Table Of Contents
Analyze a Brute Force Attack in Microsoft Sentinel
A brute force attack is one of the most common methods that attackers use to gain unauthorized access to systems. It involves trying multiple combinations of usernames and passwords until the correct one is found. Detecting and responding to such attacks promptly is crucial to protecting your organization’s sensitive data. Microsoft Sentinel, a cloud-native SIEM (Security Information and Event Management) tool, provides robust capabilities to detect, investigate, and respond to security threats like brute force attacks. In this blog post, I will walk you through how to effectively investigate and analyze a brute force attack in Microsoft Sentinel.
Understanding Brute Force Attacks
Before diving into the steps to investigate a brute force attack, it’s important to understand what it entails. A brute force attack involves systematically trying all possible password combinations or username/password pairs until the correct one is discovered. These attacks can target various services, including Remote Desktop Protocol (RDP), VPNs, and other web applications.
Detecting Brute Force Attacks in Microsoft Sentinel
The first step in successfully investigating a brute force attack is to detect it. Sentinel uses advanced machine learning, analytics, and custom detection rules to identify potential brute-force attempts. Some common indicators of a brute force attack include:
- Unusual login attempts: A high number of failed login attempts in a short period of time.
- Geographic anomalies: Login attempts from unusual or high-risk regions.
- Credential stuffing patterns: Multiple login attempts using different usernames but the same password.
You can set up custom rules or leverage built-in analytics to detect these suspicious activities. In Sentinel, leveraging KQL (Kusto Query Language) queries for log data is a great way to identify brute force patterns. Click here to learn from the previous lab.
Investigating the Attack
When a brute force attack is detected, it’s time to investigate. Follow these steps to carry out a detailed analysis:
Review the Alert: Begin by reviewing the triggered alert. You should find information like:
- The source IP address of the attacker.
- The target account is being targeted.
- The timestamp of the failed login attempts.
- The number of failed attempts.
Use KQL Queries: Utilize Kusto Query Language (KQL) queries in Sentinel to examine logs and find further details. Below is an example KQL query to analyze failed login attempts:
SecurityEvent
| where EventID == 4625
| summarize Count = count() by IpAddressThis query identifies and counts the number of failed login attempts (EventID 4625) for each unique IP address in the SecurityEvent log. It helps in detecting potential brute force attacks or suspicious activities by tracking where failed logins are coming from. The result will provide a list of IP addresses with the corresponding count of failed login attempts. You can adjust the query based on your specific use case.
Explanation
1. SecurityEvent
- SecurityEvent refers to the table or dataset that contains security-related event logs. It typically includes events such as user logins, account lockouts, etc.
2. | where EventID == 4625
- This part filters the records to only include those where the EventID is 4625. In Windows security logs, EventID 4625 corresponds to a failed logon attempt. So, this filter ensures the query only processes failed logon attempts.
3. | summarize Count = count() by IpAddress
- The summarize function is used to aggregate data. Here, it counts the number of failed logon attempts (filtered in the previous step) and groups them by IpAddress.
- Count = count(): This counts the number of occurrences (failed logon attempts).
- by IpAddress: This groups the result by the IpAddress field, meaning the query will show how many failed logon attempts occurred from each IP address.

I left the honeypot created in the previous lab running for about 20 hours. And I got 27 Incidents created by Microsoft Sentinel. In this lab, I will walk you through step by step how to analyze brute force attack incidents in Microsoft Sentinel. Click here to learn how to create a honeypot and create a Sentinel alert rule.
First, it is important to address incidents based on their priorities. I am curious and can’t wait to see what is going on, especially the high-severity incident.

You can assign the incident to an analyst by clicking on the Actions tab at the top or clicking on unassigned by the right and then selecting the user you like to assign it to. For this example, I will assign the ticket to myself, as shown below. Click on the high-severity incident to learn about it. You can click on View full details.
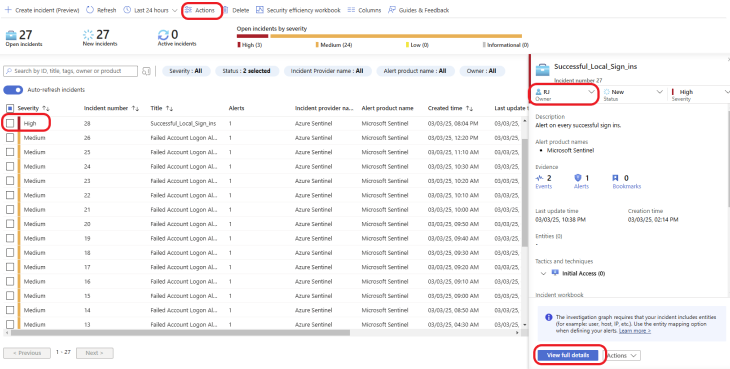
Notice that there are 2 events in this incident. You can scroll down to leave a comment in the comment section. Click on the 2 Events as shown below.

Click on the Right Arrowhead next to one of the 2 events to expand.
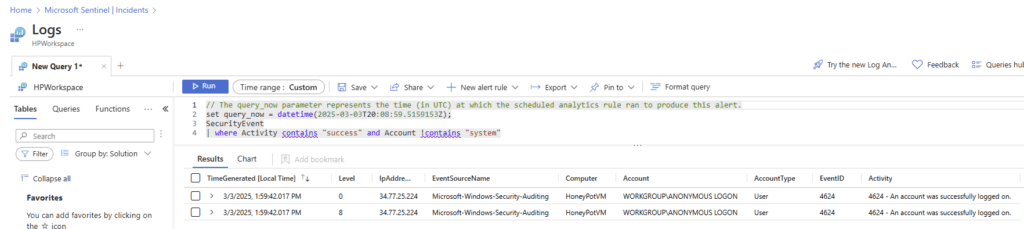
A successful login was made by an anonymous user on 3/3/2025 at 1:59:42.017 PM, with IP address 34.77.25.224 and Event ID 4624, as shown in the screenshot below.

Investigate the Source IP Address
Investigate the source IP address using threat intelligence data or external services like IP reputation databases (e.g., AbuseIPDB, VirusTotal, APIVoid) to check if the IP is associated with known malicious activity. Let’s check the reputation of the source IP address. Type in the Google search IP address reputation checker or click here. The attacker’s country is Belgium (BE), and the city is Brussels, though the hacker was using some form of VPN.

The IP address has 8 detection counts. The IP address was blocked by Engine, BitNinja, CRDF, ELLIO IP Feed, HoneyDB, IPSpamList IPsum, and S5hbl. Click on More Details to learn more.

VirusTotal’s report also shows that the source IP address is malicious.

Next, let’s analyze one of the incidents with medium severity. On the Microsoft Sentinel dashboard, click on Incident on the right menu. Click on the Medium severity incident to select it. Click on the Actions tab to assign the incident to an analyst.

For this example, I will assign the incident to myself, as shown below. Click on the 2 Events to view the events.

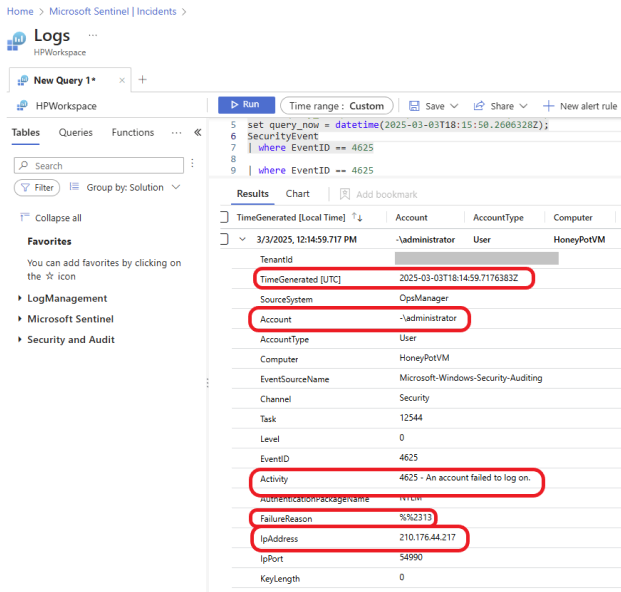
Notice there are 2 events in this incident. Click on the right arrow by the left to expand the event for details.

Here, we can see that the attacker tried to log In as an administrator on 03/03/2025 at 12:14:59.717 PM local time with IP address 210.176.44.217. FailureReason is %%2313, which means an unknown username or bad password. Event ID 4625, Activity 4625 An account with failed log-on.
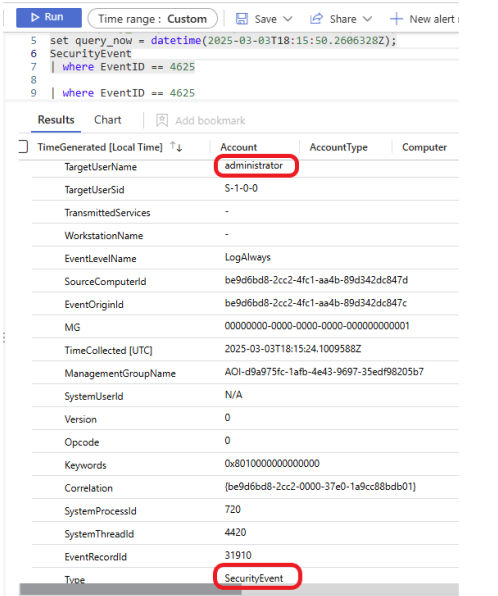
This is a security event, and the targeted username was administrator.
The attack was from Taiwan, and there were 13 detection counts. The attacker wasn’t using a VPN, and the Internet Service Provider ISP is Telstra Global.

The IP address has been blocked by Engine, BitNinja, BlockedServersRBL, CI Army List, CRDF, ELLIO IP, Feed,IPSpamList,ISX.fr DNSBL, NUBI Bad IPs, Nginx Bad Bot Blocker, Peter-s NUUG IP BL, PlonkatronixBL, S5hbl, and USTC IP BL, as shown below.

In a production environment, it’s important to examine other logs, such as firewall logs, Microsoft Entra ID logs, or VPN logs, for any signs of suspicious behavior. Look for patterns like:
- Multiple accounts being targeted from the same IP address.
- Unusual locations that do not align with normal user behavior.
By following the steps outlined in this blog post, you’ll be equipped to effectively analyze and gather valuable insights that will support your team’s remediation efforts. Click here to learn how to respond to a brute-force attack on Azure VM.
