Table Of Contents
A Comprehensive Guide to Securing Your Azure VM Using Azure Bastion
In today’s digital age, securing your cloud infrastructure is paramount. When running virtual machines (VMs) on Azure, it is essential to ensure that they are protected from unauthorized access and cyber threats. One powerful tool for enhancing Azure security is Azure Bastion. In this blog post, we’ll explore how Azure Bastion can help you secure your Azure VMs, allowing a seamless and secure connection to your resources without exposing them to the public internet.
What is Azure Bastion?
Azure Bastion is a fully managed platform-as-a-service (PaaS) that provides secure and seamless RDP (Remote Desktop Protocol) and SSH (Secure Shell) connectivity to your Azure VMs. Unlike traditional methods, where you expose your VMs directly to the public internet via an IP address, Azure Bastion ensures that no inbound public IP addresses are required to access your virtual machines. This eliminates the attack surface for your VMs, enhancing the overall security of your cloud environment.
Why Use Azure Bastion?
- Improved Security: Azure Bastion eliminates the need to expose your VMs to the public internet by providing a private, secure connection. It uses an encrypted connection for RDP and SSH access, ensuring that your VMs are safe from external threats. With Azure Bastion, your virtual machines are protected behind a firewall, and the only access points are Azure Bastion, which is tightly integrated with Azure security features.
- Simplified Access: Azure Bastion simplifies the access process by allowing you to connect to your VMs directly from the Azure portal without the need for additional client software. This is convenient for administrators and teams managing cloud infrastructure.
- No Public IPs Required: You don’t need to assign public IP addresses to your VMs, reducing the risk of direct attacks from the internet. Azure Bastion manages all the inbound and outbound traffic to your VMs through the Azure portal, further strengthening your security posture.
- Seamless User Experience: With Azure Bastion, users can access VMs securely from any device or location without the complexity of VPNs or additional configurations.
How to Secure Azure VM Using Azure Bastion
Let’s walk through the steps to set up Azure Bastion and secure your Azure VMs.
Create a Virtual Network (VNet)
Before using Azure Bastion, you need a virtual network where your Azure VMs reside. If you don’t already have a VNet, follow these steps to create one:
Log in to the Azure portal with your admin credentials. In the search bar, type Virtual Network and select it from the list.
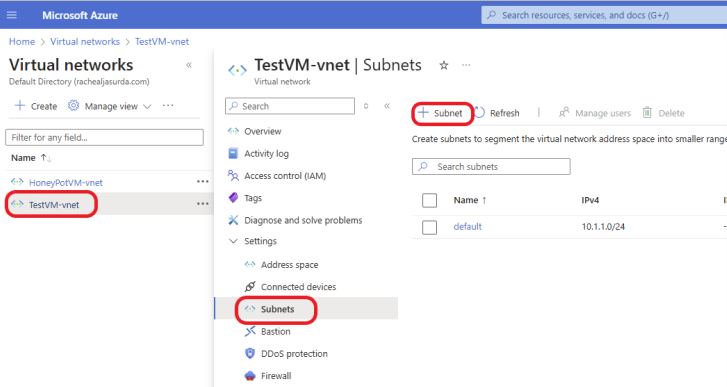
Click on the VNet to which you want to associate the Azure Baston. Click on the + Subnet tab at the top to create a new subnet.
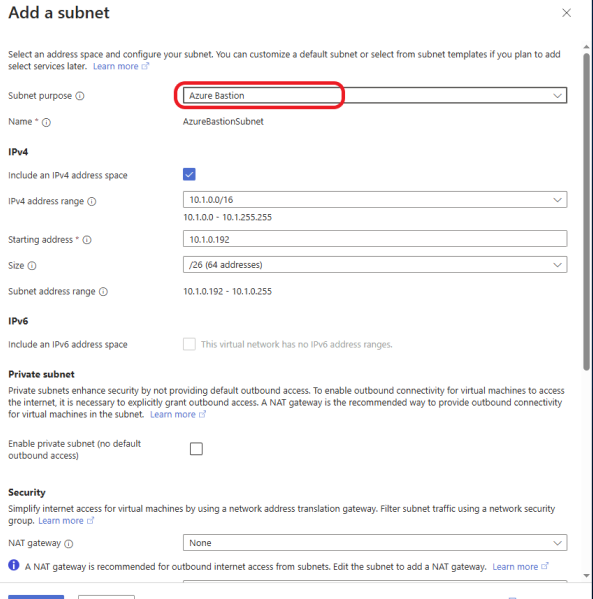
For Subnet purposes, select Azure Bastion. Azure Bastion requires a subnet called AzureBastionSubnet with at least a /26 address space. The default meets the requirements. Click on the Create button.
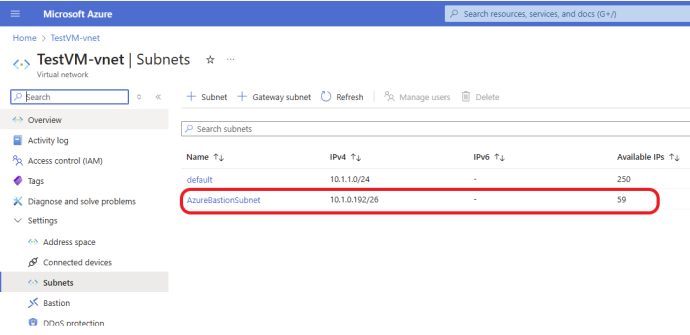
The subnet was created successfully, as shown in the screenshot below. Notice that the subnet is named AzureBastionSubnet by default.
Set Up Azure Bastion
Once you have your virtual network in place, you can create an Azure Bastion resource:
In the Azure search bar, type in marketplace and select it from the list.
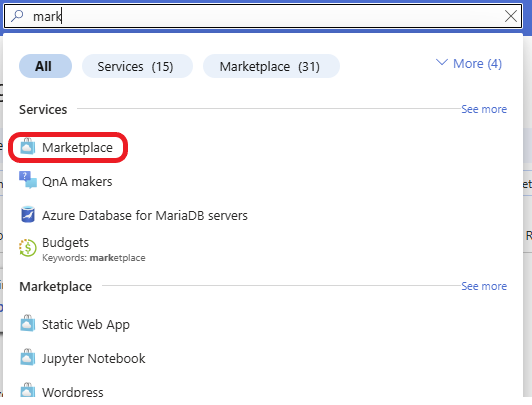
In the Azure Marketplace, search for Bastion. On the Bastion by Microsoft, click on Create, then select Bastion.
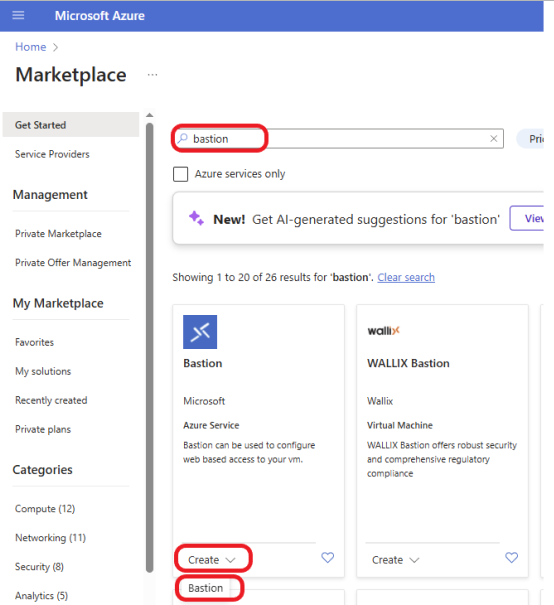
Choose the Subscription and Resource Group where you want to deploy Bastion. Select the Region where your VNet is located. Select the tier based on your organization’s needs. Click here to learn more about Azure Bastion SKUs. Under Virtual Network, choose the VNet where your VMs are deployed and select the subnet created earlier. Click on the Review + create button.
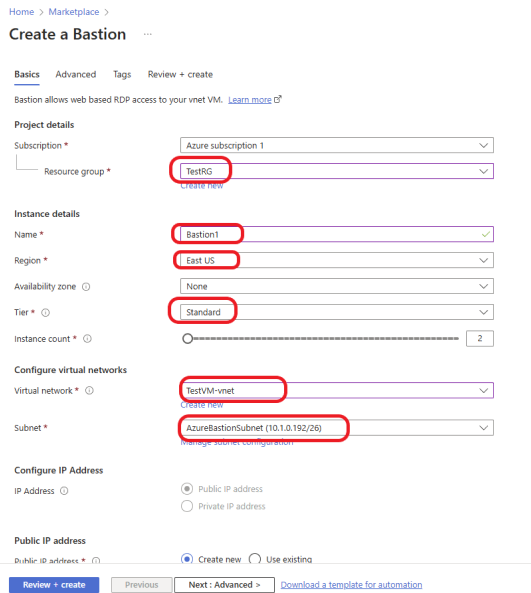
Review and click on the Create button.
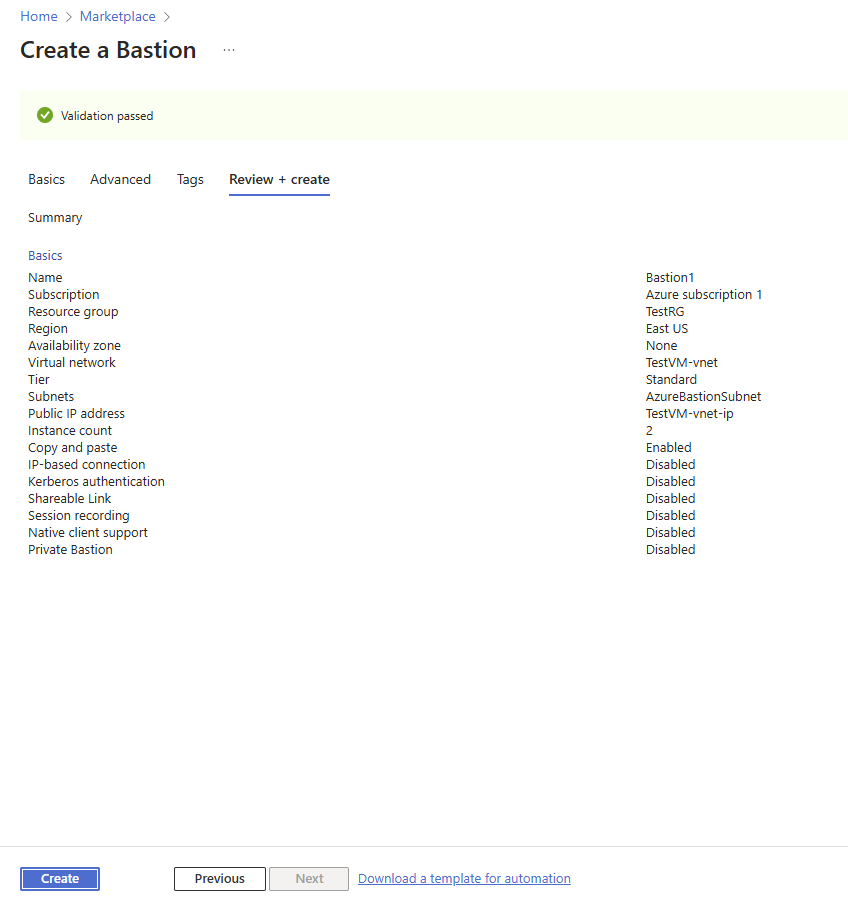
The Bastion was successfully deployed. Click on Go to resource.
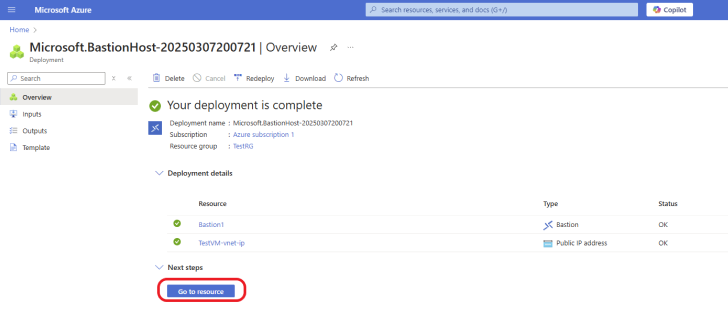
Configure Azure Bastion to Connect to Your VM
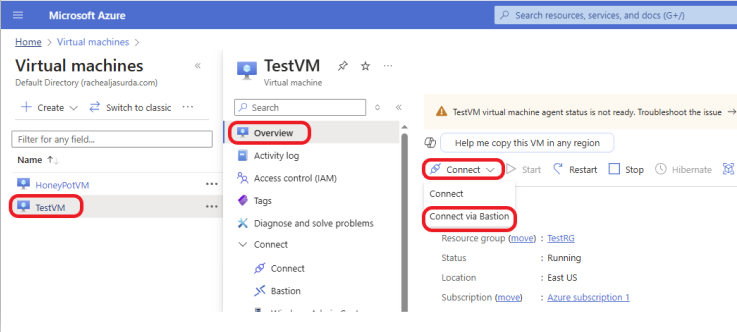
Once Azure Bastion is deployed, you can connect to your VMs using the following steps:
Navigate to the Virtual Machines section in the Azure portal. Select the VM you want to connect to. Click on Connect, and under the Connect button, select Bastion. Azure Bastion will establish a secure RDP or SSH session, and you can interact with your VM without any additional configuration.
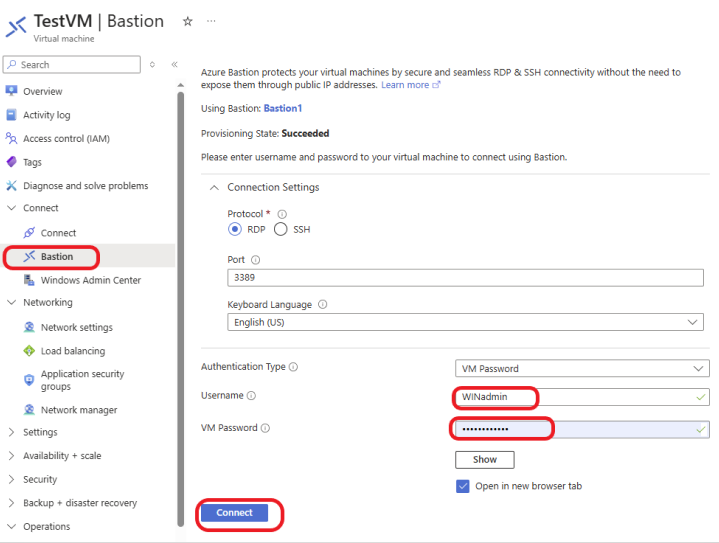
Enter your VM username and password or SSH key (depending on your authentication method). Click Connect to initiate the connection. When you click on Connect, it opens in a new window. Make sure to allow popups.
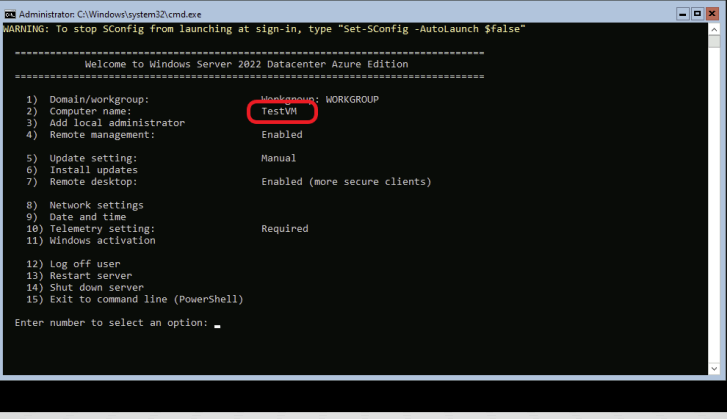
I was able to successfully log in via Bastion, as shown below.
Best Practices for Securing Azure VMs with Azure Bastion
- Use Strong Authentication: Always use multi-factor authentication (MFA) and strong passwords for Azure AD accounts accessing your VMs. Consider using Azure AD join for seamless identity management.
- Limit Access: Use Azure Network Security Groups (NSGs) and Role-Based Access Control (RBAC) to restrict who can connect to your VMs via Bastion. Only allow trusted users or admins access to critical systems.
- Regularly Update Your VMs: Keep your virtual machines and operating systems up to date with the latest security patches to avoid vulnerabilities.
- Use Just-in-Time (JIT) VM Access: Enable JIT access to restrict RDP/SSH access to VMs to specific time windows. This ensures that access is only available when necessary, further reducing exposure.
- Monitor Activity: Continuously monitor user activity and set up alerts for any unauthorized access attempts or unusual behavior.
Conclusion
Securing your Azure virtual machines is crucial to prevent cyberattacks and unauthorized access. Azure Bastion offers a secure, seamless, and easy-to-use solution to protect your VMs by eliminating the need for public IPs and exposing your resources to the internet. By following the steps in this guide, you can significantly enhance the security of your Azure environment, streamline your access management, and ensure that your cloud infrastructure remains safe.
