accurately reports that a particular file is clean and free of malware when it actually is.
- False Positive: An intrusion detection system flags normal network traffic as malicious due to an overly sensitive rule.
- False Negative: A vulnerability scanner fails to detect a critical security flaw in a software application that it should have identified.
Impact on Security Practices
- Accuracy and Reliability: Systems with high rates of true positives and true negatives are generally more reliable and effective.
- Resource Allocation: Reducing false positives helps avoid unnecessary investigations while minimizing false negatives helps ensure that no real threats are missed.
- Continuous Improvement: Regularly refining detection tools and methodologies helps improve accuracy and reduce both false positives and false negatives.
For this example, I am analyzing the result of the credentialed scan performed on Windows Server 2022 (DHCP Server in my lab environment). Click on the result to view the vulnerabilities. See the screenshots below.
Vulnerability Severity Rating
Security issues or vulnerabilities are often categorized by their severity to prioritize remediation efforts. These categories are Critical, High, Medium, Low, and Info. It’s important to prioritize based on the severity as it helps organizations focus their resources on the most pressing issues. Here’s a breakdown of what each severity level typically represents:
1. Critical: Issues that pose an immediate and severe threat to the organization’s security. They often involve vulnerabilities that could be exploited remotely and with minimal user interaction, leading to a full compromise of systems or data. For example, Unpatched zero-day vulnerabilities, critical flaws in network-facing services, and severe misconfigurations that expose sensitive data.
2. High: Serious issues that present a significant risk but may require more effort or specific conditions to exploit compared to Critical issues. These vulnerabilities can lead to a substantial impact if exploited. For example, Vulnerabilities that allow privilege escalation, severe flaws in internal applications, and significant security weaknesses in public-facing services.
3. Medium: Issues that present a moderate risk. These vulnerabilities typically require certain conditions to be exploited and may result in less severe impacts compared to Critical or High issues. For example, Vulnerabilities in non-critical applications, configurations that could be exploited under specific conditions, and issues that require multiple steps to exploit.
4. Low: Issues that present a minimal risk to the organization. These vulnerabilities typically require a combination of factors to be exploited and result in minimal impact. For example, Minor security flaws in less critical applications, configurations that have limited exposure, and low-impact vulnerabilities in internal tools.
5. Info (Informational): Issues that do not represent a direct threat but provide useful information about the system’s configuration or security posture. These are typically not vulnerabilities but rather observations that can help with security hardening. For example, Information about unused services, details on configuration settings, and non-critical issues that do not directly affect security.
Qualitative Severity Ratings
The CVSS score is categorized into qualitative severity ratings, as listed below. Click here to Understand Vulnerability and CVE.
9.0 – 10.0: Critical
7.0 – 8.9: High
4.0 – 6.9: Medium
0.1 – 3.9: Low
None (0): Info
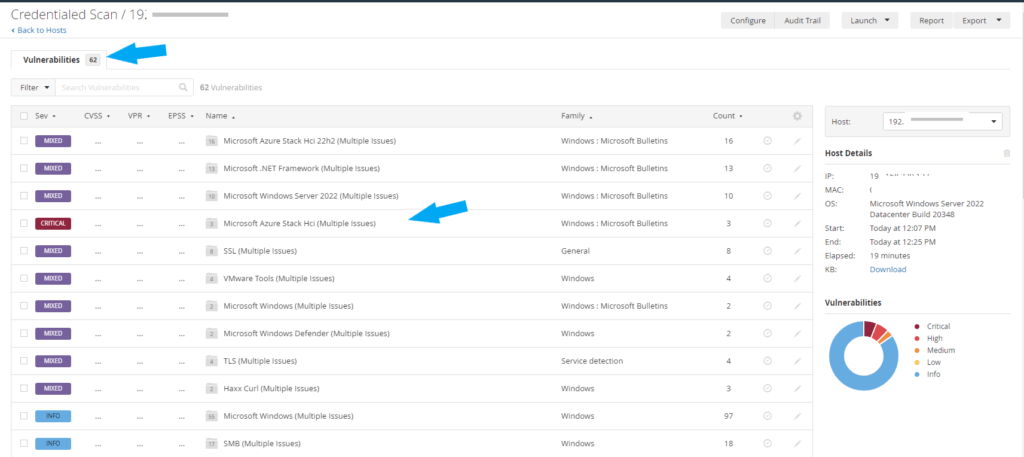
In a vulnerability management program, Critical and High vulnerabilities are usually prioritized for immediate remediation due to their potential for severe impact. For this example, I will click on critical; the CVSS rating is 9.8, as shown in the screenshot below.
Note: Your result may look different from mine. These machines are intentionally made vulnerable for practice purposes.
Click one more time for more details. Here, you will get more details about the vulnerability, including the description, solution, and CVE number. You can look it up to verify the vulnerability or click the See Also link.
Understanding the Identified Vulnerabilities
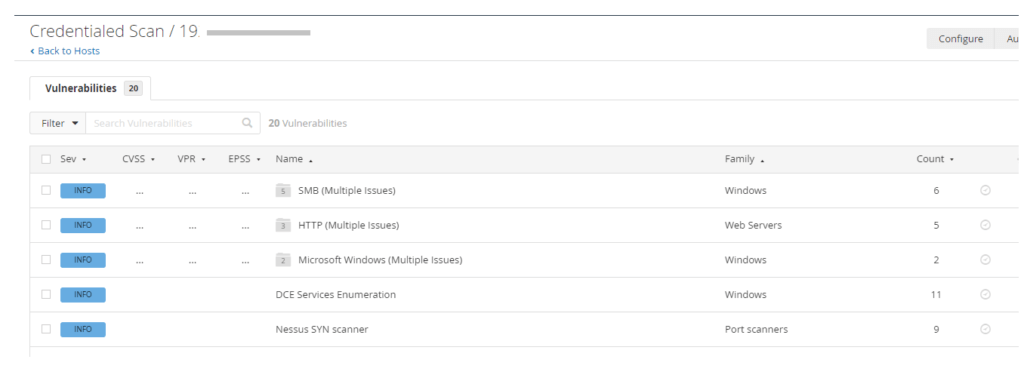
Five vulnerabilities were identified by the Nessus scanner, as listed below. We are going to classify each vulnerability and assess the risks.
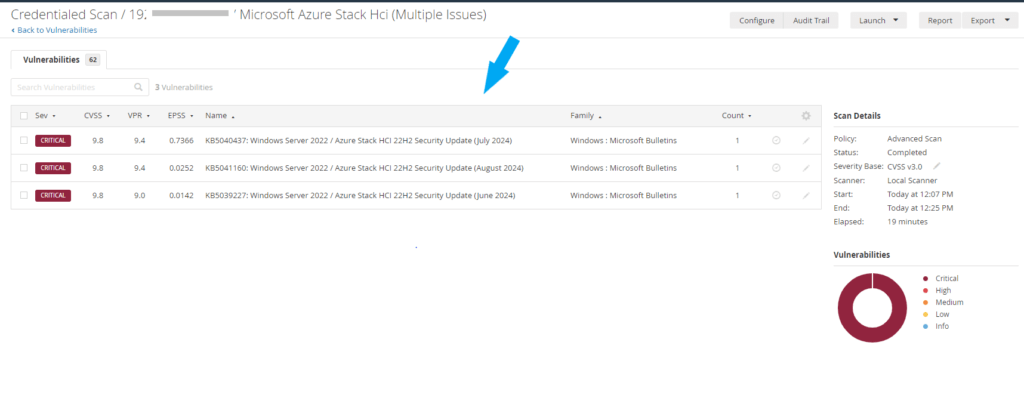
1. Missing Updates: The first vulnerability has to do with missing updates. This is a true positive, and the severity is critical.

Critical – KB5039227: Windows Server 2022 / Azure Stack HCI 22H2 Security Update (June 2024)
Description
The remote Windows host is missing security update 5041160. It is, therefore, affected by multiple vulnerabilities
Critical – KB5040437: Windows Server 2022 / Azure Stack HCI 22H2 Security Update (July 2024)
Description
The remote Windows host is missing security update 5041160. It is, therefore, affected by multiple vulnerabilities
Critical – KB5041160: Windows Server 2022 / Azure Stack HCI 22H2 Security Update (August 2024)
Description
The remote Windows host is missing security update 5041160. It is, therefore, affected by multiple vulnerabilities
Solution
Apply Security Update 5040437
2. Cipher Suites Strength: The second vulnerability has to do with Cipher Suites Strength. This is a true positive, and the severity is High.
Click on Mixed and then click on High for more details about the high-severity vulnerability identified.
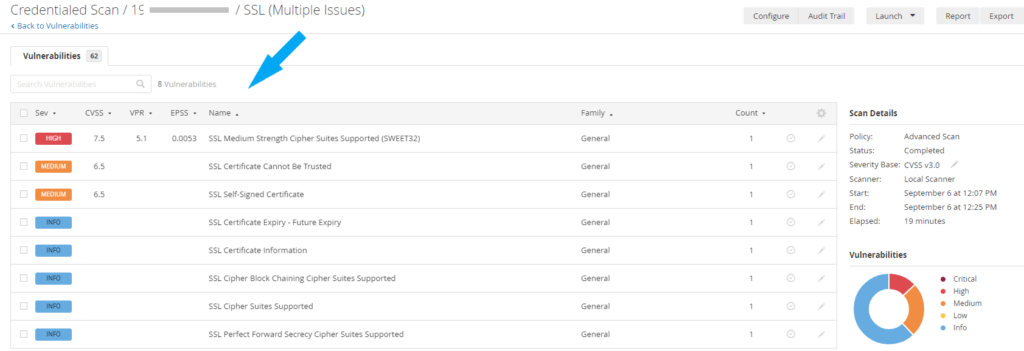
Here, you will get more details about the vulnerability, including the description, solution, and CVE number. You can look it up to verify the vulnerability or click the See Also link.
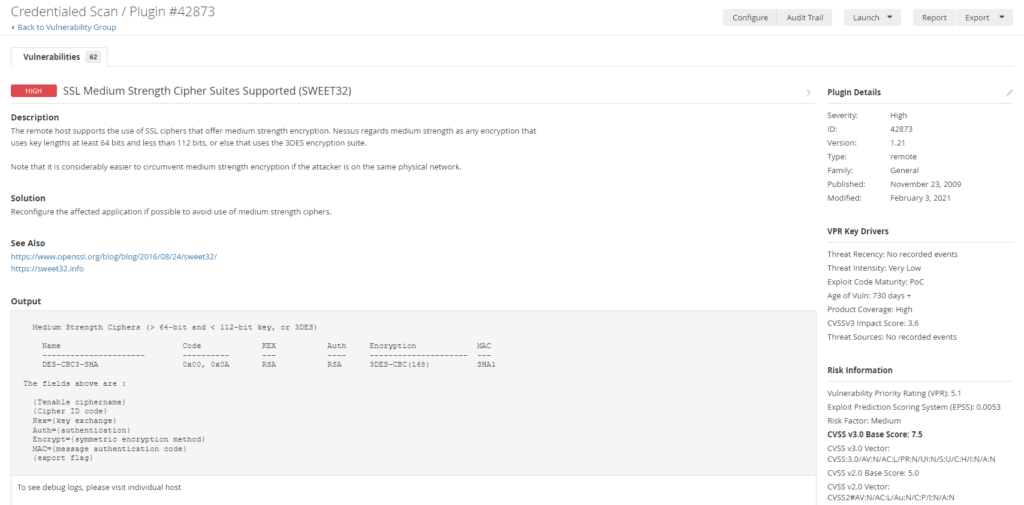
High – SSL Medium Strength Cipher Suites Supported (SWEET32)
Description
The remote host supports the use of SSL ciphers that offer medium strength encryption. Nessus regards medium strength as any encryption that uses key lengths at least 64 bits and less than 112 bits, or else that uses the 3DES encryption suite.
Solution
Reconfigure the affected application if possible to avoid use of medium strength ciphers.
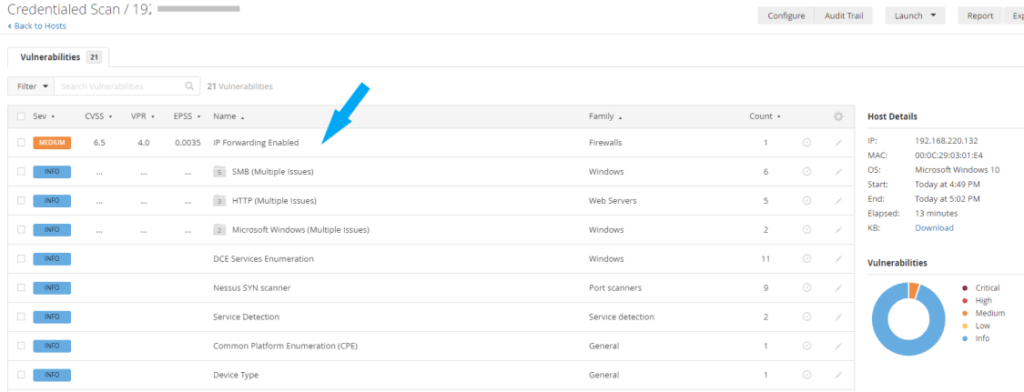
3. IP Forwarding: The third vulnerability has to do with IP Forwarding. This is a false positive, and the severity is Medium.
Click on Mixed and then click on Medium for more details about the medium-severity vulnerability identified. Here, you will get more details about the vulnerability, including the description, solution, and CVE number. You can look it up to verify the vulnerability or click the See Also link.
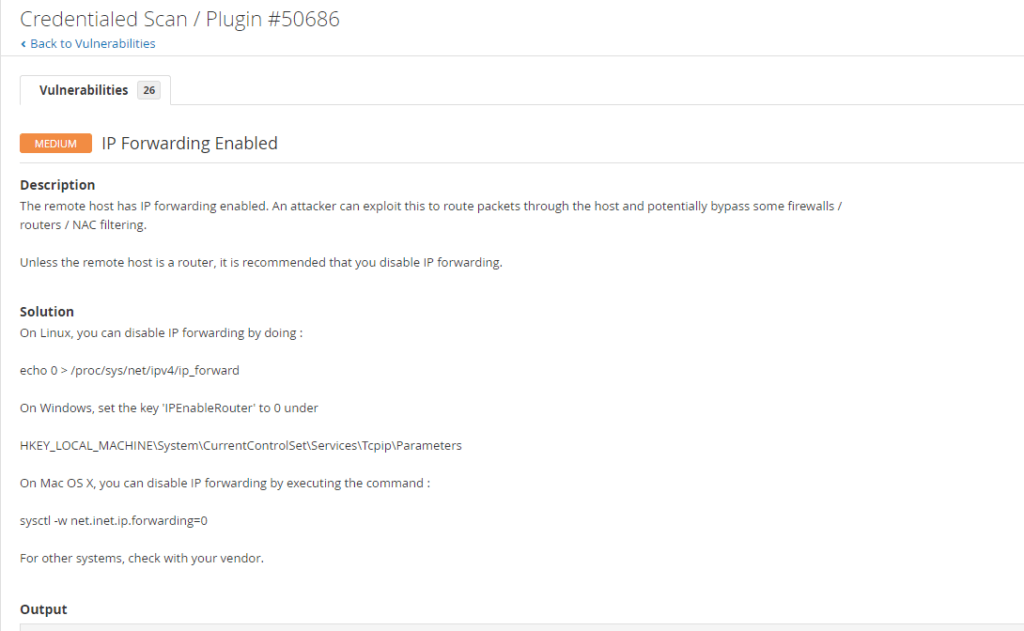
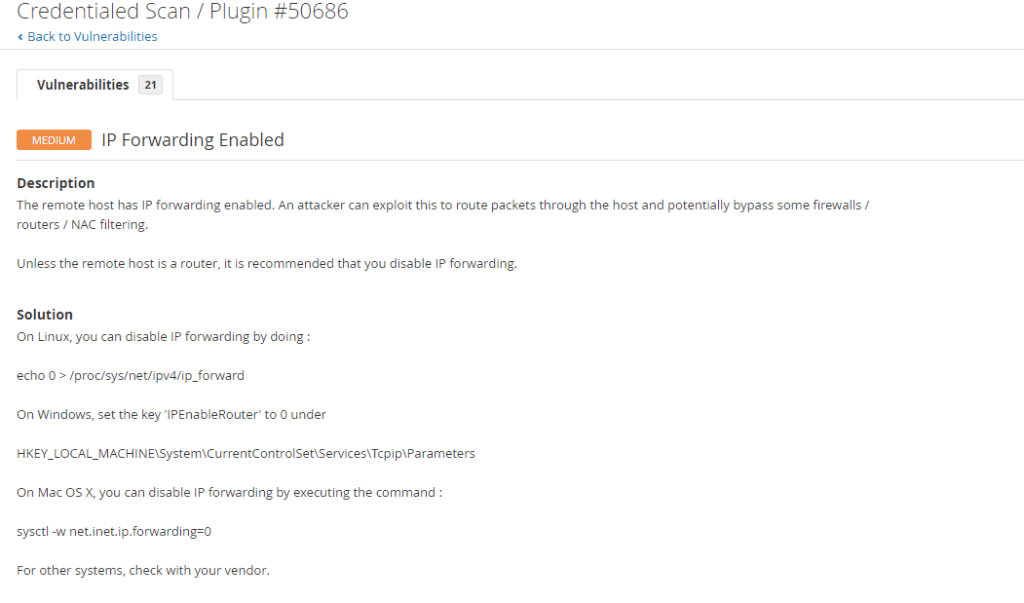
Medium – IP Forwarding Enabled
Description
The remote host has IP forwarding enabled. An attacker can exploit this to route packets through the host and potentially bypass some firewalls / routers / NAC filtering.
Solution
Unless the remote host is a router, it is recommended that you disable IP forwarding. HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters.4. SMB Signing: The fourth vulnerability has to do with SMB Signing. This is a true positive, and the severity is Medium.
Click on Mixed and then click on Medium for more details about the medium-severity vulnerability identified. Here, you will get more details about the vulnerability, including the description, solution, and CVE number. You can look it up to verify the vulnerability or click the See Also link.
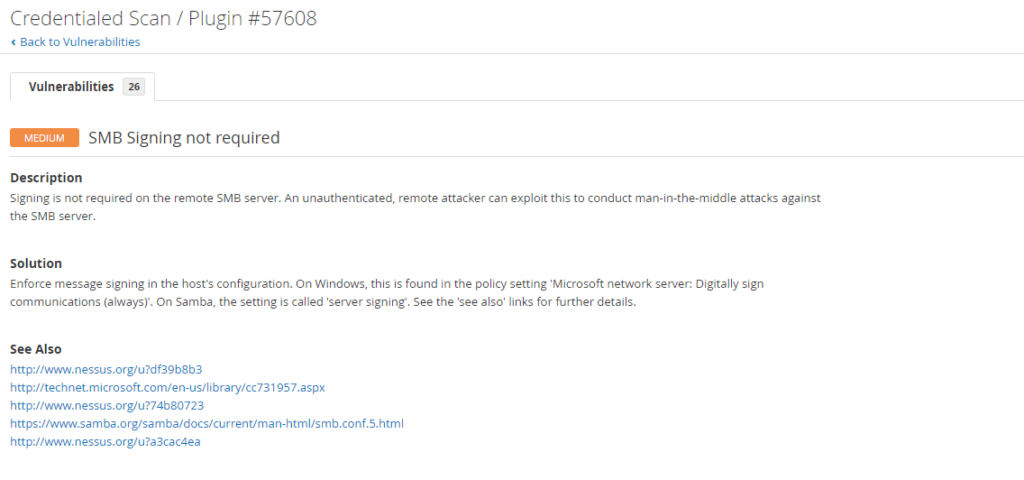
Medium – SMB Signing not required
Description
Signing is not required on the remote SMB server. An unauthenticated, remote attacker can exploit this to conduct man-in-the-middle attacks against the SMB server.
Solution
Enforce message signing in the host’s configuration. On Windows, this is found in the policy setting ‘Microsoft network server: Digitally sign communications (always)’. On Samba, the setting is called ‘server signing’. See the ‘see also’ links for further details.
5. Deprecated TLS Protocol Version: The fifth vulnerability has to do with the Deprecated TLS Protocol Version. This is a true positive, and the severity is Medium.
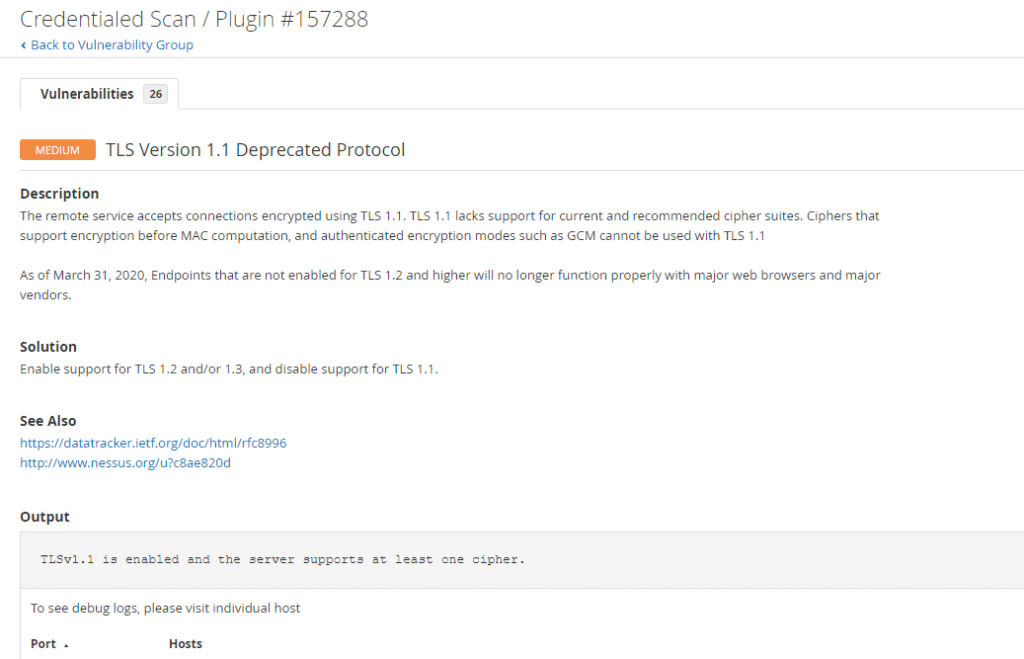
Medium – TLS Version 1.1 Deprecated Protocol
Description
The remote service accepts connections encrypted using TLS 1.1. TLS 1.1 lacks support for current and recommended cipher suites. Ciphers that support encryption before MAC computation, and authenticated encryption modes such as GCM cannot be used with TLS 1.1 As of March 31, 2020, Endpoints that are not enabled for TLS 1.2 and higher will no longer function properly with major web browsers and major vendors.
Solution
Enable support for TLS 1.2 and/or 1.3, and disable support for TLS 1.1.
Vulnerability Remediation
Next, we are going to remediate the identified vulnerability and then rescan the system.
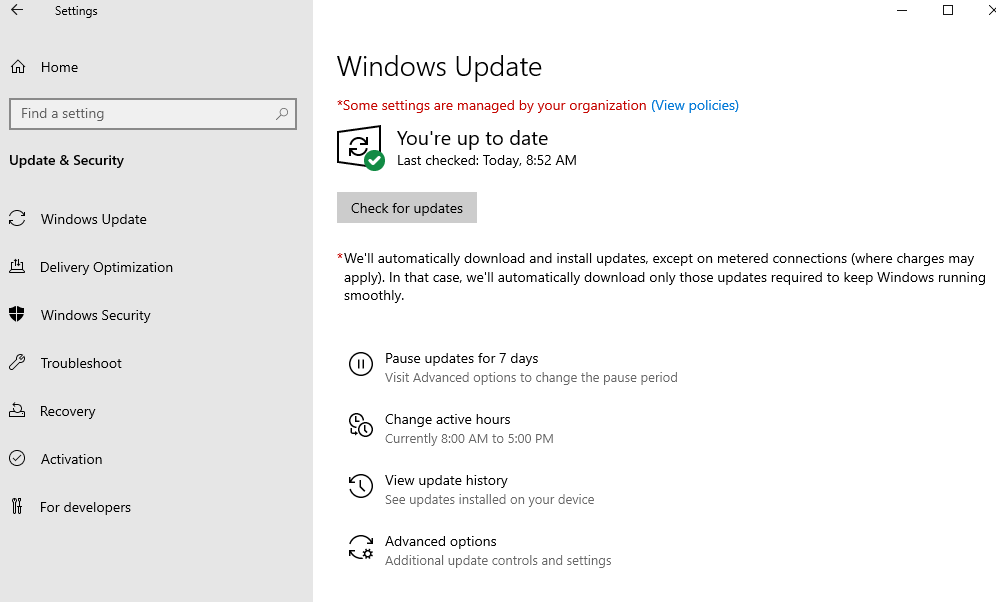
1. To remediate the first vulnerability (Missing Updates), we need to update the system. Click on Settings > Update & Security > Check for Updates > Install now> Restart.
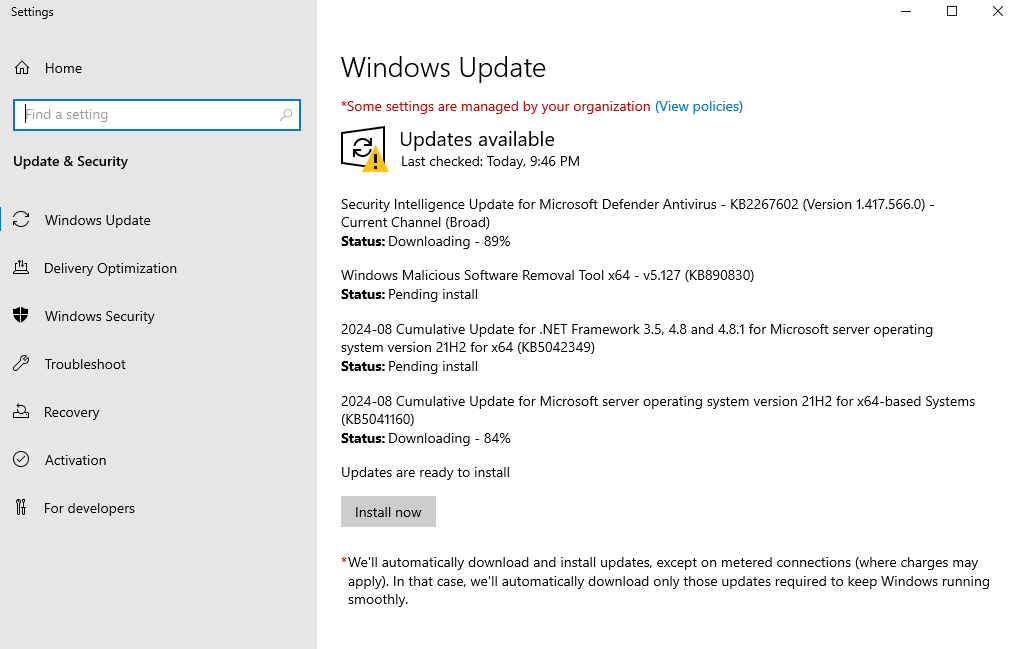
The server has been updated and restarted, as shown in the screenshot below.
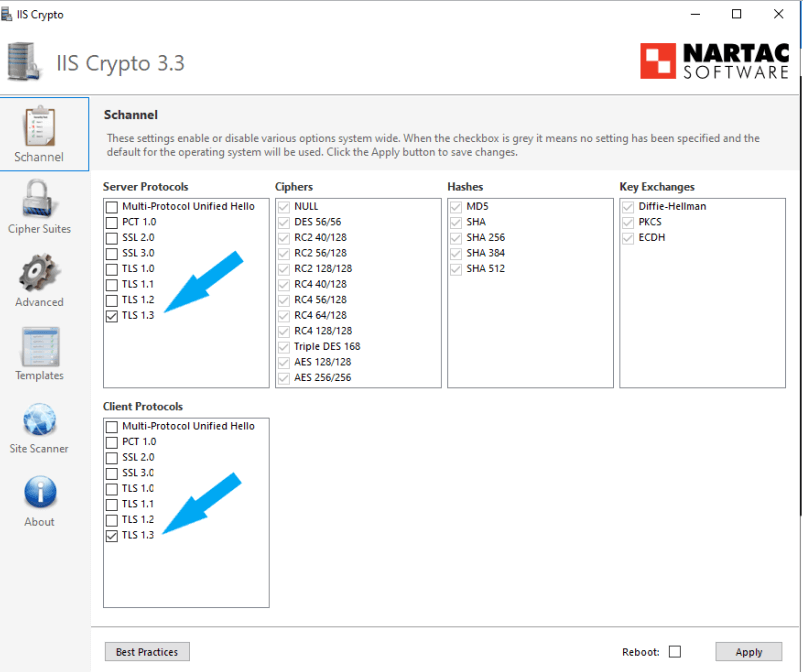
To remediate the second (Cipher Suites Strength) and the fifth (Deprecated TLS Protocol Version) vulnerabilities, We are going to enable the TLS 1.3 protocol for both the server and the client and disable older protocols. Click here to learn How to Enable TLS 1.3 on Windows Server 2022 With IIS Crypto. Click here for a Step by Step Guild to Enabling TLS 1.3 on Windows Server 2022 With Registry Editor. See the screenshot below.
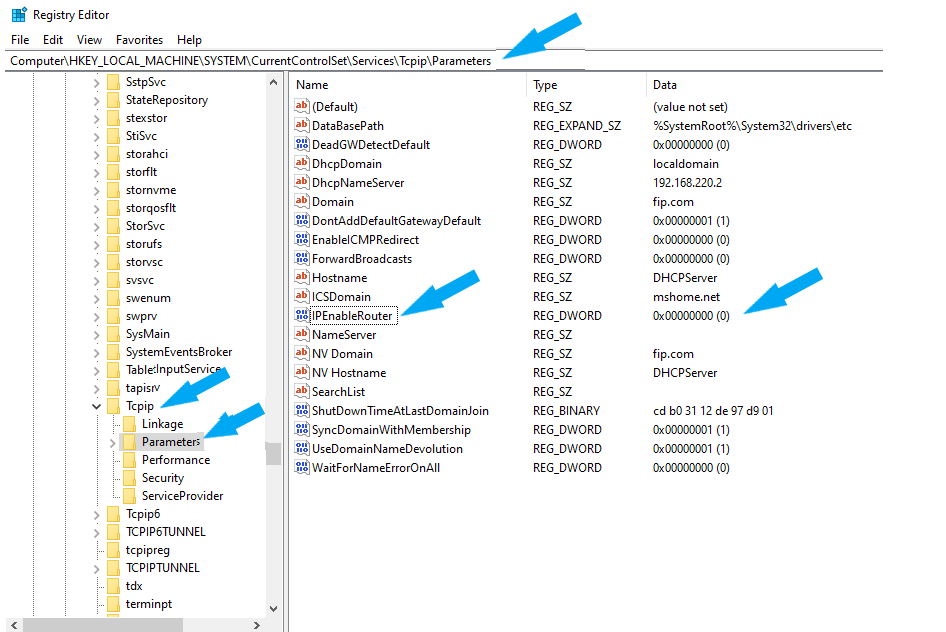
3. To remediate the third vulnerability (IP Forwarding), the IP forwarding must be disabled. This third vulnerability was a false positive for me as the IPEnableRouter was disabled (0), as shown in the screenshot below. I only confirmed the vulnerability and didn’t make any changes. Navigate to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters and locate IPEnableRouter. Change the value to (0) if enabled.
3. To remediate the fourth vulnerability (SMB Signing), we must enable SMB Signing. Click here to learn how to enable SMB Signing. SMB Signing has been enabled, as shown below.
Post-Remediation Scan Result
After all the identified vulnerabilities have been remediated, we need to launch another credentialed scan on the same host. See the screenshot below for the result.
Note: Your target machine IP address may change after a reboot if using DHCP. So remember to adjust your target IP address or addresses as needed or set up a static IP address on the target machine.
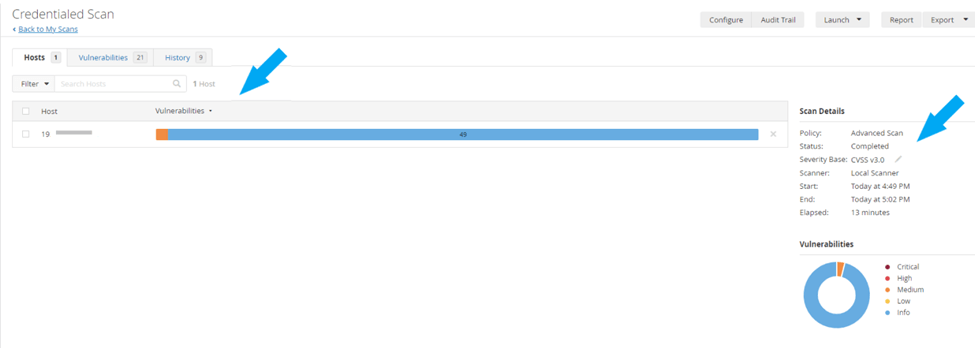
The only vulnerability left is the third vulnerability (IP Forwarding Enabled), as shown in the screenshot below, and it was a false positive.
Next, we need to address the identified false positive so it stops showing up in our future scans. Click here to learn How To Address False Positives in Nessus.
After addressing the false positive, we need to rescan to verify the changes. See the screenshot below.