What is Windows Defender Firewall?
The Windows Defender Firewall serves as an integrated security component in Windows, safeguarding your computer against entry and potential threats posed by software attempting to infiltrate via the internet or local network.
How does Windows Defender Firewall work?
Windows Defender Firewall monitors the traffic coming in and out of your system and decides whether to allow or block traffic based on predefined rules. Windows Defender Firewall acts as a barrier, blocking unauthorized access and keeping your system safe. For example, If a hacker or malware tries to sneak into your computer through the internet. It not only protects you from threats coming from the outside but also helps manage communication between different programs on your computer. It ensures that only safe and authorized connections are allowed, preventing malicious programs from spreading or accessing sensitive information. You can create rules to allow specific programs or services to communicate over the network while blocking others. This gives you control over what enters and leaves your computer.
In the search box, type Control Panel.
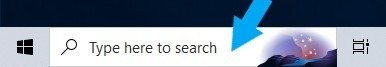
Then click Control Panel.
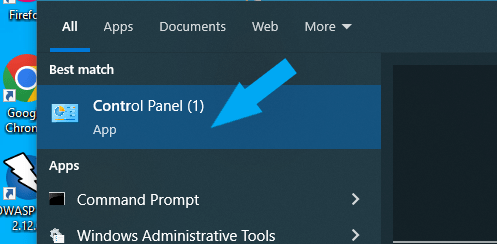
To easily locate Windows Defender Firewall, change your “view by” on the top right to small icons
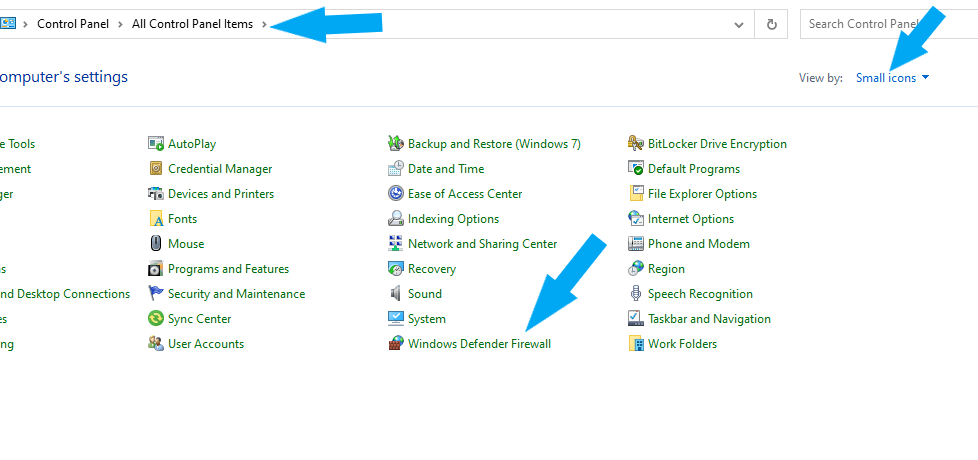
Click Windows Defender Firewall > Turn Windows Defender Firewall on or off.

Check the radio button next to Turn off Windows Defender Firewall (not recommended) under Domain Network Settings. Check the radio button next to Turn off Windows Defender Firewall (not recommended) under Private Network Settings. Check the radio button next to Turn off Windows Defender Firewall (not recommended) under Public Network Settings. Then click the OK button to save the changes.
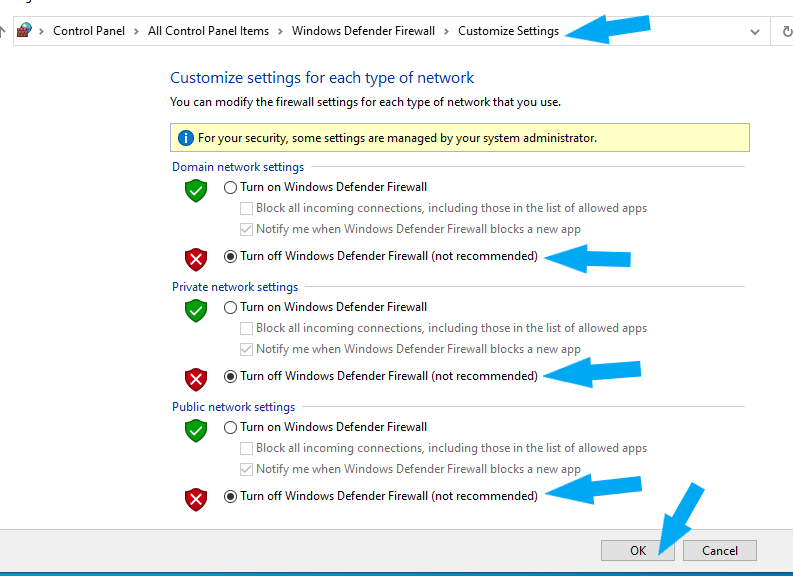
Windows Defender Firewall was successfully turned off. Your screen should look similar to the screenshot below.
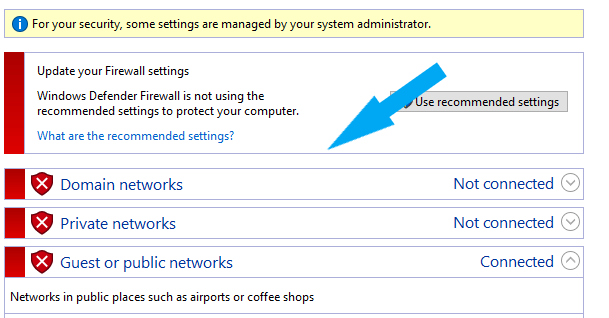
Conclusion
While it is not recommended to turn off Windows Defender Firewall for security purposes, you may need to do so in some situations, such as when you are trying to bypass the firewall for testing purposes. Or trying to set up a vulnerable machine for practicing penetration testing/ vulnerability scanning in your lab environment.
